群里的老哥推荐了Game Of Active Directory这个靶机,说是把GOAD吃透了,AD这部分就吃透了。于是立马着手开始搭建。先把当前用的kali完整克隆一份,然后分配25G内存和200G硬盘(GOAD需要最低24G内存和120G硬盘)。为了搭建这个靶机连夜加购一根16G内存条。
分配好后开机使用sudo gparted分配扩展空间到主硬盘。
在kali上安装virtualbox 和 vagrant 及其插件
sudo apt install virtualbox
sudo apt update && sudo apt install vagrant
vagrant plugin install vagrant-reload vagrant-vbguest winrm winrm-fs winrm-elevated
把repo clone下来,运行:
git clone https://github.com/Orange-Cyberdefense/GOAD.git
cd GOAD
./goad.sh
设定ip范围和安装类型:
set_ip_range 192.168.0
set_lab GOAD # 可选GOAD/GOAD-Light/NHA/SCCM
install
然后就会自动开始安装。若出现ip范围不允许的问题,则可以在sudo vim /etc/vbox/networks.conf路径下创建文件,在文件里加上:
* 192.168.0.0/24
随后我又出现了该平台不支持虚拟化Intel VT-x的问题。使用这篇文章里的办法https://blog.csdn.net/qq_45301716/article/details/131782732。
先打开任务管理器->性能 查看虚拟化是否已启用
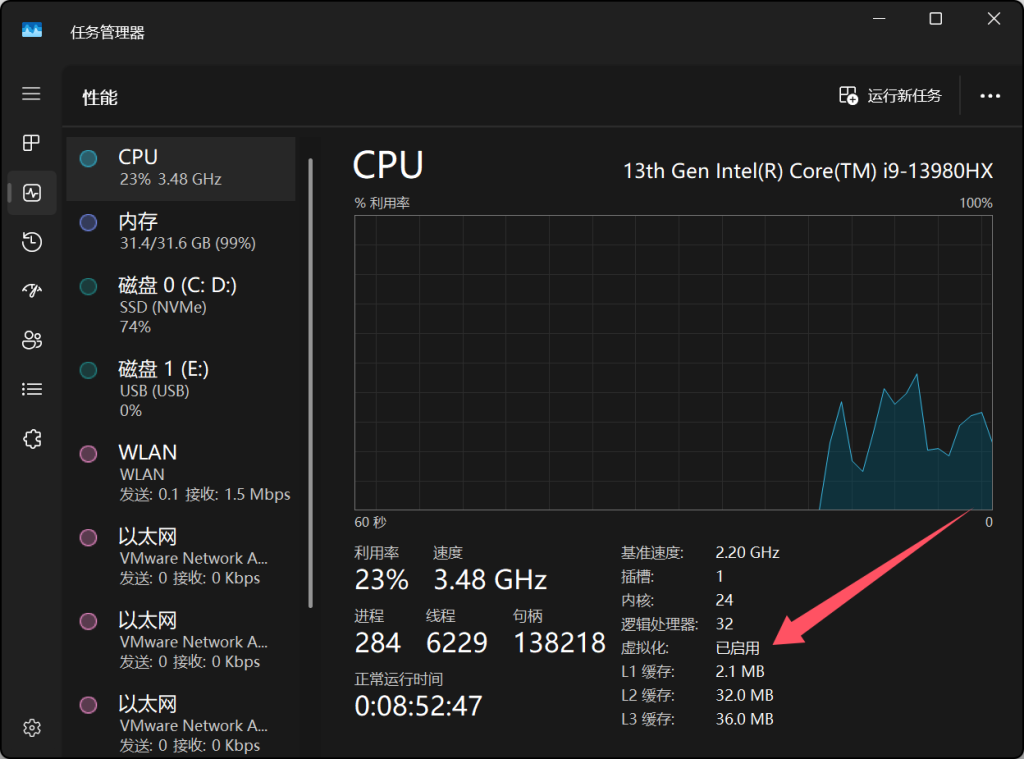
然后搜索框里搜索"启用或关闭Windows功能"
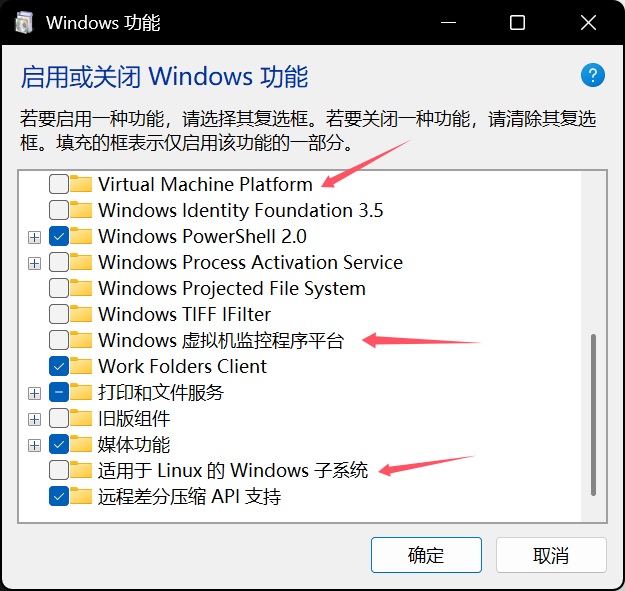
关闭 Hyper-V(若有),windows沙盒(若有),虚拟机平台, windows虚拟机监控程序平台, linux子系统。然后重启电脑。
管理员身份打开powershell或cmd,输入:
bcdedit /set hypervisorlaunchtype off
重启电脑后再次管理员身份打开powershell或cmd输入:
bcdedit /enum
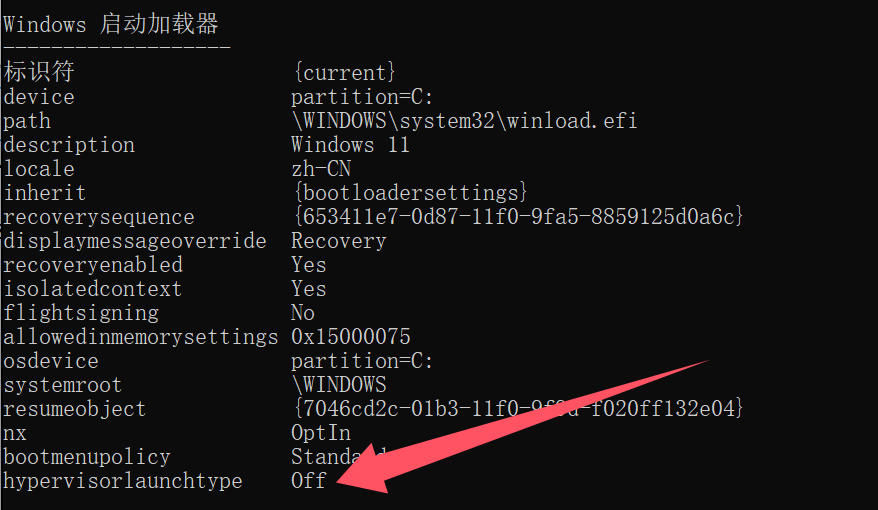
搜索框搜索“系统信息” 查看“基于虚拟化的安全性”是否已开启
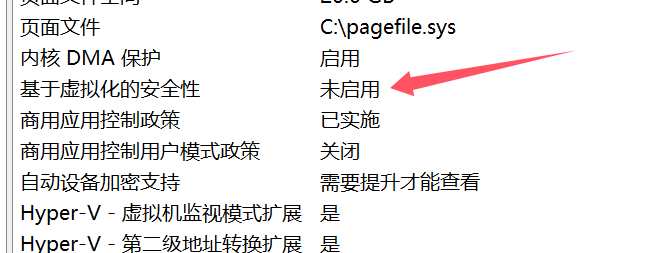
若显示开启,到设置->windows安全中心->设备安全性->内核隔离 关闭内核隔离
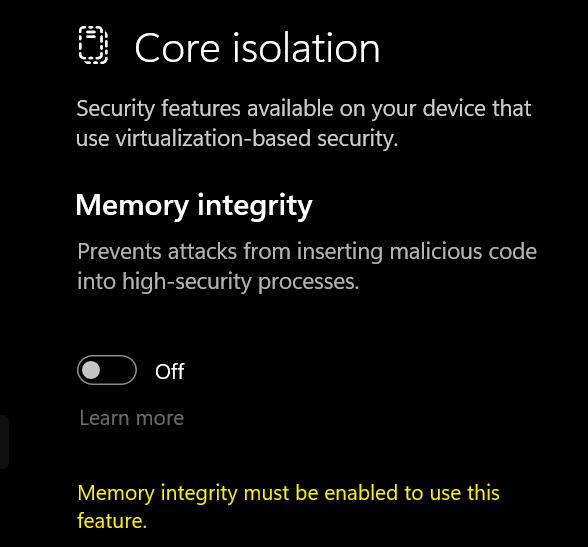
重启,查看系统信息基于虚拟化的安全是否已关闭。
然后在vmware中打开,设置->处理器->虚拟化引擎 勾选
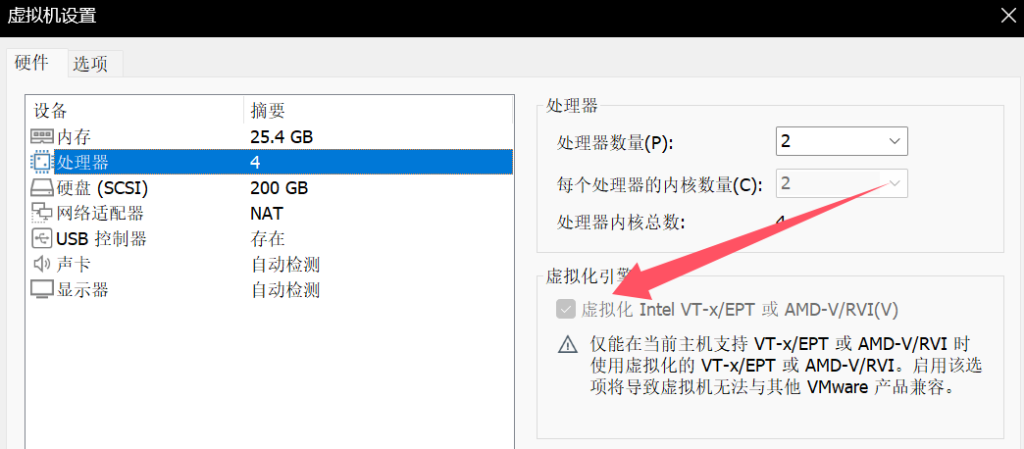
若没有这个选项,就去找当前虚拟机的.vmx文件,文本打开在最后加上一行:
vhv.enable = "TRUE"
保存,重启vmware,此时虚拟化引擎选项应该出现。
做完上面这些就可以开始安装了:
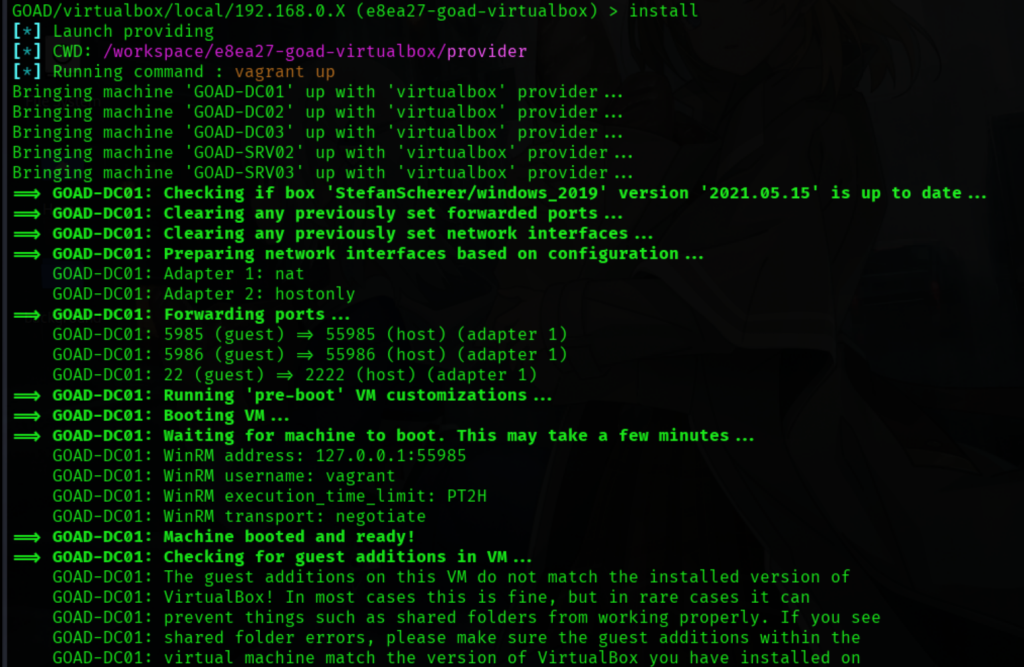
接下来就是漫长的等待。等部署好后尝试用fping测试各个机器:
fping -asgq 192.168.0.0/24 > result.txt
cat result.txt
192.168.0.1
192.168.0.10
192.168.0.11
192.168.0.12
192.168.0.22
192.168.0.23
没问题。再用nmap扫描一下端口:
sudo nmap -p- 192.168.0.1,10,11,12,22,23 -T4 --min-rate 2000 -Pn
Not shown: 65534 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
Stats: 0:00:10 elapsed; 1 hosts completed (6 up), 5 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 41.67% done; ETC: 12:13 (0:00:13 remaining)
Nmap scan report for 192.168.0.10
Host is up (0.00045s latency).
Not shown: 65506 closed tcp ports (reset)
PORT STATE SERVICE
53/tcp open domain
80/tcp open http
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
3389/tcp open ms-wbt-server
5985/tcp open wsman
5986/tcp open wsmans
9389/tcp open adws
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49669/tcp open unknown
49670/tcp open unknown
49671/tcp open unknown
49673/tcp open unknown
49676/tcp open unknown
49686/tcp open unknown
49698/tcp open unknown
49832/tcp open unknown
MAC Address: 08:00:27:2A:66:20 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.0.11
Host is up (0.00050s latency).
Not shown: 65508 closed tcp ports (reset)
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
3389/tcp open ms-wbt-server
5985/tcp open wsman
5986/tcp open wsmans
9389/tcp open adws
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49669/tcp open unknown
49671/tcp open unknown
49672/tcp open unknown
49675/tcp open unknown
49678/tcp open unknown
49701/tcp open unknown
49828/tcp open unknown
MAC Address: 08:00:27:2C:77:94 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.0.12
Host is up (0.00031s latency).
Not shown: 65508 closed tcp ports (reset)
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
3389/tcp open ms-wbt-server
5985/tcp open wsman
5986/tcp open wsmans
9389/tcp open adws
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49668/tcp open unknown
49669/tcp open unknown
49670/tcp open unknown
49671/tcp open unknown
49673/tcp open unknown
49676/tcp open unknown
49686/tcp open unknown
49852/tcp open unknown
MAC Address: 08:00:27:AC:2E:CA (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.0.22
Host is up (0.00062s latency).
Not shown: 65516 closed tcp ports (reset)
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
1433/tcp open ms-sql-s
3389/tcp open ms-wbt-server
5985/tcp open wsman
5986/tcp open wsmans
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49668/tcp open unknown
49680/tcp open unknown
49696/tcp open unknown
49698/tcp open unknown
49703/tcp open unknown
49797/tcp open unknown
MAC Address: 08:00:27:BB:04:43 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.0.23
Host is up (0.00057s latency).
Not shown: 65516 closed tcp ports (reset)
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
1433/tcp open ms-sql-s
3389/tcp open ms-wbt-server
5985/tcp open wsman
5986/tcp open wsmans
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49668/tcp open unknown
49669/tcp open unknown
49697/tcp open unknown
49785/tcp open unknown
49787/tcp open unknown
49857/tcp open unknown
49955/tcp open unknown
MAC Address: 08:00:27:A2:2A:C0 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
搭建成功.

Comments NOTHING